Phishing attacks have long been a primary tool for cybercriminals looking to steal sensitive data, from login credentials to financial information. However, the emergence of artificial intelligence (AI) is revolutionizing phishing strategies, making these attacks more sophisticated, targeted, and harder to detect. AI-powered phishing represents a new and dangerous phase in cybersecurity threats, enabling attackers to automate, personalize, and optimize their malicious campaigns on an unprecedented scale.
This blog examines how AI is reshaping phishing attacks, the risks posed to organizations and individuals, and the strategies to defend against these evolving threats.
How AI Powers Phishing Attacks:
AI is enhancing phishing attacks in several significant ways. Here's how it's transforming traditional tactics:

a) Personalized and Targeted Attacks
AI allows attackers to gather and analyze large amounts of publicly available information from social media profiles, company websites, etc. to create hyper-targeted phishing messages. Unlike traditional mass phishing campaigns, AI can tailor messages to individuals, making them appear more legitimate and increasing the chances of success.
Natural Language Processing (NLP): AI can generate phishing emails that sound increasingly convincing by mimicking a person’s tone, writing style, or specific vocabulary.
Impersonation via Deepfakes: AI-driven deepfake technology can create realistic fake audio or video messages, enabling cybercriminals to impersonate company executives or other trusted figures, tricking employees into complying with malicious requests.
b) Automation at Scale
AI enables cybercriminals to automate phishing campaigns, significantly increasing the volume and scale of attacks. Rather than manually creating phishing emails, AI systems can quickly generate thousands of customized emails, each with different content, making it more difficult for traditional detection systems to identify and block them.
Phishing Kit Generation: AI can automatically produce phishing kits—websites that replicate legitimate login pages, making it easier for attackers to harvest credentials.
Real-time Optimization: AI can also test different phishing tactics in real time, optimizing email content, subject lines, and URLs for maximum effectiveness.
c) Advanced Social Engineering
AI can refine social engineering tactics, exploiting human behavior more effectively. By analyzing patterns in employee actions, attackers can craft messages that manipulate individuals based on psychological triggers.
Psychological Targeting: AI tools can predict the best times to launch attacks based on behavioral patterns, such as when employees are under pressure or distracted.
Emotionally Manipulative Messaging: AI can craft emails that tap into emotions like urgency or fear, making it more likely that targets will act without thinking.
Impact of AI-Driven Phishing Attacks:
AI enables personalized, dynamic phishing content that closely mimics legitimate communication, making attacks harder to detect.
AI automates phishing campaigns, allowing cybercriminals to reach a large number of targets with customized messages.
AI enables highly targeted attacks on key individuals (e.g., executives), based on specific personal and professional details.
AI-powered attacks can evolve in real-time, bypassing traditional security systems and spam filters.
Defending Against AI-Enhanced Phishing:
To combat the growing threat of AI-enhanced phishing, organizations and individuals must adopt a multi-layered defense strategy that combines technology, training, and proactive monitoring. Here are several key defense measures:
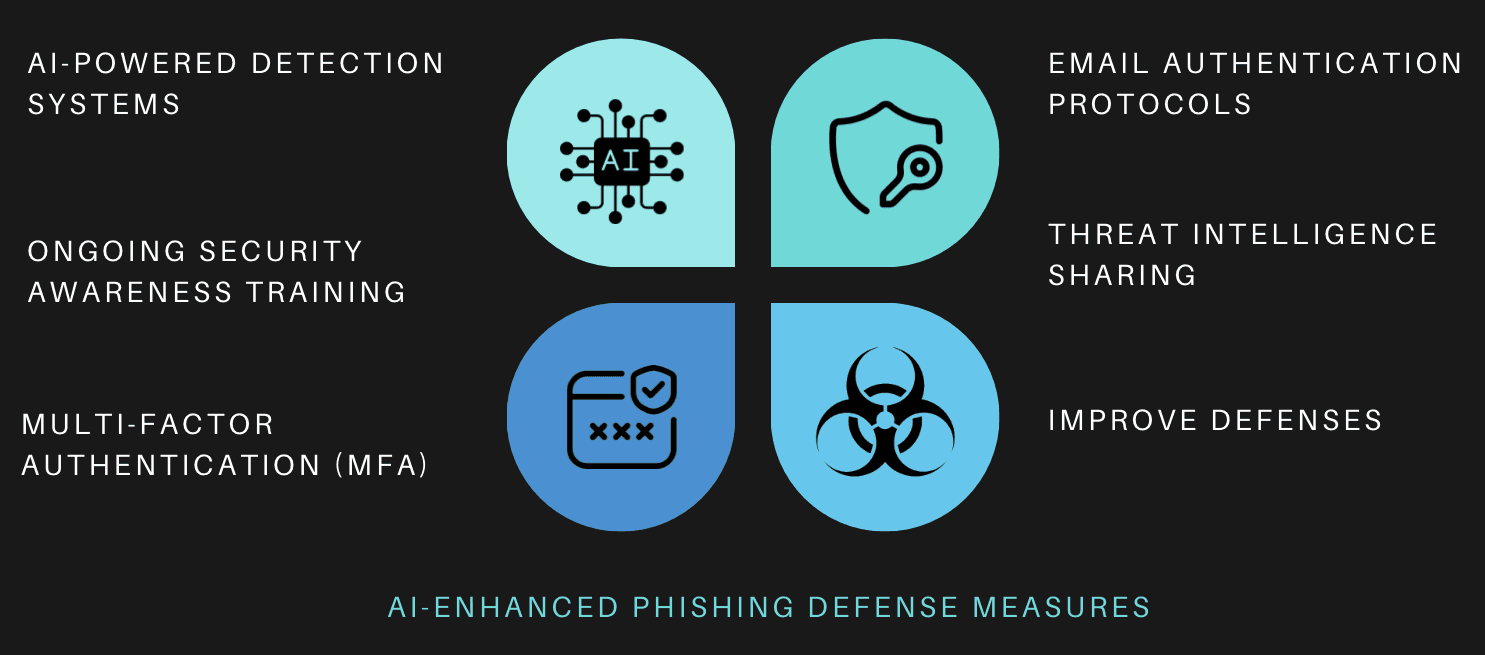
a) AI-Powered Detection Systems
Just as cybercriminals use AI for their attacks, organizations can deploy AI-driven tools to detect phishing attempts. These systems use machine learning to identify unusual email patterns, detect suspicious behavior, and flag potential phishing emails based on language anomalies, sender inconsistencies, and email metadata.
Behavioral Analytics: AI can help spot unusual behavior, such as abnormal login times or unauthorized data access, which may indicate a phishing attack in progress.
Advanced Email Filtering: AI can improve spam filters by continually learning from new phishing tactics, enhancing their ability to detect even novel phishing methods.
b) Ongoing Security Awareness Training
Human error remains one of the most common causes of successful phishing attacks. Security training programs should evolve to address more sophisticated AI-driven phishing tactics, teaching users to recognize subtle signs of phishing, even in highly personalized messages.
Simulated Phishing Drills: Regular phishing simulations can help employees spot AI-generated attacks and reduce the likelihood of falling victim.
Psychological Training: Employees should also be educated on how AI-based social engineering may exploit emotional triggers like fear or urgency, making them more vigilant in responding to suspicious requests.
c) Multi-Factor Authentication (MFA)
Implementing MFA provides an additional layer of security, even if an attacker successfully obtains a user’s login credentials. By requiring a second form of authentication such as a text message code or biometric scan MFA can stop attackers in their tracks even if they manage to steal login credentials.
d) Email Authentication Protocols
Organizations should implement email security protocols like SPF, DKIM, and DMARC, which help authenticate the legitimacy of incoming messages. These protocols reduce the risk of domain spoofing, which is often used in phishing attacks.
e) Threat Intelligence Sharing
Collaborating with external cybersecurity experts and threat intelligence platforms can provide early warnings about new phishing tactics. Sharing information about emerging phishing techniques allows organizations to stay ahead of attackers and improve defenses.
Conclusion:
AI is rapidly changing the landscape of phishing, making attacks more personalized, scalable, and difficult to detect. As cybercriminals adopt AI tools to optimize their phishing tactics, organizations must respond with equally advanced defenses, including AI-powered detection systems, security training, and multi-layered protection strategies. By understanding and preparing for AI-driven phishing, we can better safeguard sensitive data and mitigate the risks of these increasingly sophisticated cyber threats.
Happy Learning !!