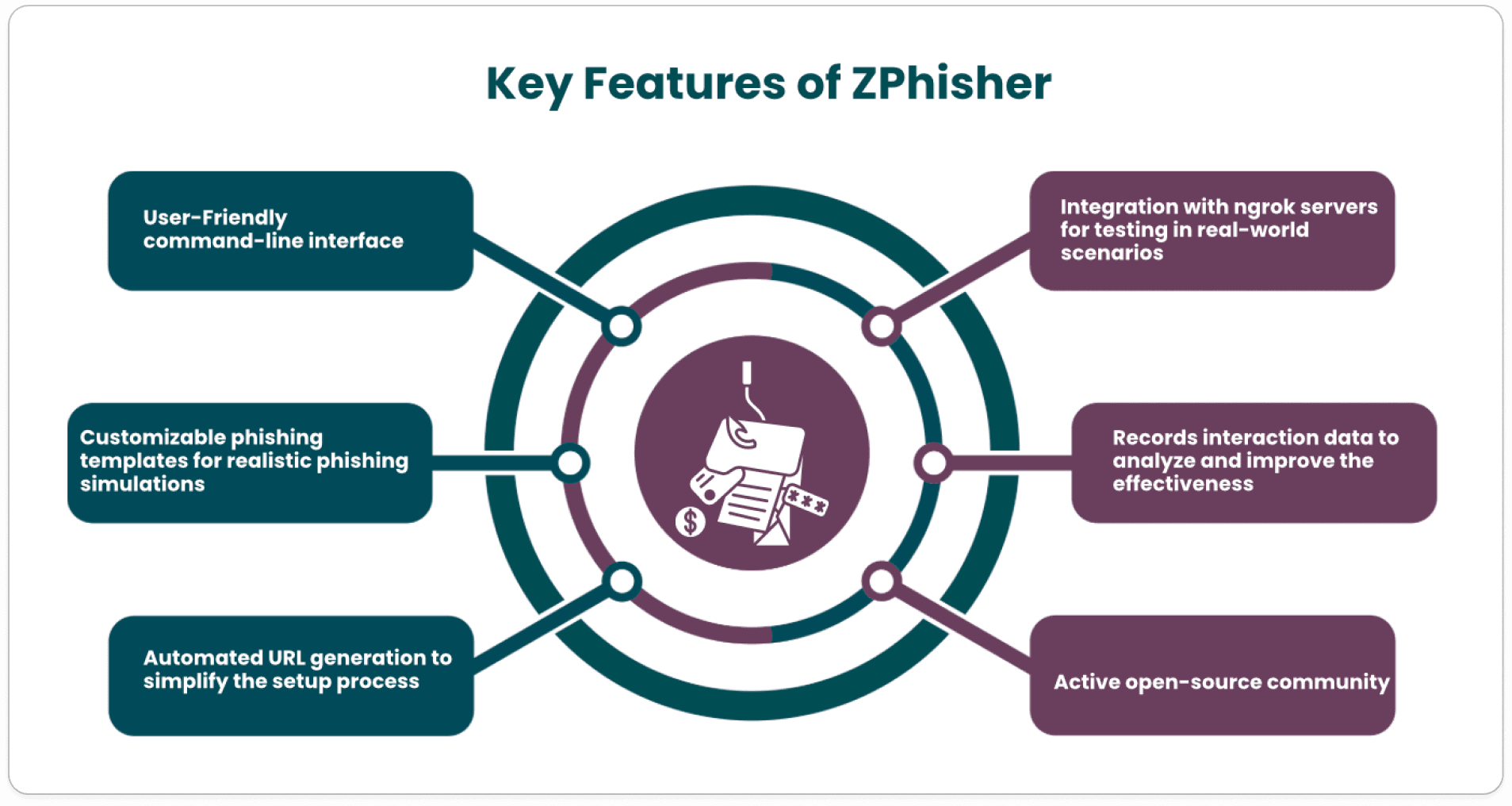
In today’s digital world, cybersecurity awareness is more crucial than ever. As phishing attacks become increasingly sophisticated, having tools to help security professionals understand and mitigate these threats is essential. One such tool is ZPhisher, an open-source phishing framework designed for ethical hacking that helps organizations strengthen their defenses against phishing attempts. In this blog, we’ll explore what ZPhisher is, its key features, and how it can be used responsibly for educational purposes.
What is ZPhisher?
ZPhisher is an open-source framework that simulates phishing attacks for educational and ethical hacking purposes. Unlike malicious phishing schemes aimed at stealing sensitive information, ZPhisher offers cybersecurity professionals and enthusiasts a platform to learn about phishing techniques, develop effective countermeasures, and enhance user awareness.
How to Install ZPhisher in Your Environment
Setting up ZPhisher is simple and can be completed in just a few steps. Here’s a guide to help you get started.
Prerequisites:
Before installation, ensure you have the following installed on your system:
Git: Required for cloning the repository.
PHP: Version 7.0 or higher.
Ngrok: Optional, but recommended for exposing your local server to the internet.
Step-by-Step Installation
Choose a Phishing Template: When the script runs, you’ll see a list of available phishing templates. Select the one you wish to use by entering the corresponding number.
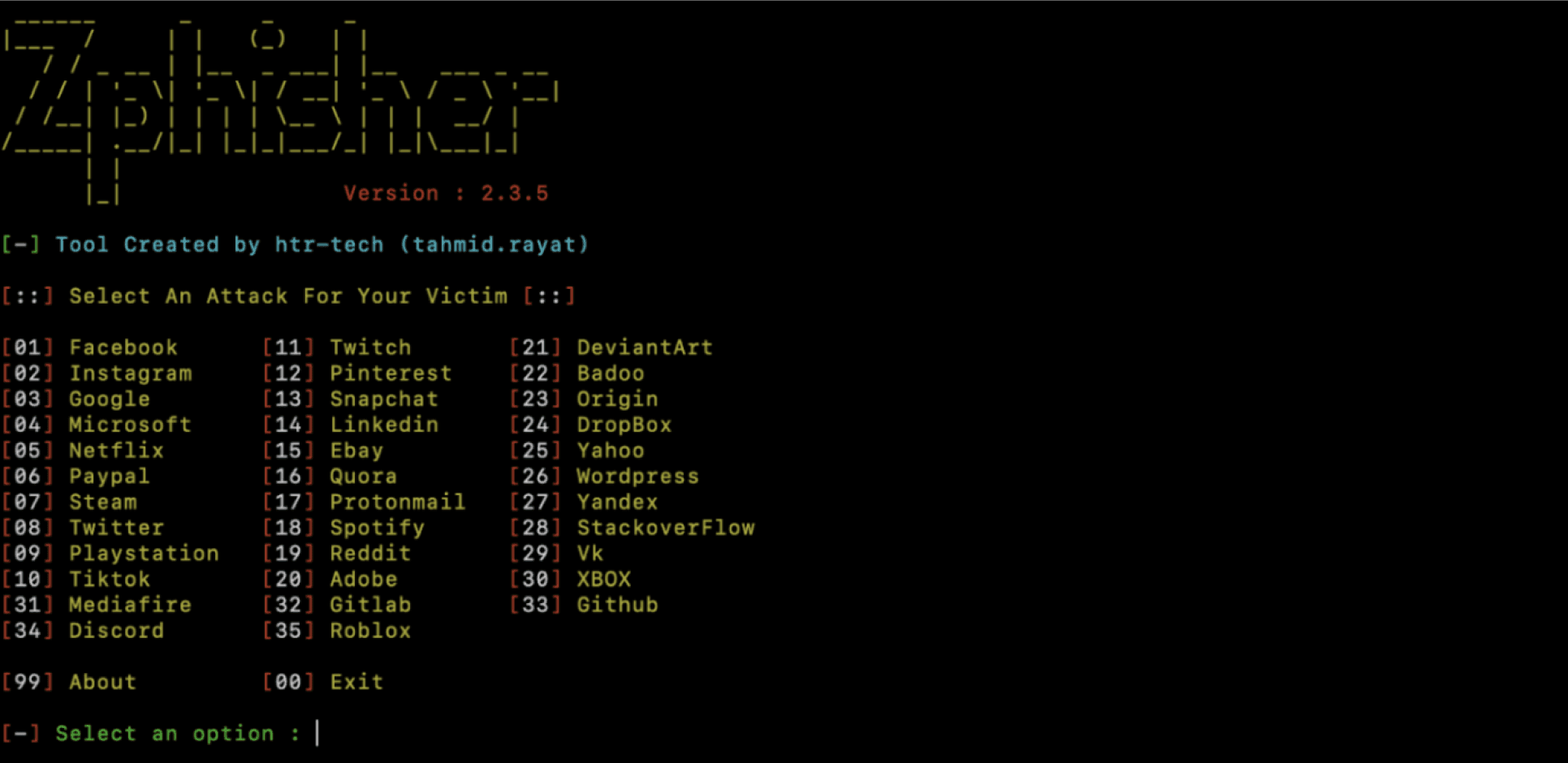
Select your preferred option to perform the attack.
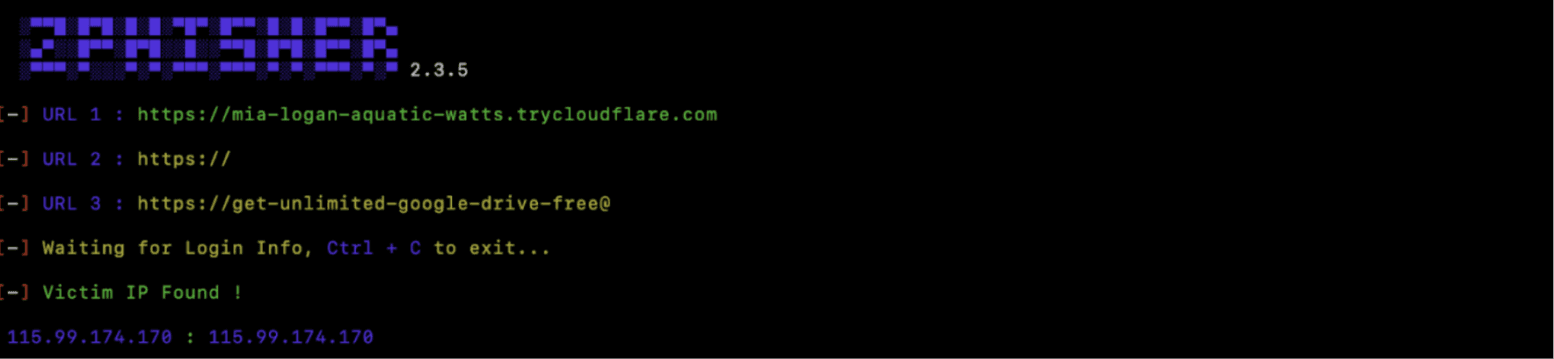
Once it’s launched, you’ll be able to view the captured account information, such as email addresses and passwords.
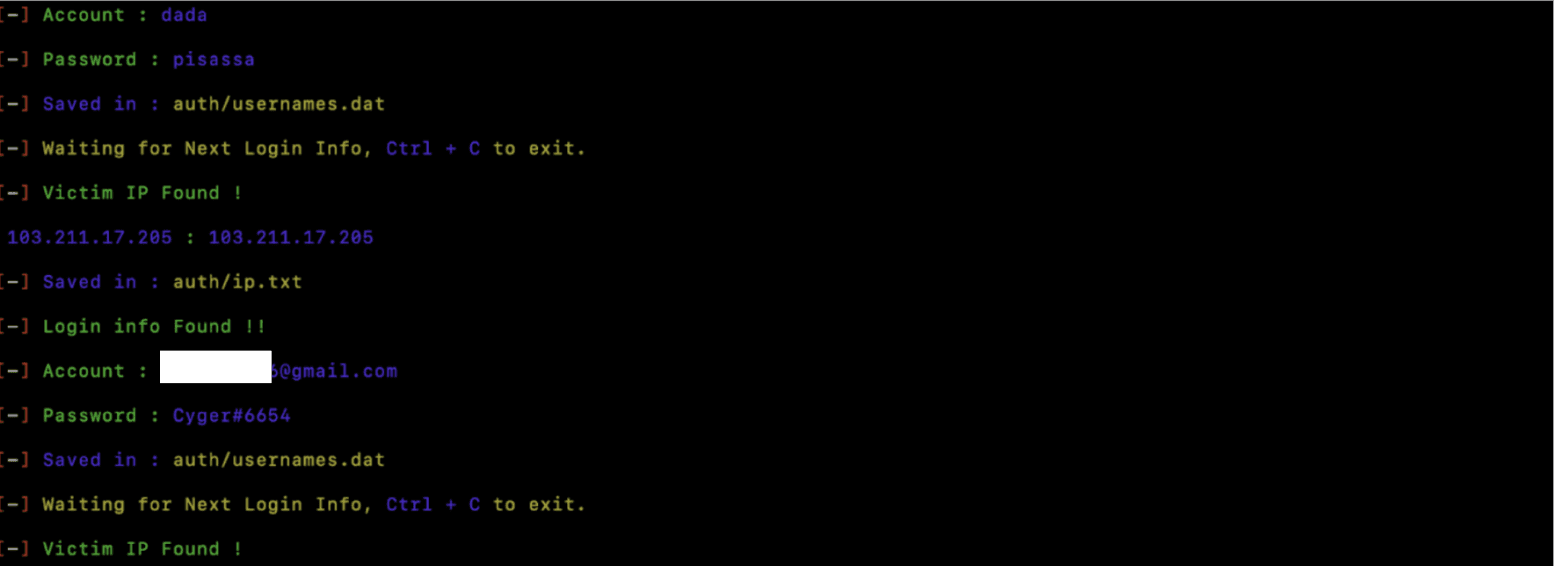
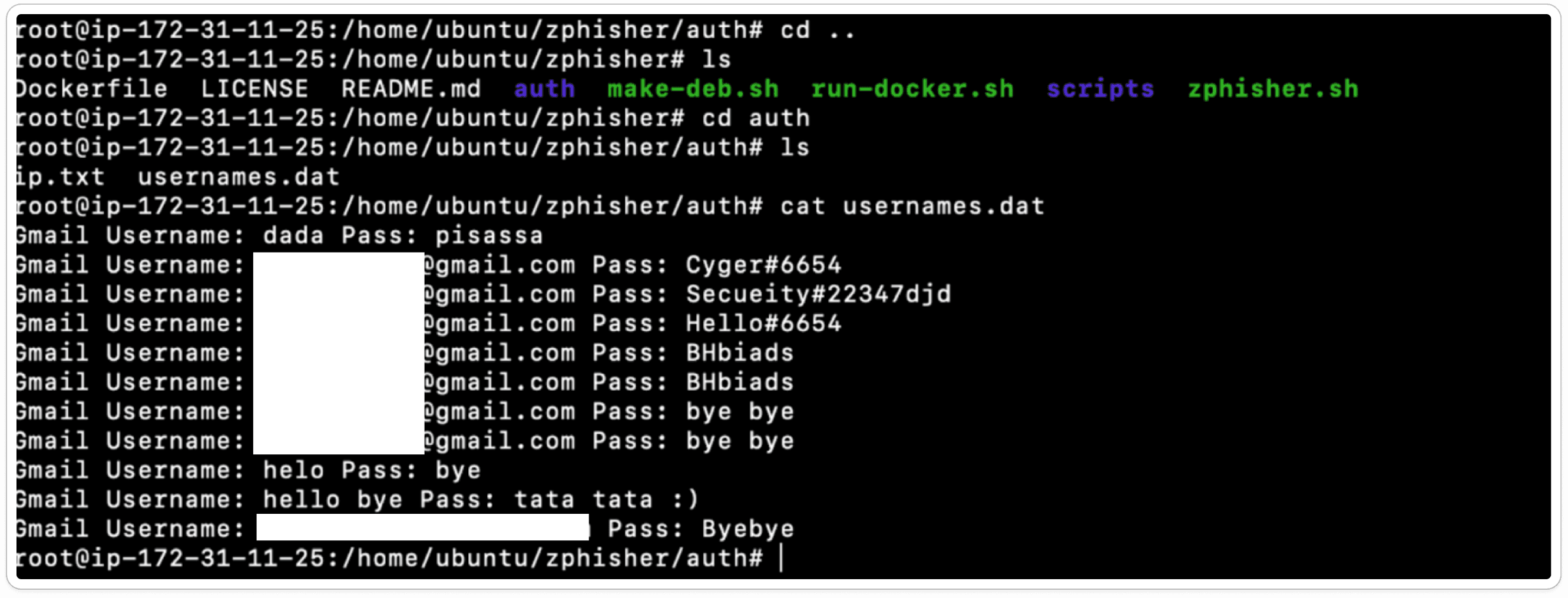
Here’s an interesting feature in ZPhisher: navigate to the auth folder to see a list of usernames along with their passwords.
Conclusion
ZPhisher is a robust and versatile open-source phishing framework that serves as an essential resource for both cybersecurity professionals and educators. By offering insights into phishing tactics, it enables organizations to bolster their defenses and raise user awareness about cybersecurity. It's crucial to use ZPhisher responsibly and ethically, ensuring that its capabilities contribute to a safer digital environment for all.
If you're aiming to deepen your understanding of phishing attacks or create effective cybersecurity training programs, ZPhisher is definitely worth exploring!
Happy Hunting !!


