In general, BloodHound is a powerful tool for red teaming exercises aimed at evaluating and enhancing the security of Active Directory (AD) environments.
How does it work?
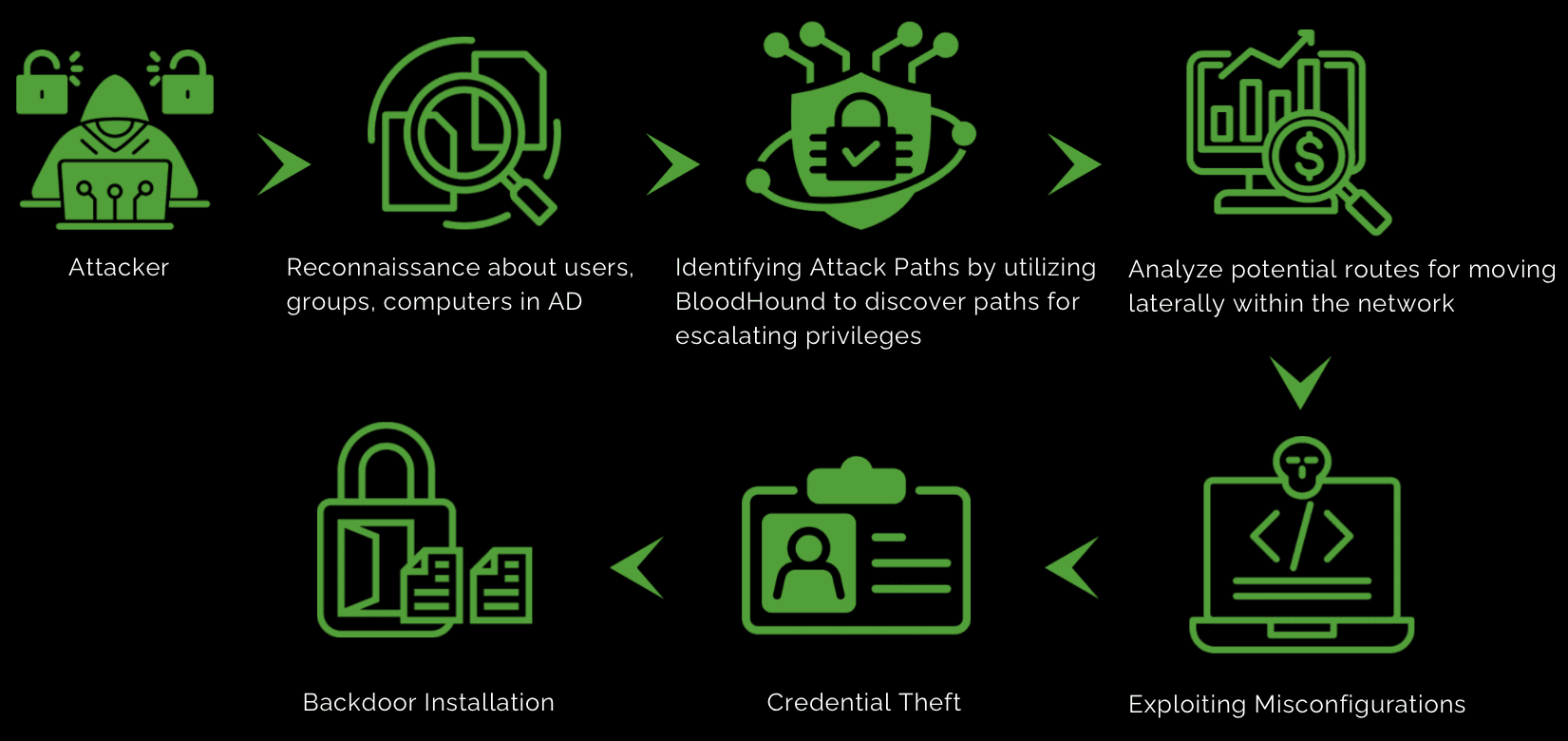
By using BloodHound, malware authors can identify and exploit weaknesses within an Active Directory (AD) environment. Here's the detailed breakdown:
Reconnaissance
Data Collection: Attackers, like ethical red teamers, can use BloodHound's SharpHound tool to gather extensive data about the AD environment.
Enumeration: They collect information about users, groups, computers, trusts, sessions, and permissions within the AD.
Identifying Attack Paths
Privilege Escalation: Attackers utilize BloodHound to discover paths for escalating privileges, pinpointing accounts with high privileges that can be compromised.
Lateral Movement: They analyze potential routes for moving laterally within the network to access more valuable targets or critical systems.
Exploiting Misconfigurations
Weak Permissions: BloodHound aids attackers in identifying weak permissions and misconfigurations that can be exploited for unauthorized access.
Credential Theft: By recognizing privileged accounts and their associated systems, attackers can target these accounts to steal credentials.
Persistence
Backdoor Installation: Attackers use the insights from BloodHound to locate systems where they can establish persistent backdoors without detection.
Defense Evasion: They gain a comprehensive understanding of the network layout, helping them avoid detection by security tools and maintain long-term access.
How to mitigate BloodHound exploitation?
Assign minimal permissions to users and services to limit potential attack paths.
Enforce multi-factor authentication (MFA) and use dedicated access methods for privileged accounts.
Monitor for suspicious activities, such as attempts at privilege escalation.
Regularly review and tighten permissions for service accounts.
Deploy honeypots or use detection tools like BloodHound to identify malicious activities.
Useful Event IDs to Detect BloodHound Exploitation:
To conclude, it is crucial to actively monitor for BloodHound exploitation by proactively detecting suspicious activities and utilizing key Event IDs. This approach is vital for safeguarding Active Directory environments from sophisticated cyber threats.
Happy Learning !!