XorBot is a form of malware primarily targeting Linux systems. Initially, it gained attention as part of a botnet operation, where infected machines were harnessed to carry out a variety of malicious activities, such as Distributed Denial of Service (DDoS) attacks, data theft, and more. XorBot uses a combination of sophisticated techniques to infiltrate systems, making it a significant threat to both home users and enterprise networks.
One of XorBot's most dangerous traits is its ability to operate stealthily over long periods, executing its payloads in the background without raising suspicion. It often exploits vulnerabilities in software and, more recently, has been observed using brute-force methods to crack weak or default passwords.
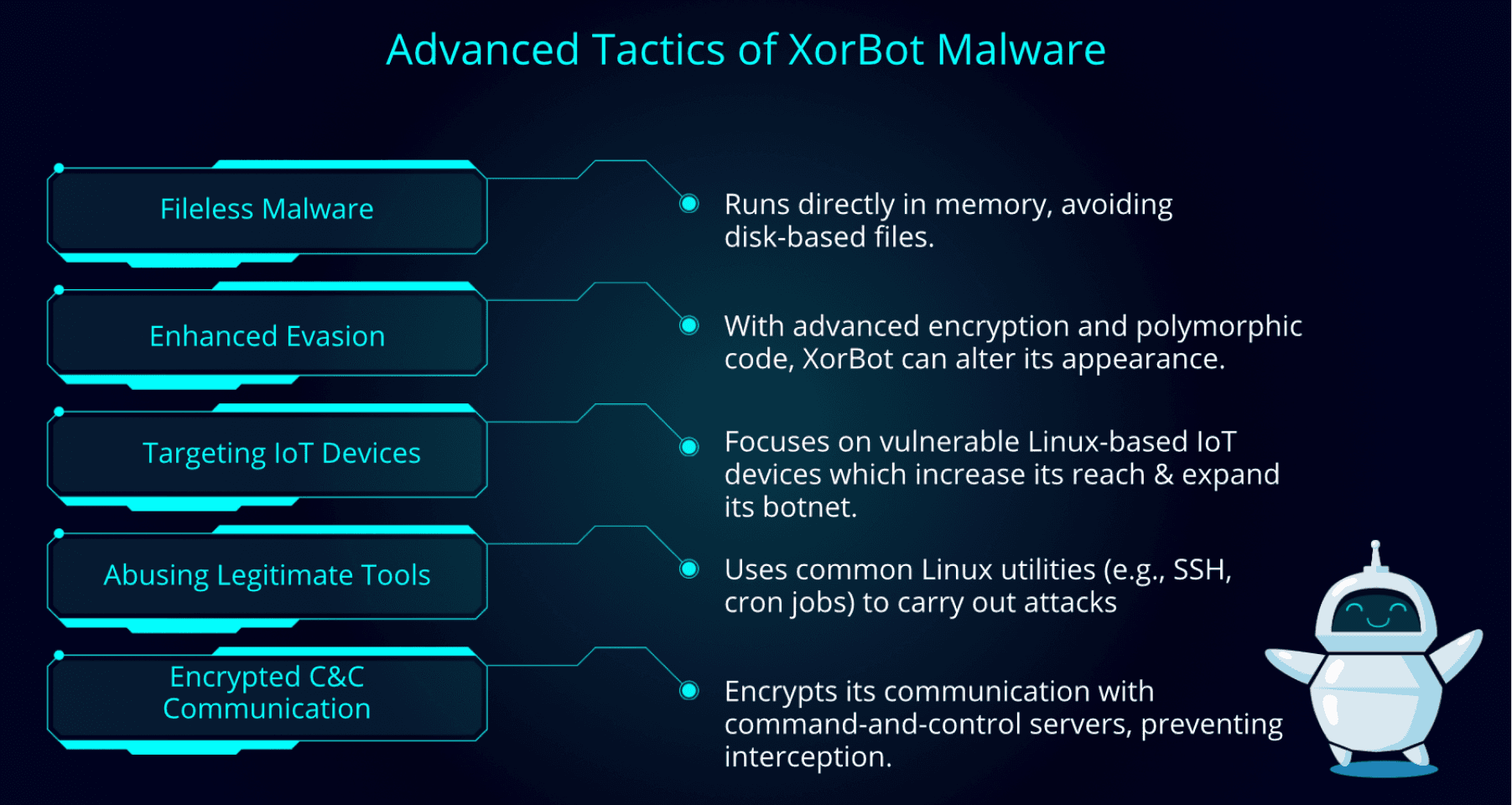
What's New? Advanced Tactics
XorBot’s return is marked by a shift towards more advanced and evasive tactics that makes it harder to detect, analyze, and eliminate. Some of the most notable updates to its behavior include:
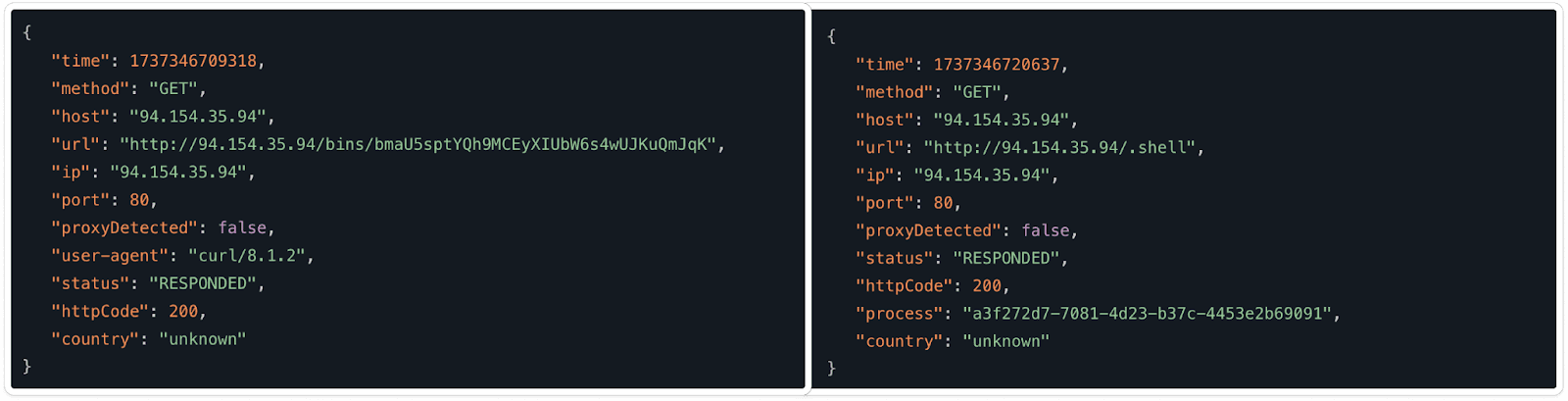
Malicious .sh Script:
Here, These scripts appears to download a malicious payload (bmaU5sptYQh9MCEyXIUbW6s4wUJKuQmJqK) and (weQ3YelZA6gjZi0VlAMIssgKlRbBhOW3oe) from a remote server, grants it executable permissions, executes it, and then removes the file to cover its tracks. While the exact purpose of the payload is setting up a backdoor and exfiltrating data to executing other harmful actions on the system.
Here’s the GET method in the .sh file, which retrieves the malware from their malicious domain.
AV Sandbox Results:
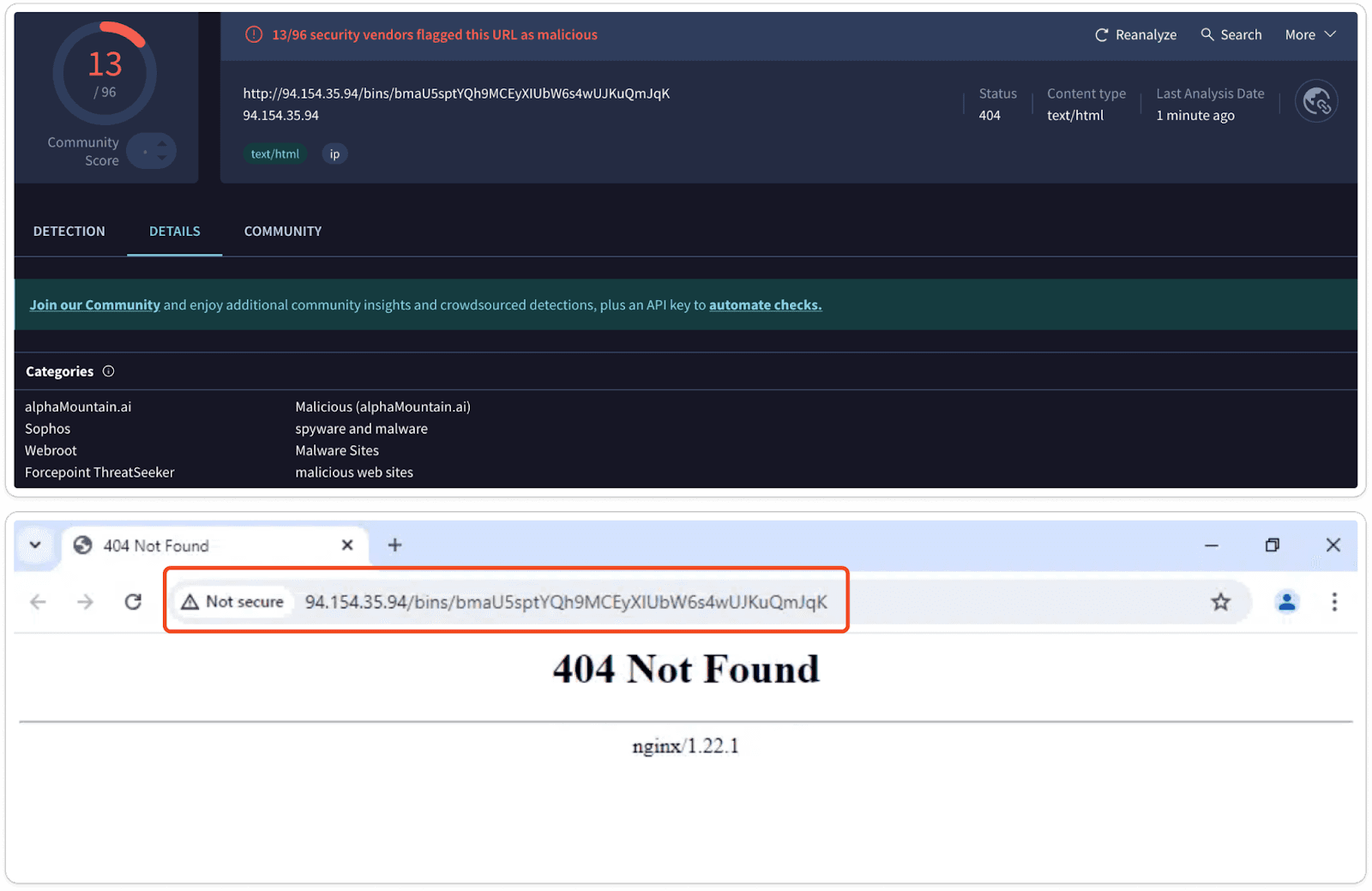
Conclusion:
XorBot campaign targets multiple system architectures (MIPS and x86_64) using a script that downloads, executes, and deletes malicious payloads from a remote server. The use of various download methods (wget, curl, busybox) ensures reliability, even if some tools are unavailable. The payloads likely install backdoors or steal sensitive data, and the removal of the downloaded files helps evade detection. By targeting both embedded and desktop systems, the campaign poses a serious risk. To defend against such threats, organizations should maintain strong endpoint protection, monitor network activity, and ensure regular security updates.
Happy Hunting !!