A brute force attack is a method of cyber attack that relies on trial and error to guess passwords, encryption keys, or other sensitive data. In this process, the attacker systematically tries different combinations of characters until they find the correct one. The approach is straightforward: test all possible combinations until access is granted.
The term "brute force" refers to the use of raw computational power to "force" entry into a system. This type of attack doesn't rely on exploiting vulnerabilities or using advanced techniques; instead, it depends on the sheer time and computational resources required to attempt numerous combinations.
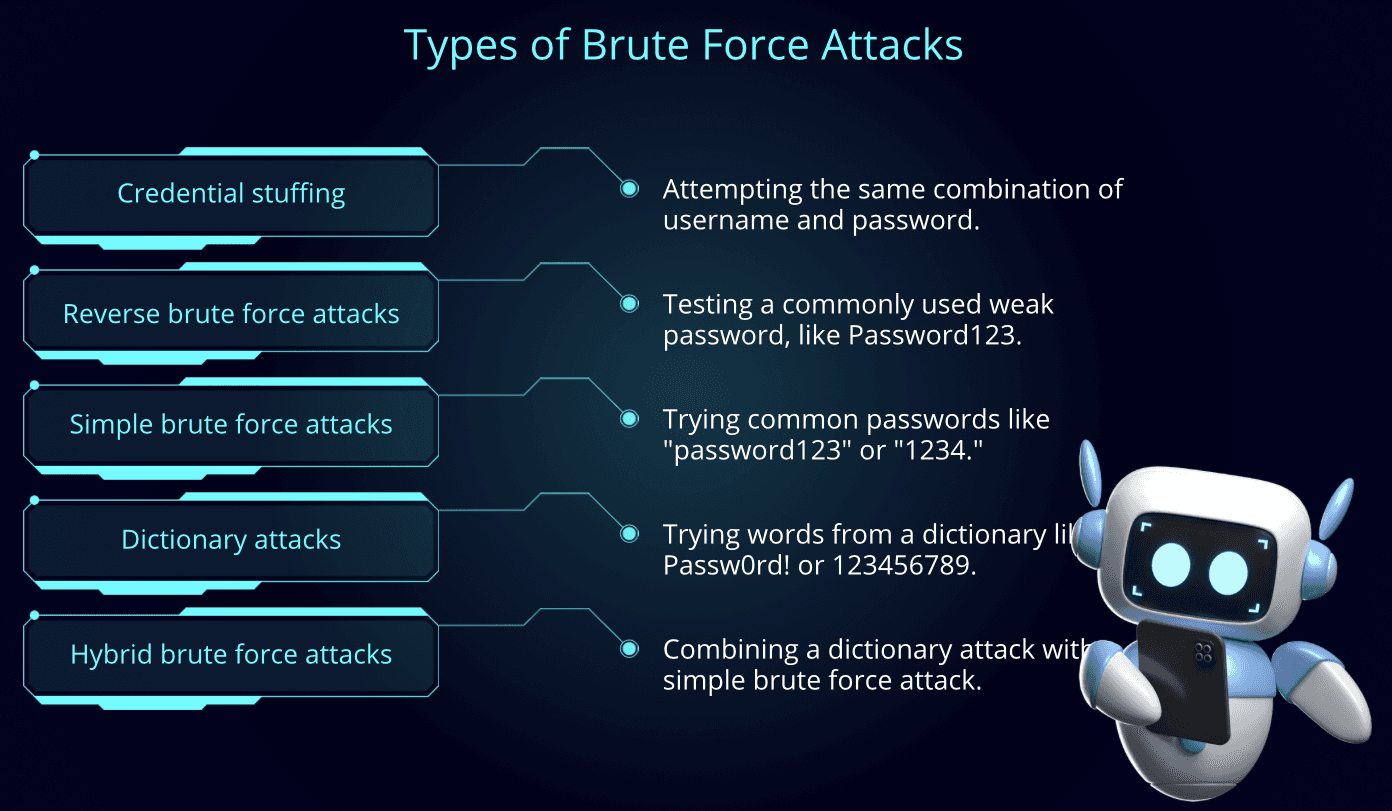
Types of Brute Force Attacks:
Brute force attacks can manifest in different ways, depending on the target and the security measures in place. Below are some common types of brute force attacks:
How Brute Force Attacks Work?
When carrying out a brute force attack, an attacker typically follows these steps:
Target Identification: The attacker begins by identifying the target. This could be a user account, a website, a server, or even an encrypted file.
Input of Possible Combinations: The attacker then uses a specialized tool or script to start testing various password combinations. These automated programs can attempt thousands, or even millions, of combinations per second.
Trial and Error: The attacker continues testing different combinations in a trial-and-error fashion until the correct password is found. Depending on the password's complexity such as its length and character variety the process could take anywhere from a few seconds to several years.
Access Gained: Once the correct password is discovered, the attacker gains unauthorized access to the target system, account, or data.
Conclusion:
While brute force attacks might appear to be a straightforward and basic hacking technique, they continue to pose a significant threat due to their simplicity and the widespread use of weak passwords. By understanding how these attacks work and taking proactive measures to protect your accounts and systems, you can greatly reduce the risk of falling victim.
Using strong, unique passwords, enabling multi-factor authentication, and adopting other security best practices are key steps in safeguarding your online presence and minimizing your exposure to brute force attacks. With the right precautions, you can stay one step ahead of attackers and secure your digital life.
Happy Reading !!


