What is Malware Obfuscation?
Malware obfuscation is the process of making a program’s code difficult for both humans and computers to understand or detect, without altering the program's functionality. The objective is not merely to make the code unreadable, but to completely conceal the program’s presence.
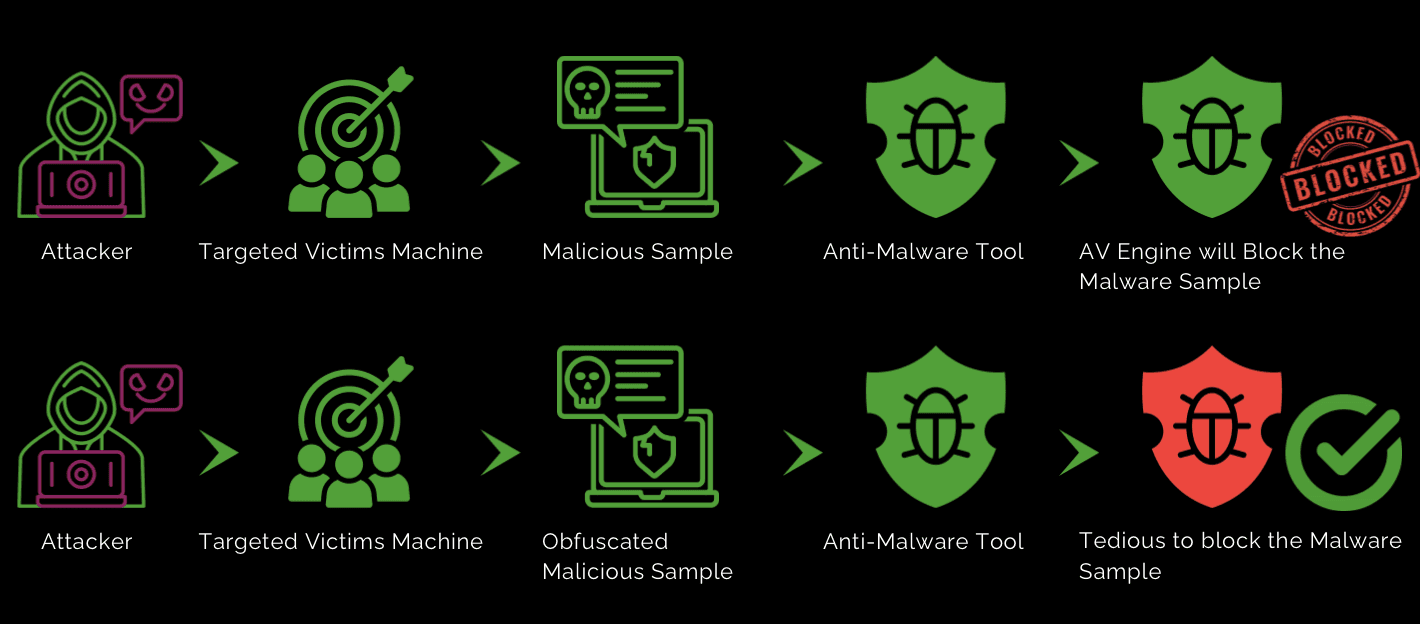
Attackers commonly use obfuscation techniques to hide the true nature of malicious code from security tools and analysts. By modifying or encrypting the code, they create challenges for antivirus programs and other security measures, making it harder to detect, analyze, and remove the threat. This often involves restructuring the code and employing various methods to mask the malware’s behavior and intent.
How does it work?
What are the most common Malware Obfuscation Techniques?
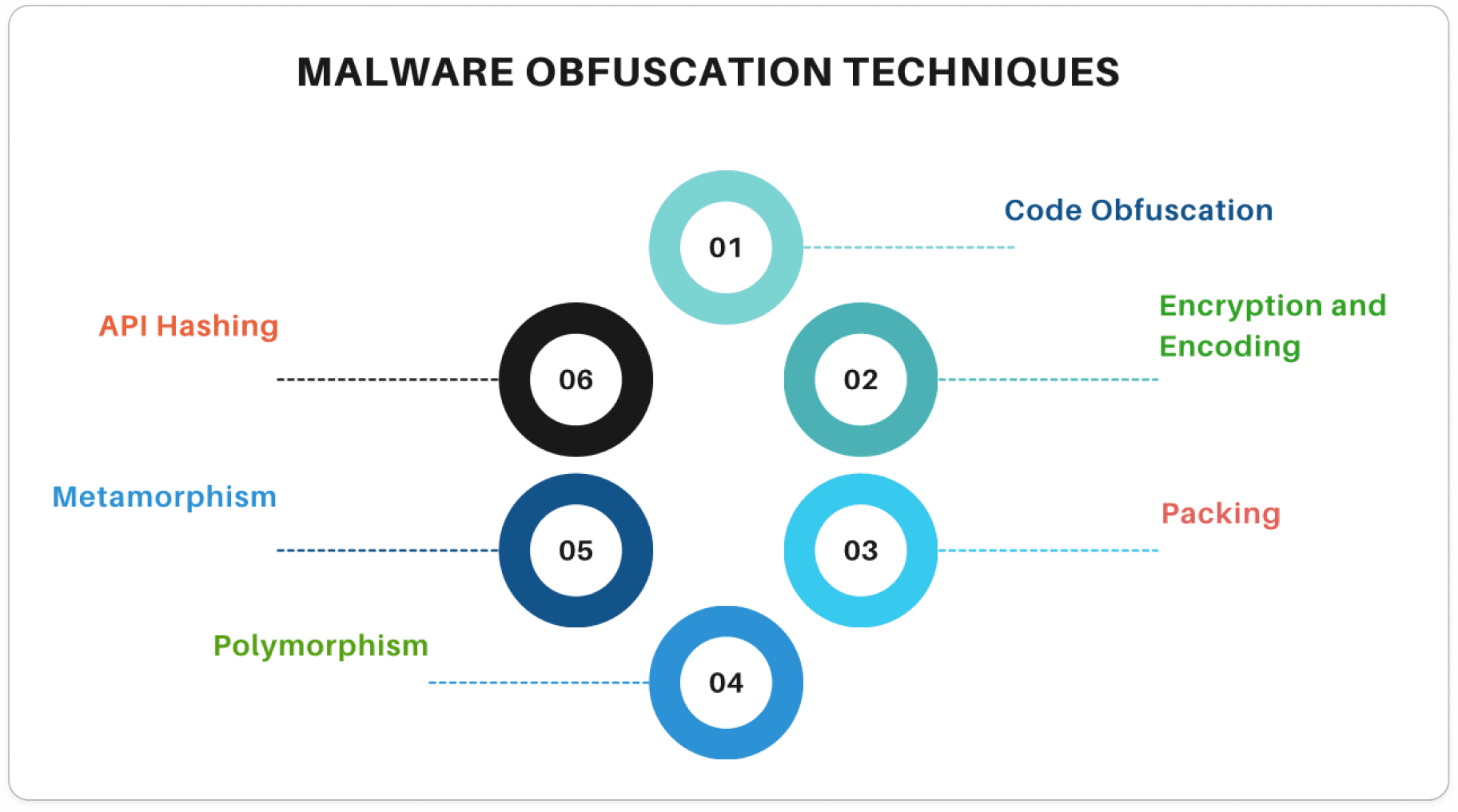
1. Code Obfuscation
Code Obfuscation is a technique involving altering the logical execution path of a program, making it difficult for analysts to understand the program's original flow.
Methodology:
Opaque Predicates: These are logical conditions that always evaluate to true or false but are used to obscure the flow.
Loop Transformation: Changing loop constructs to make them appear more complex, such as replacing simple loops with recursive functions.
2. Encryption and Encoding
Encryption is the process of converting Plain text into Cipher text.
Techniques:
Symmetric Encryption: Uses the same key for encryption and decryption, often embedding the key within the malware.
Asymmetric Encryption: Uses a pair of public and private keys, typically to secure communications or payloads.
On the other end, the malware uses encoding schemes to hide code or data, making it appear as harmless text.
Techniques:
Base64 Encoding: Converts binary data into ASCII text, masking its true intent.
Custom Encoding: Uses a proprietary encoding scheme to make detection and decoding more challenging.
3. Packing
A packer is a software tool that compresses the executable files, reducing their size and hiding their true contents. These are archive files (like ZIP or RAR) that include executable code to unpack themselves upon execution.
For Example:
When the packed file is executed, it decompresses or decrypts itself in memory, revealing the original code.
4. Polymorphism
Polymorphic Code that changes its appearance with each iteration or infection while retaining its core functionality. In general, it's embedded in the malware to dynamically alter the code using various encryption techniques with different keys for each iteration.
Why Polymorphism?
5. Metamorphism
Metamorphic code utilizes specialized engines to alter the entire structure and appearance of the malware each time it replicates or executes. By transforming its code with each iteration, metamorphic malware can completely change its signature. This dynamic modification makes it extremely challenging for signature-based detection systems to identify and track the malware.
Techniques:
Instruction Reordering: Changes the sequence of operations in the code.
Code Substitution: Uses different algorithms or logic to perform the same operations.
Register Renaming: Alters the register usage pattern, changing which registers are used for which operations.
6. API Hashing
API hashing is a technique used by malware to obscure its use of Windows API functions, complicating detection by security software. It stores hashed values of function names instead of the actual names, making signature-based detection more challenging. This technique makes static analysis and reverse engineering harder, as analysts must determine the hash algorithm to identify the functions.
At runtime, the malware resolves API addresses dynamically, evading security tools that monitor specific API patterns. Overall, API hashing enhances the stealthiness of malware by hiding its true functionality.
Obfuscation malware poses a major challenge in cybersecurity by concealing malicious intentions, making detection and analysis difficult. Understanding these techniques is essential for security professionals to strengthen defenses against evolving threats. To protect against obfuscated malware, it's crucial to keep security software updated, use robust intrusion detection systems, and educate users about safe online practices. Staying vigilant and informed helps defend against this sophisticated threat.
Happy Learning !!