A .ppam file is a PowerPoint Add-in, used to enhance Microsoft PowerPoint by adding custom features, commands, and macros. It helps automate tasks and extends the program's functionality. While typically used to improve presentations, .ppam files can also be abused by attackers to execute malicious code. Therefore, they should be handled with caution, especially if received from untrusted sources.
File Details:
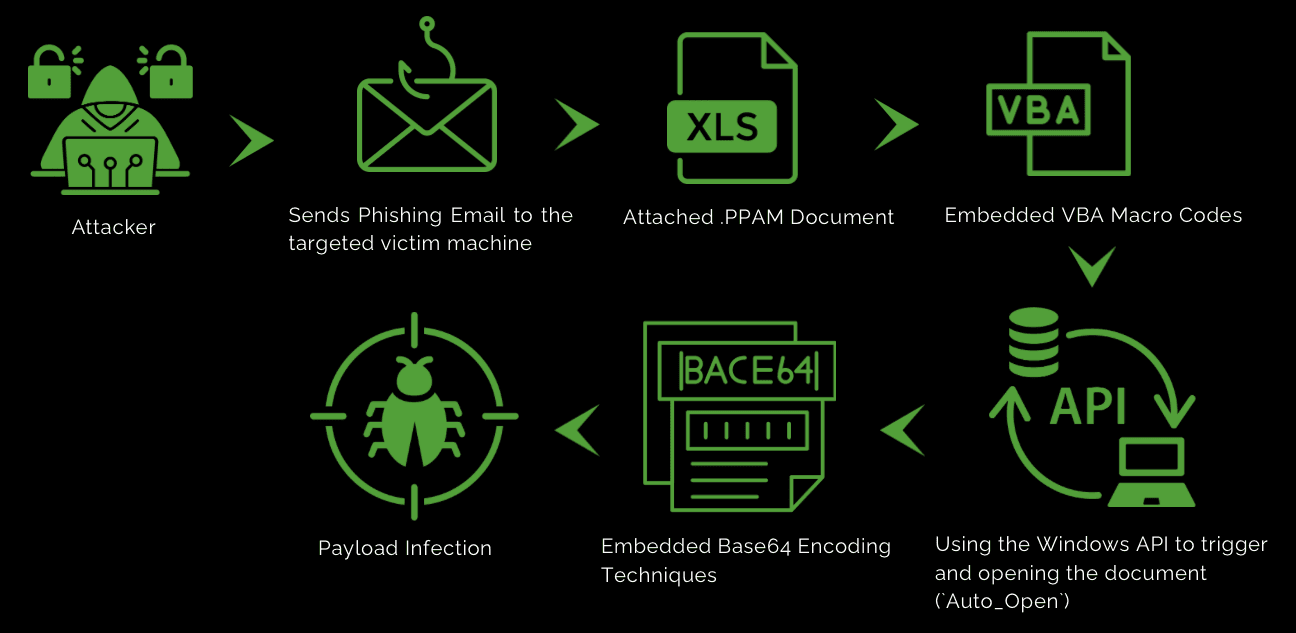
Infection Chain:
Technical Analysis of .PPAM Powerpoint Document:
To analyze a .ppam file, begin by extracting its contents. A .ppam file is a compressed archive, so unpacking it will reveal its internal structure, including any embedded files and folders.
After extraction, inspect the individual components, including embedded scripts, macros, and other resources. This review helps identify any malicious content or suspicious behavior within the add-in, such as obfuscated code, unusual macros, or unauthorized connections. A thorough examination of these elements is essential for understanding the .ppam file's functionality and assessing its potential security risks.
.PPAM Files and Folders:
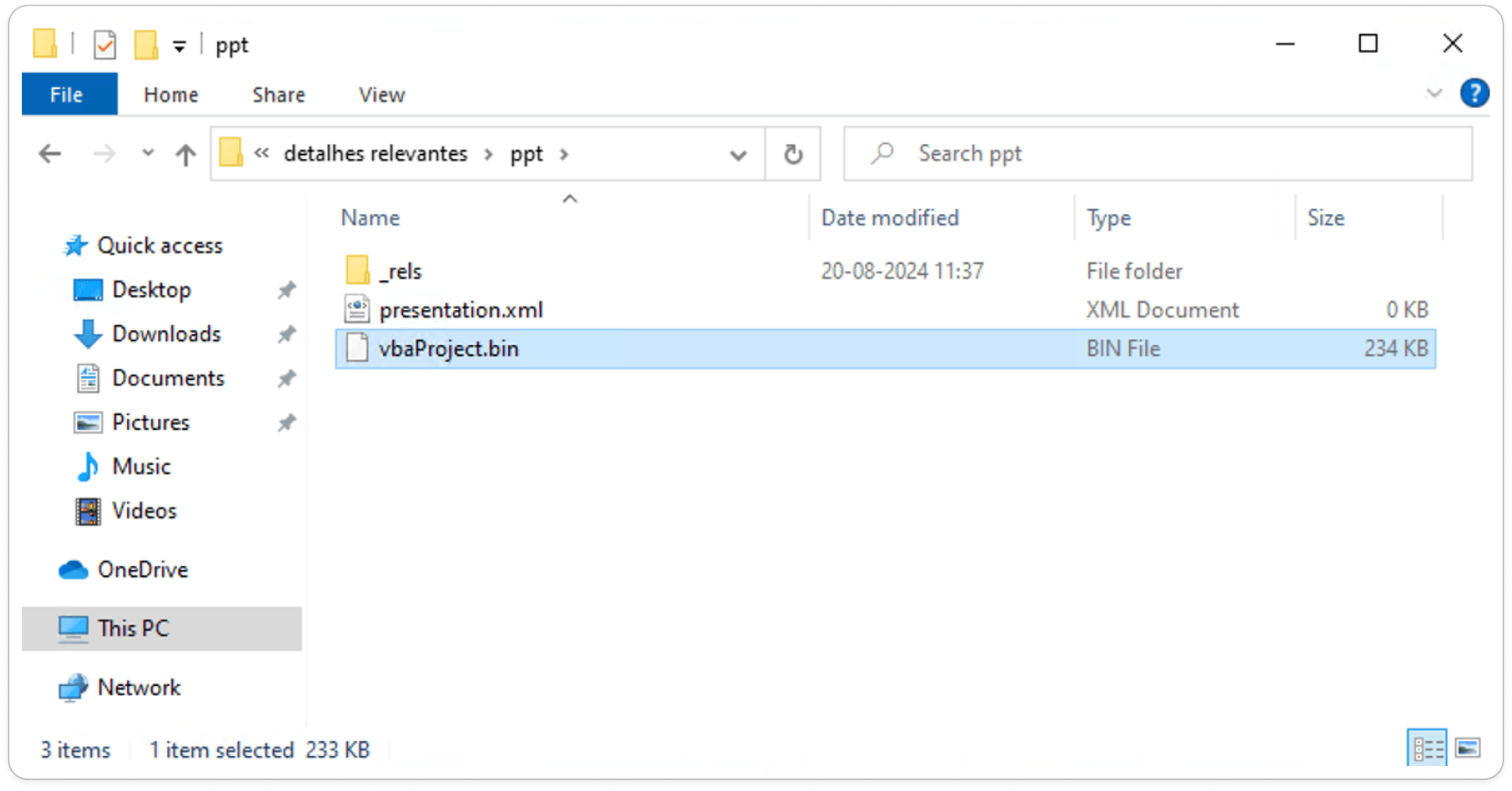
.PPAM vbaProject.bin:
The vbaProject.bin file within a .ppam file contains the Visual Basic for Applications (VBA) code used by the PowerPoint add-in. This binary file holds all the macros, functions, and scripts that enhance PowerPoint's functionality. It's a critical component to analyze, as it may include custom automation routines, user-defined functions, or potentially harmful code that could execute when the add-in is used. Reviewing this file is essential to understand the add-in's behavior and to identify any security risks.
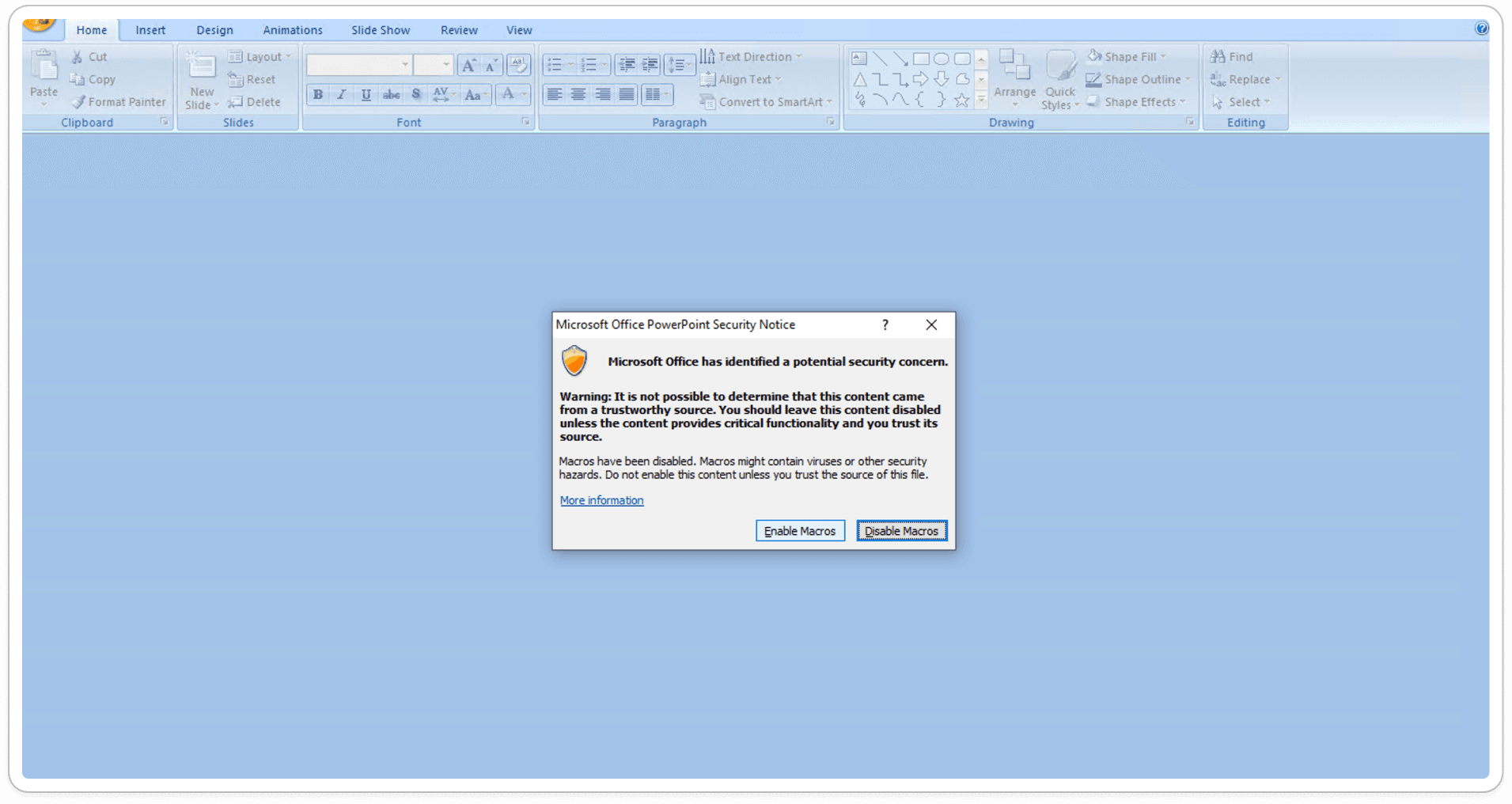
Macro Enabled Content:
Macro-enabled content in a .ppam file includes VBA scripts or macros embedded in the PowerPoint add-in. These macros enhance PowerPoint by automating tasks or adding custom features, but they can also be exploited to run malicious code, posing a security threat.
The \u00f6\u0192\u00ee\u00d5\u00b9 function processes each character of a string, subtracting a specific integer value from its ASCII code to update the string. This appears to be a simple character decryption method.
The \u00d9\u00f0\u00e5\u00bb\u00c8 function processes the string in pairs of characters, converting each pair to its hexadecimal equivalent and appending the corresponding character to a new string, functioning as a basic hexadecimal decoder.
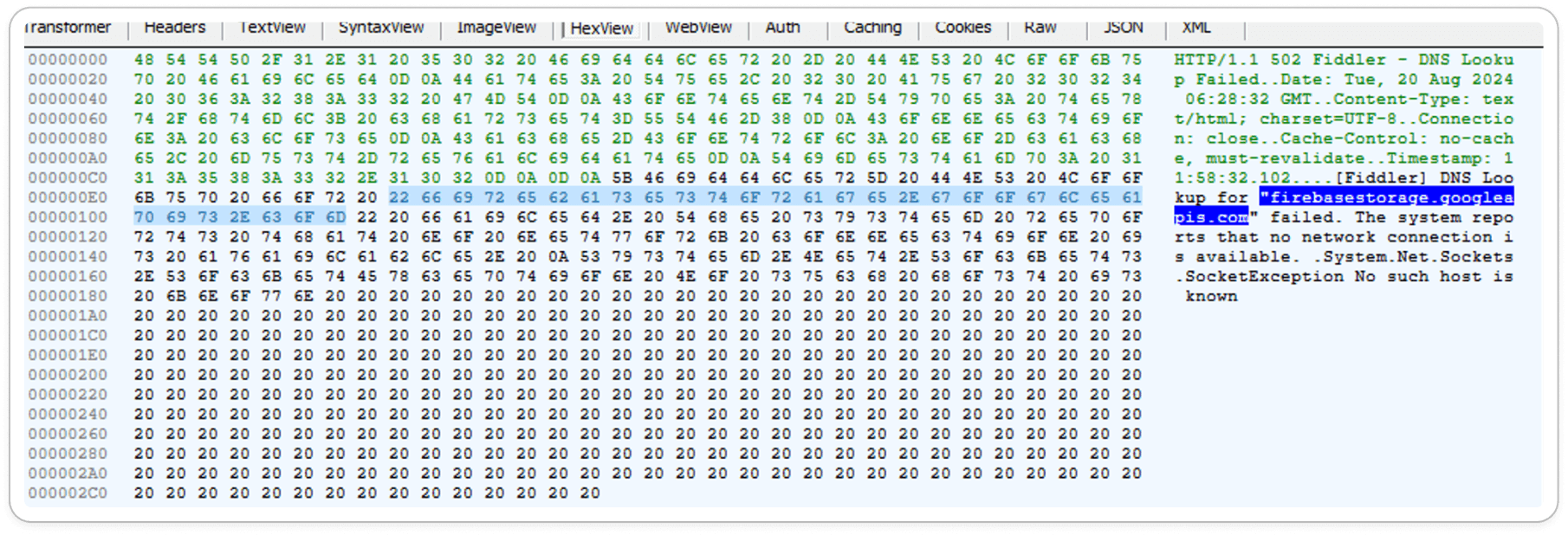
Obtained HTTP Packet Capture:
During dynamic analysis, we captured an HTTP response from the legitimate website firebasestorage[[.]]googleapis(.))com. Once the payload is executed, the final landing page is a lengthy URL, which is identified as potentially malicious.
In conclusion, the emergence of new TTPs for spreading malicious .PPAM PowerPoint documents highlights the growing sophistication of cyber threats. Attackers are leveraging these advanced techniques to hide harmful content within seemingly legitimate files, making detection more challenging. It is crucial to remain vigilant and implement strong security measures to effectively identify and counter these evolving threats.
Happy Hunting !!


