A pass-the-ticket attack in a Windows Active Directory environment involves stealing or forging authentication tickets generated during user logins. These tickets contain user identity and access privileges, granting access to network resources like files and applications. Attackers exploit this by reusing stolen or forged tickets to gain unauthorized access without needing to authenticate again. This method allows them to move laterally across the network, access sensitive data, and potentially take control of systems, posing significant security risks to organizational networks.
How does it work?
In Windows domain environments using Kerberos authentication, upon a user's login, the Kerberos protocol generates a Ticket Granting Ticket (TGT). This TGT enables users to request Service Tickets (TGS) without needing to re-enter their credentials, facilitating access to specific network resources such as files and applications. In the context of a Pass-the-Ticket (PtT) attack, attackers exploit vulnerabilities or use tools to steal TGTs or TGSs from memory or network traffic. Alternatively, they may forge counterfeit tickets that mimic valid ones, allowing them to gain unauthorized access to network resources.
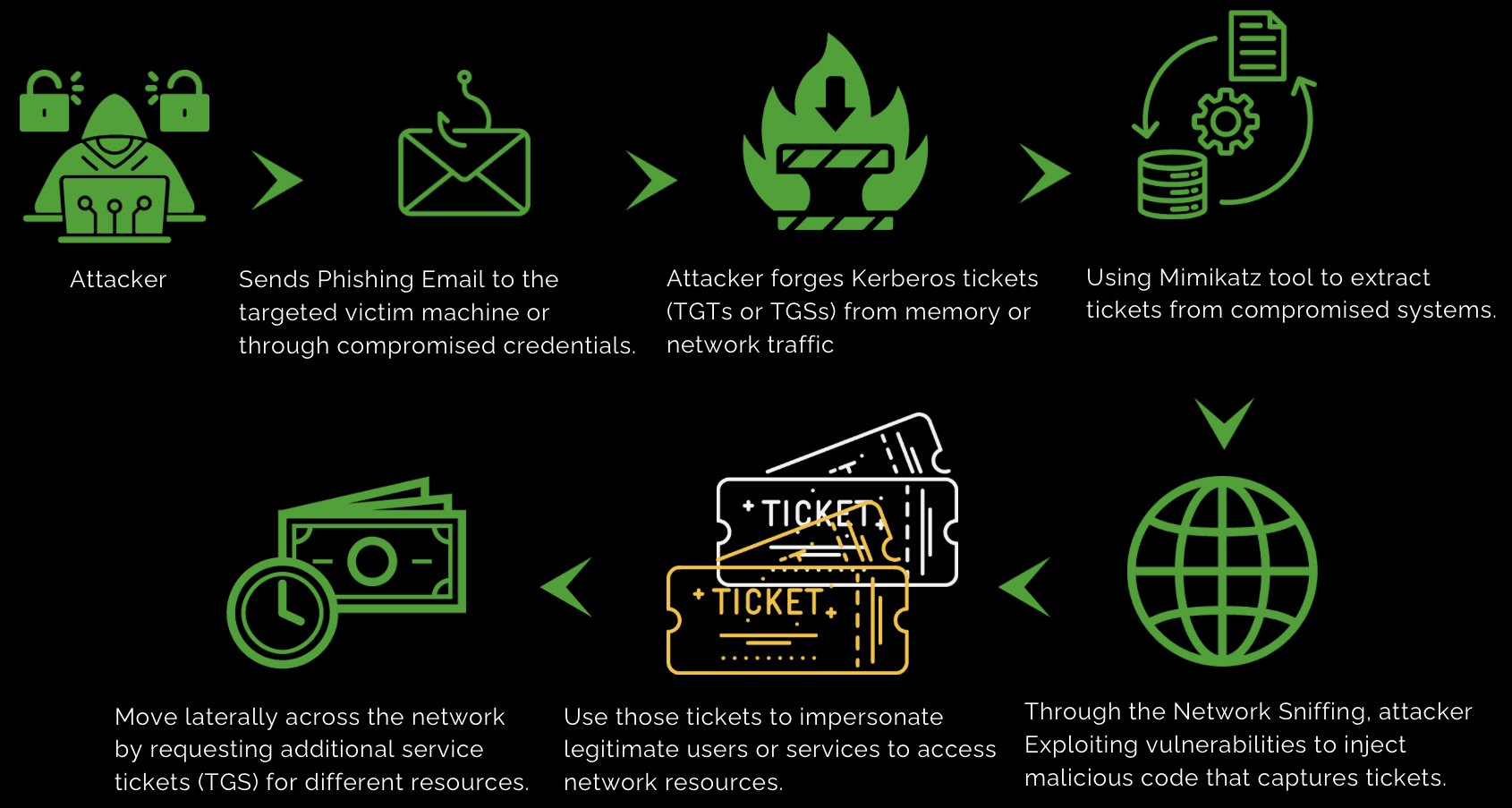
Attack Lifecycle:
Initial Access:
Attackers gain initial access through methods such as phishing, exploiting system vulnerabilities, or using compromised credentials.
Ticket Theft or Forgery:Attackers steal or forge Kerberos tickets (TGTs or TGSs) using various techniques:
Memory Exploitation:
Using tools like Mimikatz to extract tickets from compromised systems.
Network Sniffing:
Intercepting Kerberos traffic to capture tickets.
Injection Techniques:
Exploiting vulnerabilities to inject malicious code that captures tickets.
Ticket Reuse:
With stolen or forged tickets, attackers can:
Access Resources:
Impersonate legitimate users or services to access network resources.
Lateral Movement:
Move across the network by requesting additional service tickets (TGS) for different resources.
Behavioral Anomalies:
Monitor for unusual behavior that may indicate a PtT attack:
Unusual Ticket Requests:
Abnormal frequency or timing of Kerberos ticket requests.Unauthorized Access Patterns:
Access to sensitive resources or systems outside normal user or service behavior.
Useful Event IDs to Detect Pass-the-Ticket (PtT) Attack:
The Pass-the-Ticket (PtT) attack exploits Kerberos by reusing stolen or forged tickets for unauthorized access to network resources, enabling lateral movement and data access without user credentials. Detection requires monitoring key event IDs and understanding Kerberos operations. Organizations can mitigate risks with detailed logging, anomaly detection, and strict access controls. Proactive security measures are essential to protect Active Directory environments from PtT attacks.
Happy Learning !!


