The Black Basta ransomware group first appeared in early 2022, quickly gaining attention due to its use of double extortion tactics. This involves not only encrypting victim data but also stealing sensitive information, which is threatened with public release unless a ransom is paid. The group's rapid expansion, targeting at least 20 victims within its first two weeks, suggests a high level of experience and a well-established method of gaining initial access to networks.
There are suspicions that Black Basta may be a rebrand or successor of the Conti ransomware group, a notorious Russian-speaking cybercriminal organization. Black Basta shares many tactics, techniques, and procedures (TTPs) with Conti and other related groups, such as BlackMatter. Unlike other cybercriminal groups that recruit publicly on dark web forums, Black Basta tends to operate more discreetly, making it harder to trace or disrupt.
How does it work?
Black Basta typically gains access through phishing emails that appear to be from reputable sources, such as invoices, shipping notifications, or system alerts. These emails often contain malicious attachments (e.g., .PDF or .DOCX files) or links that, when opened or clicked, download malware like Qakbot (QBot), Emotet, or other types of initial access malware, allowing the group to infiltrate the victim's network.
Unlike many other cybercriminal groups, the group employs a wide range of tools and remote access methods. Some of the most commonly used tools by Black Basta include Qakbot (also known as QBot), SystemBC, Mimikatz, Cobalt Strike, and Rclone.
Common Tactics, Techniques, and Procedures (TTPs):
Initial Access: Black Basta gains entry through malicious links or attachments in phishing emails.
Lateral Movement: Once inside, the group uses tools like Mimikatz and Cobalt Strike to move laterally through the network.
Exfiltration: Sensitive data is stolen and may be threatened with public release as part of a double extortion tactic.
File Encryption: The group encrypts key files, typically appending the .basta or .basta2 extension.
Ransom Demand: A ransom note is delivered, demanding payment in cryptocurrency in exchange for decryption or to prevent data leaks.
Post-Payment: If the ransom is paid, the victim may receive decryption keys or the stolen data may be leaked as threatened.
Attack Life-Cycle:
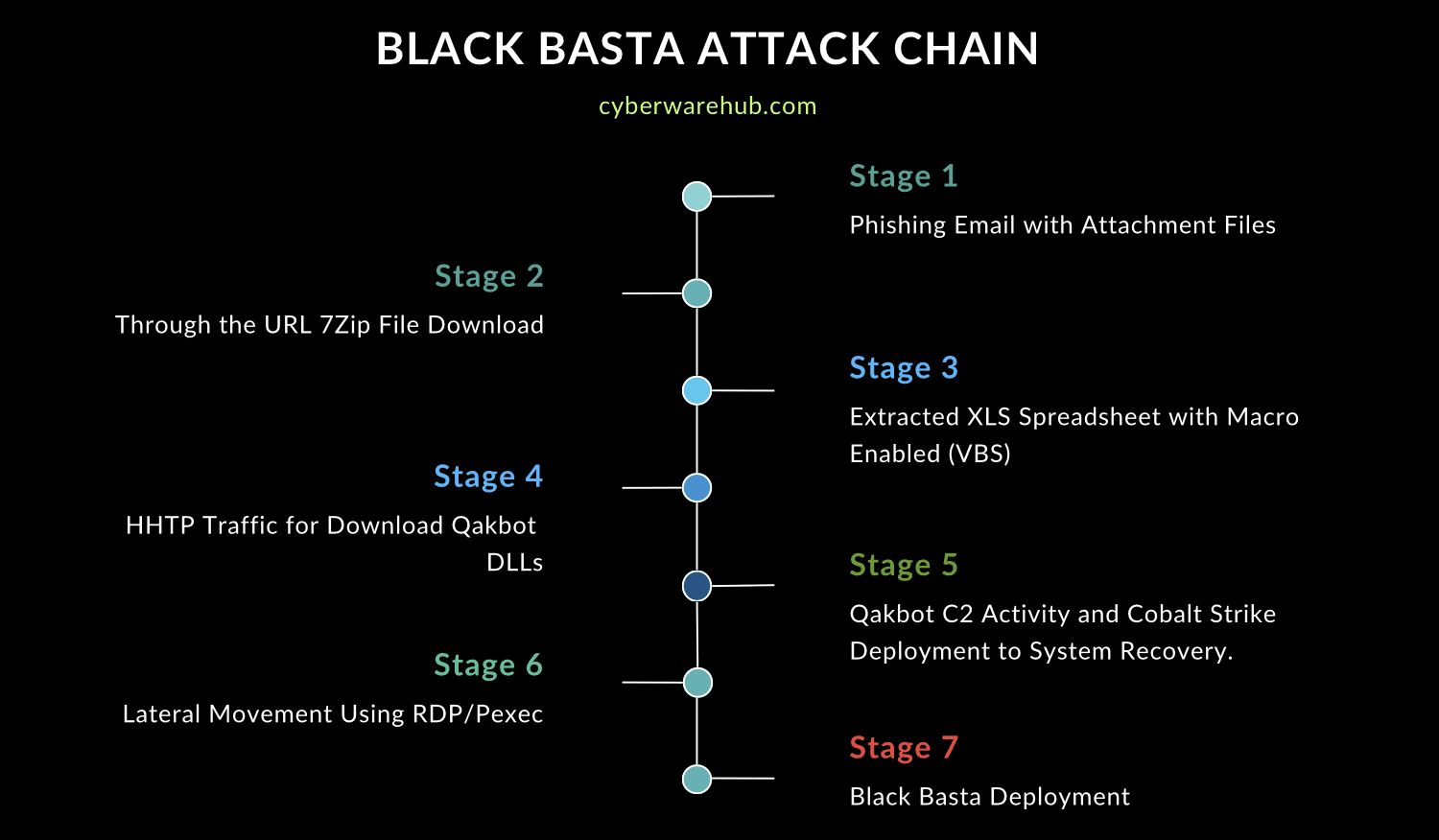
When Black Basta infects a system, files may become encrypted and show a new extension (e.g., .basta or .basta2), or they may become completely inaccessible, displaying error messages when attempting to open them. The malware often changes the system's wallpaper, and files on the desktop may become encrypted and unusable. A ransom note is typically placed on the desktop or in various folders, signaling a ransomware attack. This note contains instructions for ransom payment, usually demanding cryptocurrency. If Black Basta exfiltrates data, you may notice a sudden increase in network activity or unusual outgoing traffic to unfamiliar IP addresses, particularly if the group uses tools like Rclone to transfer stolen data.
Additionally, Black Basta is known to exploit insecure and vulnerable Remote Desktop Protocol (RDP) configurations to gain initial access.
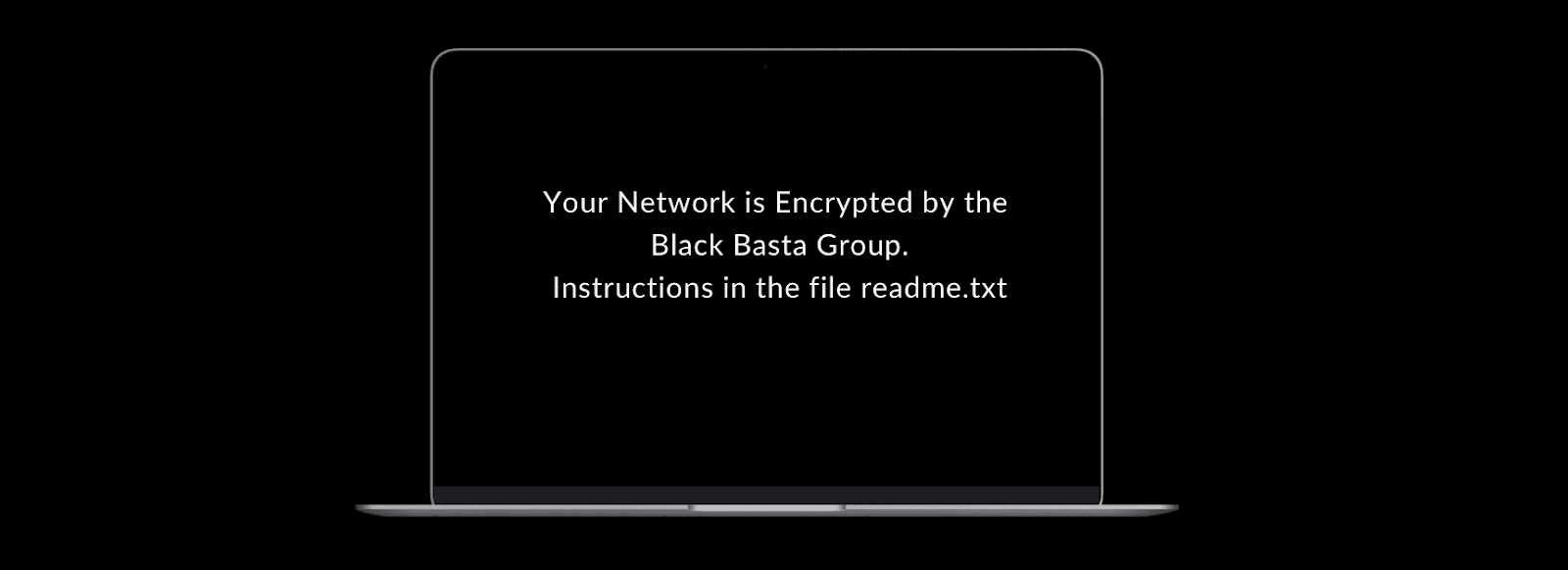
Sample Black Basta Ransomware Note:
Conclusion:
In conclusion, Black Basta is a dangerous ransomware group that employs double extortion, encrypting files and stealing sensitive data to demand ransom. It typically gains access through phishing emails and exploits vulnerabilities in Remote Desktop Protocol (RDP). Victims face severe disruption, with encrypted files and ransom demands for both decryption and to avoid data leaks. Due to its evolving tactics and use of advanced tools, Black Basta remains a significant threat. Organizations must implement robust security measures, including securing RDP and enhancing email defenses, to mitigate the risk of attack.
Happy Learning !!


