A DCSync attack is a technique where an attacker simulates the behavior of a domain controller (DC) to obtain password data through domain replication. This method allows the attacker to request sensitive information, such as user credentials and password hashes, from other domain controllers within the network.
By exploiting legitimate functions of the Active Directory (AD) infrastructure, DCSync attacks are challenging to detect and prevent. A common goal of DCSync is to retrieve the KRBTGT hash, which can then be used to create Golden Tickets, enabling persistent and undetectable access to the AD environment.
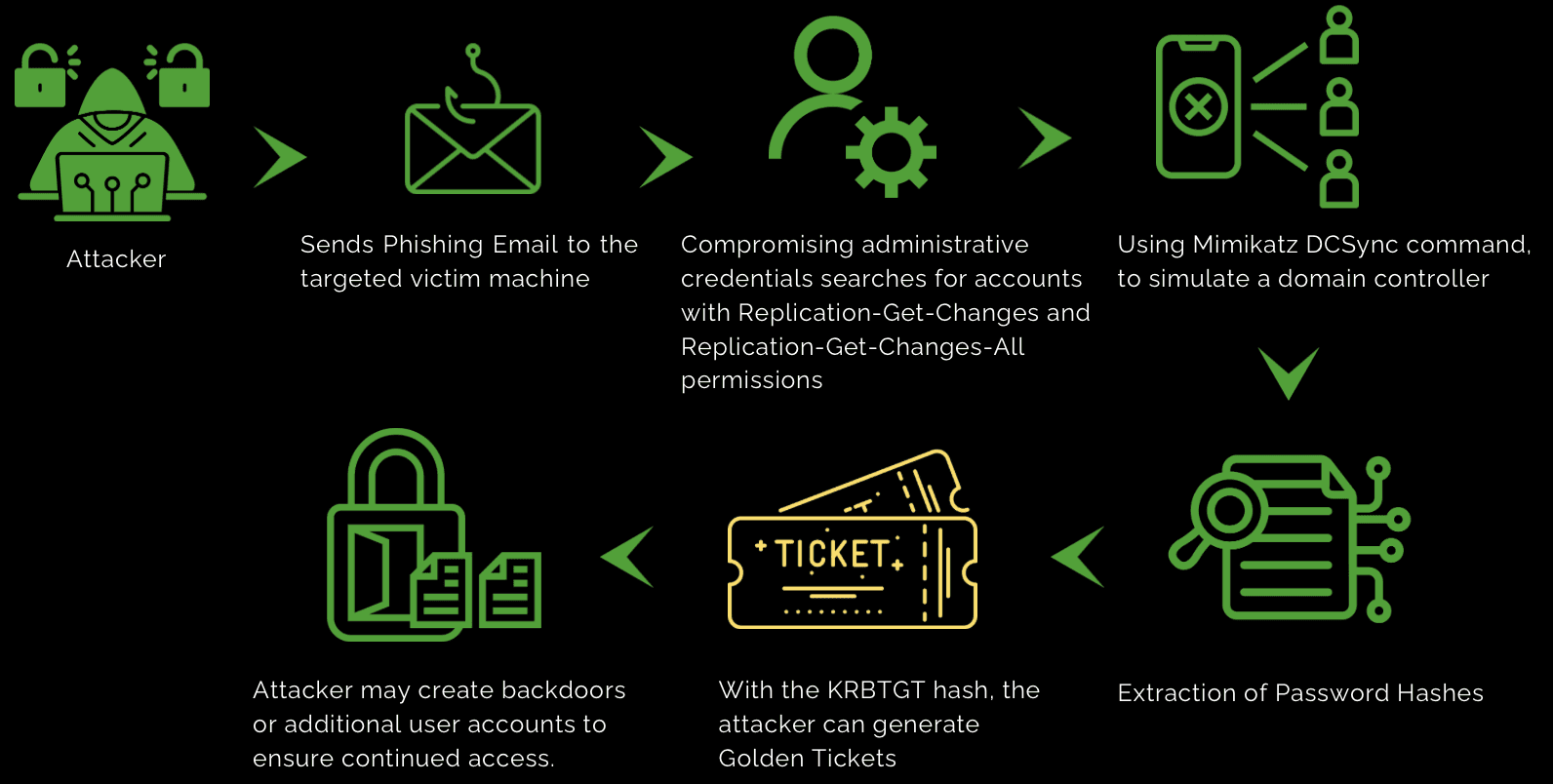
Attack Flow:
How does it work?
A DCSync attack involves simulating a domain controller (DC) to extract sensitive information from other DCs via domain replication. Here’s how it works:
Initial Compromise:
Network Access: The attacker gains initial access to the network, often through phishing, malware, or exploiting vulnerabilities.
Privilege Escalation: They escalate privileges to obtain administrative or domain-level access.
Credential Theft:
Account Search: Using the obtained privileges, the attacker searches for accounts with Replication-Get-Changes and Replication-Get-Changes-All permissions, typically domain admin or equivalent accounts.
Mimikatz Usage:
Tool Deployment: The attacker employs the open-source tool Mimikatz, specifically the DCSync command, to simulate a domain controller.
Replication Request: Commands in the Directory Replication Service Remote Protocol (MS-DRSR) are used to request replication data from legitimate domain controllers.
Data Extraction:
Password Hashes: The attacker extracts password hashes, including those of sensitive accounts such as KRBTGT, domain admins, and service accounts.
Persistent Access: This information is used to further infiltrate the network or maintain persistent access.
Exploitation:
Golden Tickets: With the KRBTGT hash, the attacker can generate Golden Tickets, granting indefinite access to the domain.
Lateral Movement: They can move laterally within the network, exfiltrate data, or carry out further attacks.
Maintaining Access:
Backdoors and Accounts: The attacker may create backdoors or additional user accounts to ensure continued access.
Evasion Tactics: They might disable security mechanisms or clear logs to avoid detection.
Useful Event IDs to Detect DCSync Attacks:
In summary, A DCSync attack exploits domain controller replication to extract sensitive data by impersonating a legitimate DC. This enables persistent, covert access to network resources, highlighting the critical need for robust monitoring, stringent access controls, and comprehensive security measures to safeguard Active Directory environments effectively.
Happy Learning !!


