A DCShadow attack (referring to T1207) is a technique employed by advanced persistent threats (APTs) to compromise Active Directory (AD) environments. In this attack, the attacker registers a rogue Domain Controller (DC) to replicate malicious changes into the AD, thereby injecting arbitrary data into the domain. This can result in serious consequences such as privilege escalation, persistence, and complete domain compromise. The attack necessitates that the attacker has already compromised a high-privilege account, such as a Domain Admin or Enterprise Admin.
Attack Flow:
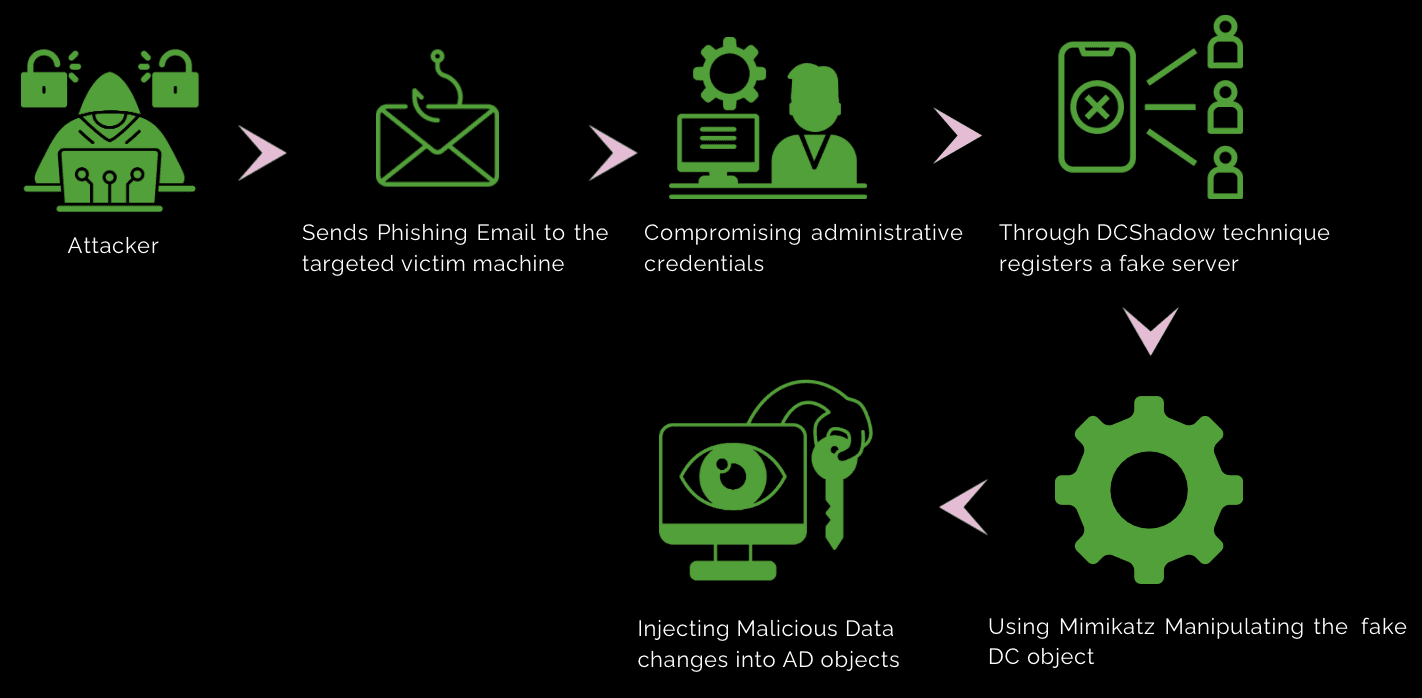
How does it work?
The DCShadow attack is an advanced method for manipulating Active Directory (AD) domain controllers (DCs) by injecting fraudulent replication data. Here’s a breakdown of how it works:
Compromise and Persistence:
Attackers initially compromise a domain-joined machine or obtain administrative credentials within the domain to establish persistence and gain control.
Registering as a Replica:
The attacker registers a rogue server as a domain controller replica using the DCShadow technique. This involves creating a fake DC object in AD that mimics a legitimate domain controller.
Manipulating Replication:
Using the fake DC object, the attacker induces legitimate DCs in the domain to replicate AD data to the rogue server. This manipulation is achieved by altering attributes and metadata associated with the rogue DC object to appear genuine.
Injecting Malicious Data:
During replication, the attacker can inject malicious changes into AD objects. These modifications may include creating unauthorized accounts, adjusting permissions, modifying group memberships, or introducing new objects to facilitate further compromise.
Stealth Operations:
DCShadow operates discreetly to evade detection by security monitoring tools designed to detect unusual replication activities. The rogue DC masquerades as legitimate to both other DCs and AD management tools.
Impact:
Successful execution of DCShadow grants the attacker unauthorized control over AD objects, compromising the domain's integrity and security. This can result in persistent unauthorized access, data exfiltration, privilege escalation, and other malicious actions.
How do attackers perform a DCShadow attack?
DCShadow, a feature in Mimikatz's lsadump module (lsadump::dcsync), allows for the creation of rogue domain controllers to push changes to Active Directory. Executing a DCShadow attack with Mimikatz involves two primary steps:
Basically, lsadump is used for dumping the Windows Security Account Manager (SAM) database and Local Security Authority (LSA), which contain NT and LM hashes of user accounts.
Compromising Credentials:
Attackers first compromise domain-joined machines or obtain administrative credentials to gain necessary privileges.
.\mimikatz.exe - Runs the Mimikatz executable from the current directory.
!+ - Command to enable a debugging mode or additional output.
!ProcessToken - This is a command within Mimikatz used to interact with process tokens, which are used for various privilege escalation techniques.
Manipulating Replication:
Using the compromised credentials, attackers register a rogue server as a domain controller replica and manipulate AD replication to inject malicious changes.
lsadump - This module in Mimikatz is used for dumping information from the Local Security Authority (LSA) or Security Account Manager (SAM).
dcshadow - This specific command within the lsadump module initiates the DCShadow attack, which involves creating rogue domain controllers to manipulate Active Directory replication and push unauthorized changes.
/push - This option specifies that the rogue changes should be pushed to the legitimate domain controllers, effectively injecting the malicious modifications into the Active Directory.
Useful Event IDs to detect the DCShadow Attack:
In conclusion, The DCShadow attack allows attackers to stealthily manipulate Active Directory by using rogue domain controllers, leading to unauthorized access and control. Mitigating this risk requires stringent monitoring, limiting administrative privileges, regular audits, and advanced anomaly detection to maintain AD security.
Happy Learning !!


