Wireshark is a popular network protocol analyzer, which facilitates users to capture and navigate the traffic within a computer network. It provides hands-on experience with real-world network traffic analysis, offering interactive browsing of data packets that provide intricate details on network protocols, packet headers, and payload content. Widely utilized for network troubleshooting, protocol development, and security auditing, Wireshark serves as an invaluable asset in network management and analysis.
Wireshark's Initial User Interface (UI):
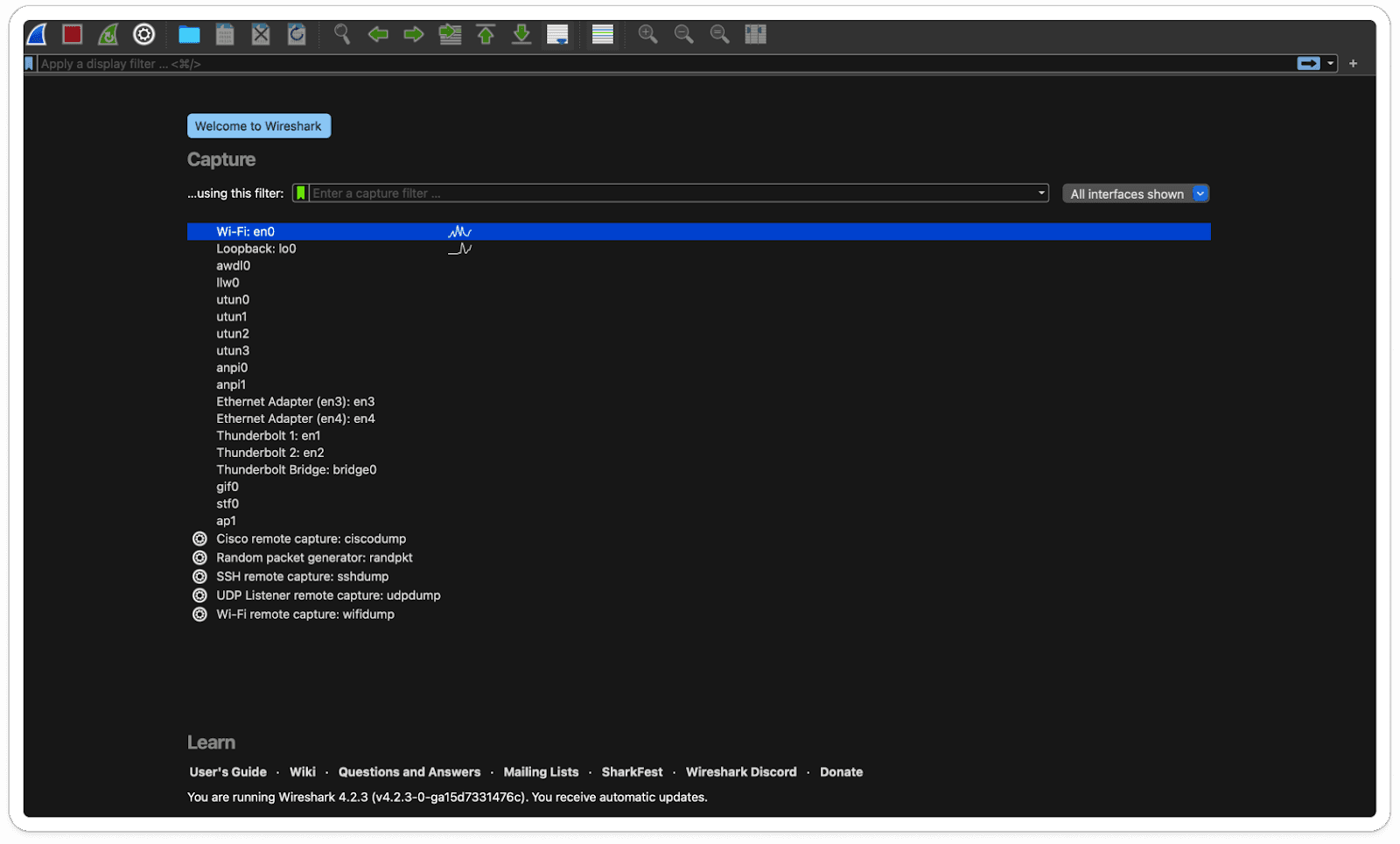
Latest Releases: [4.2.3]
Components of Wireshark:
Capture Engine: Captures network traffic from different interfaces.
Capture Options: Allows configuration of capture settings like filters and file formats.
Display Filters: Filters and displays packets based on specific criteria like protocol or source/destination address.
Packet Analyzer: Analyzes captured packets, providing insights into protocols, headers, and payload.
Packet Details Pane: Displays detailed information of selected packets, including hexadecimal and ASCII representations.
Packet List Pane: Lists captured packets with summary information such as packet number and protocol.
Protocol Support: Supports a wide range of network protocols for comprehensive analysis.
Statistics Tools: Offers various analysis tools for interpreting network traffic patterns and performance metrics.
To view all these components, we must select and click on each one individually.
Statistics of Wireshark Component:
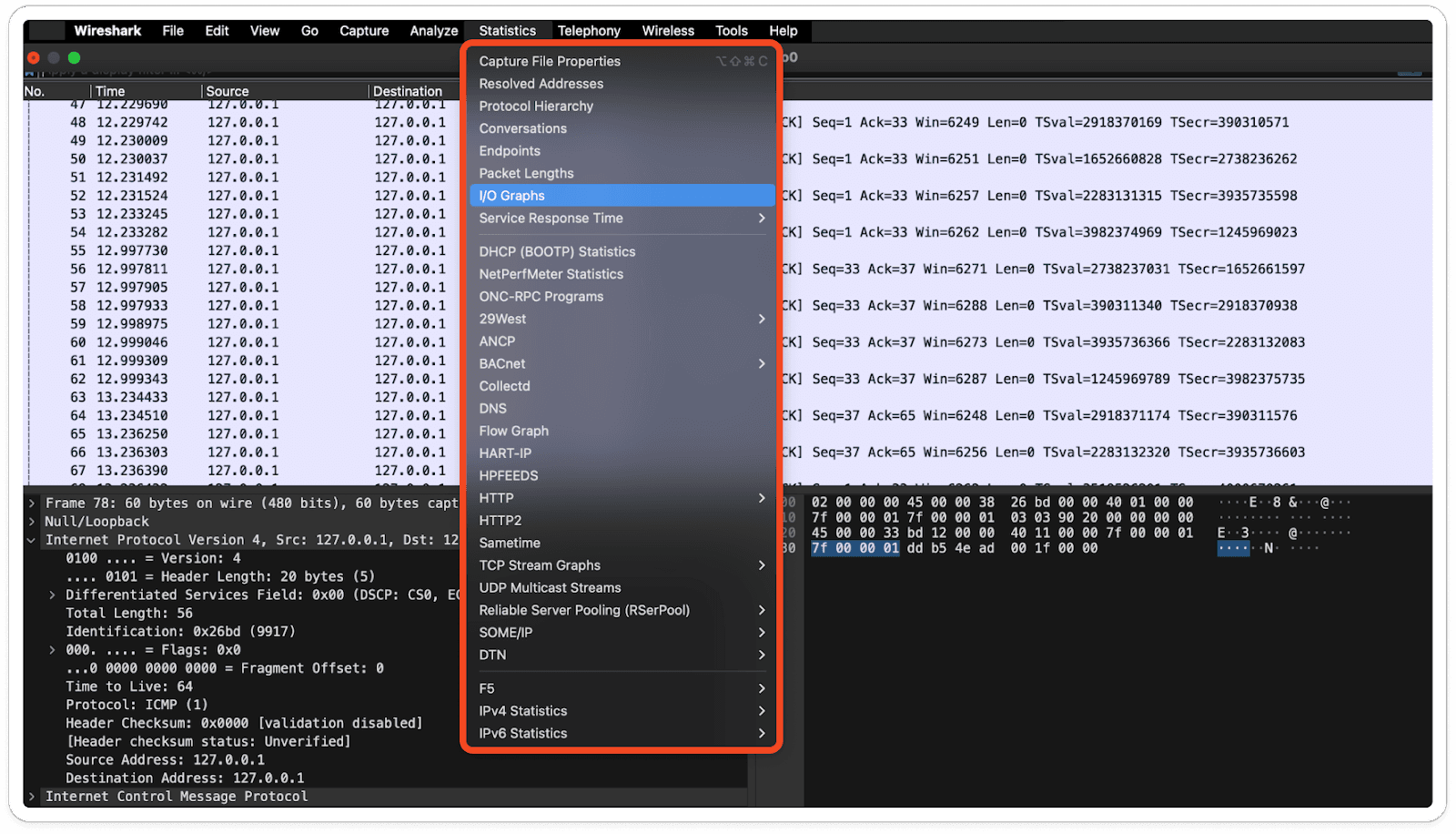
Use Cases of Wireshark:
Network troubleshooting: Wireshark helps diagnose and resolve network issues by capturing and analyzing network traffic. It can identify problems such as network congestion, packet loss, and misconfigurations.
Protocol development and testing: Developers use Wireshark to create and test network protocols. By analyzing captured packets, they can ensure that protocols function correctly and comply with standards.
Security Analysis and Monitoring: Wireshark detects and investigates security threats such as malware infections, unauthorized access attempts, and suspicious network activity. It identifies unusual patterns or behaviors indicating security breaches.
Network Performance Monitoring: Wireshark monitors performance metrics like bandwidth utilization, latency, and packet loss. It assists administrators in optimizing network resources and identifying areas for improvement.
Forensic Analysis and Incident Response: In digital forensics investigations, Wireshark captures and analyzes network traffic to reconstruct events, gather evidence, and pinpoint the source of security incidents or breaches.
Application Analysis and Debugging: Wireshark captures and analyzes network traffic generated by specific applications, assisting developers in debugging application issues and enhancing performance.
How to capture the network traffic?
Open Wireshark.
Select the network interface you want to capture traffic from.
Click on the "Start" or "Capture" button to begin capturing traffic.
Wireshark will display captured packets in real-time.
Stop capturing by clicking "Stop" or "Capture" again.
Analyze the captured traffic using Wireshark's tools and features.
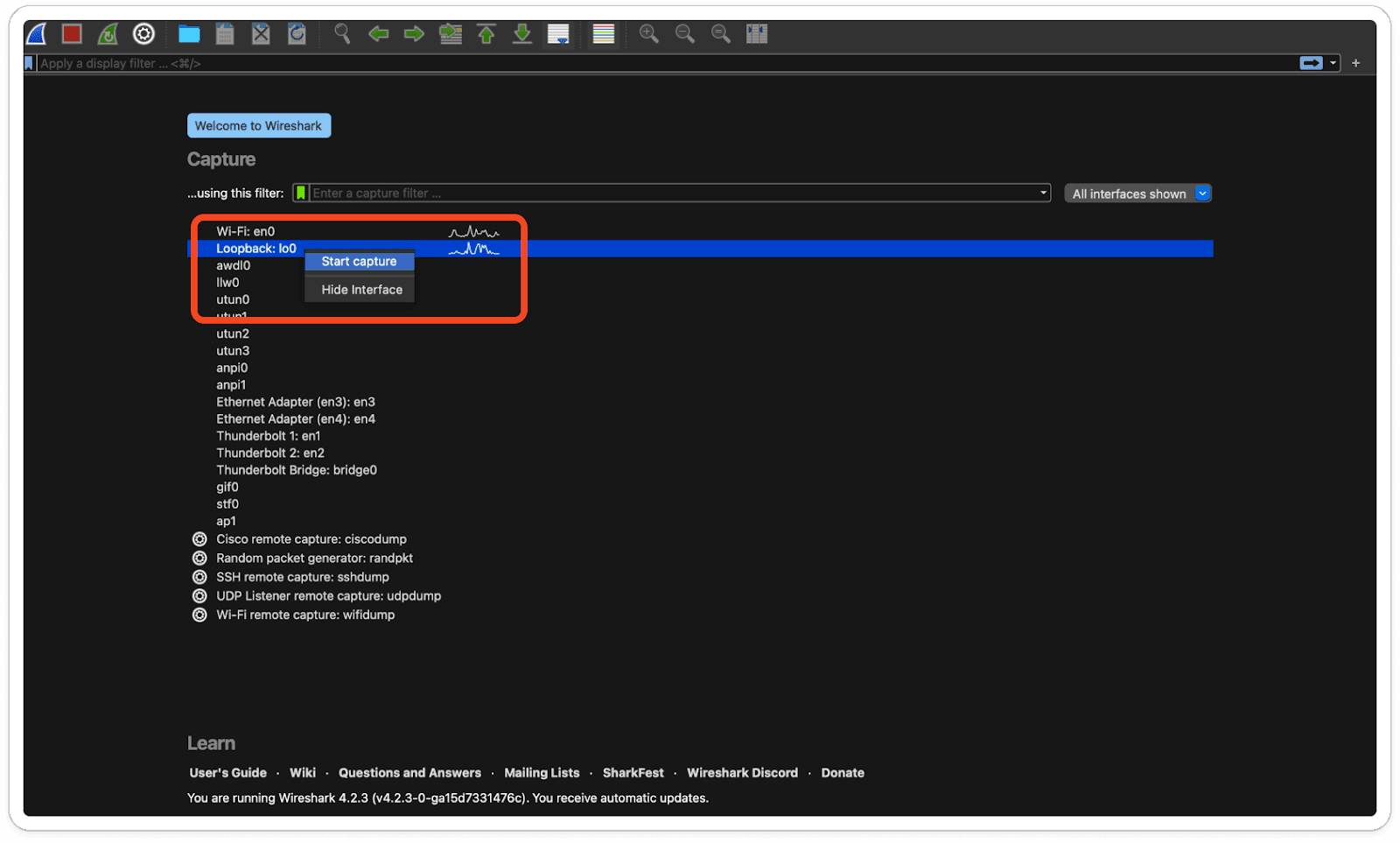
Select Loopback Traffic:
Here, I've chosen to capture Loopback traffic to capture network packets.
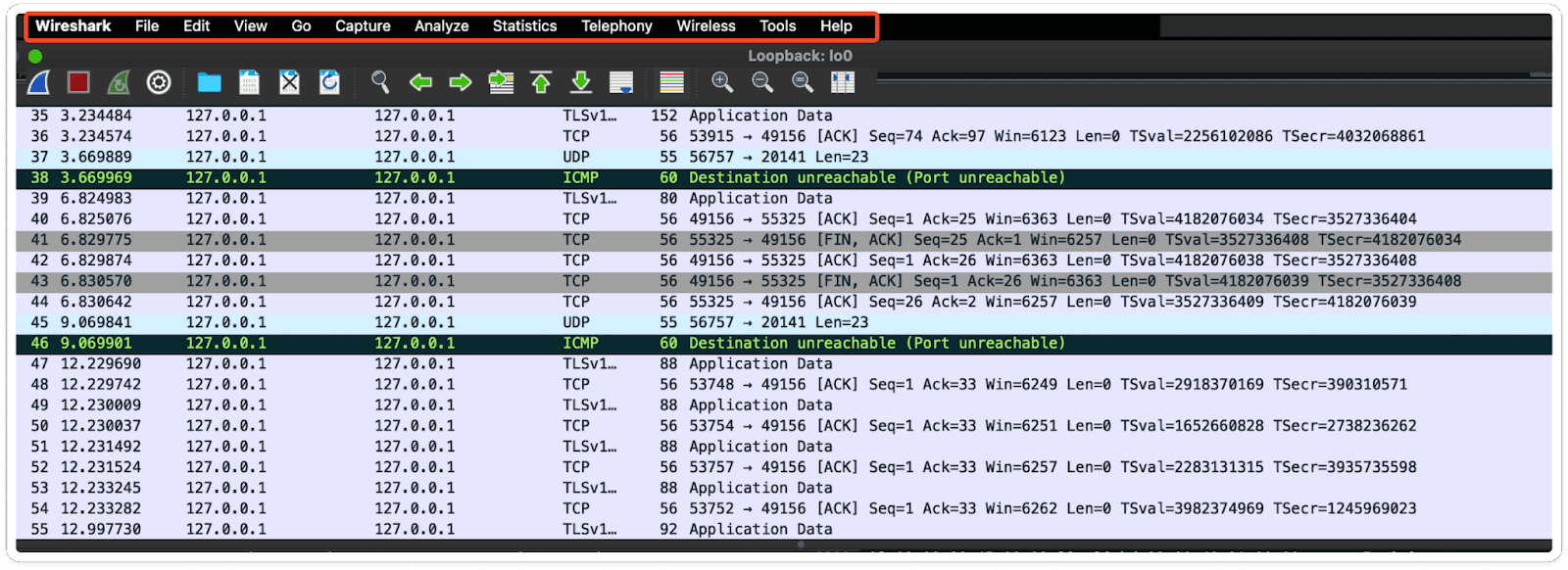
Captured Local Loopback Traffic:
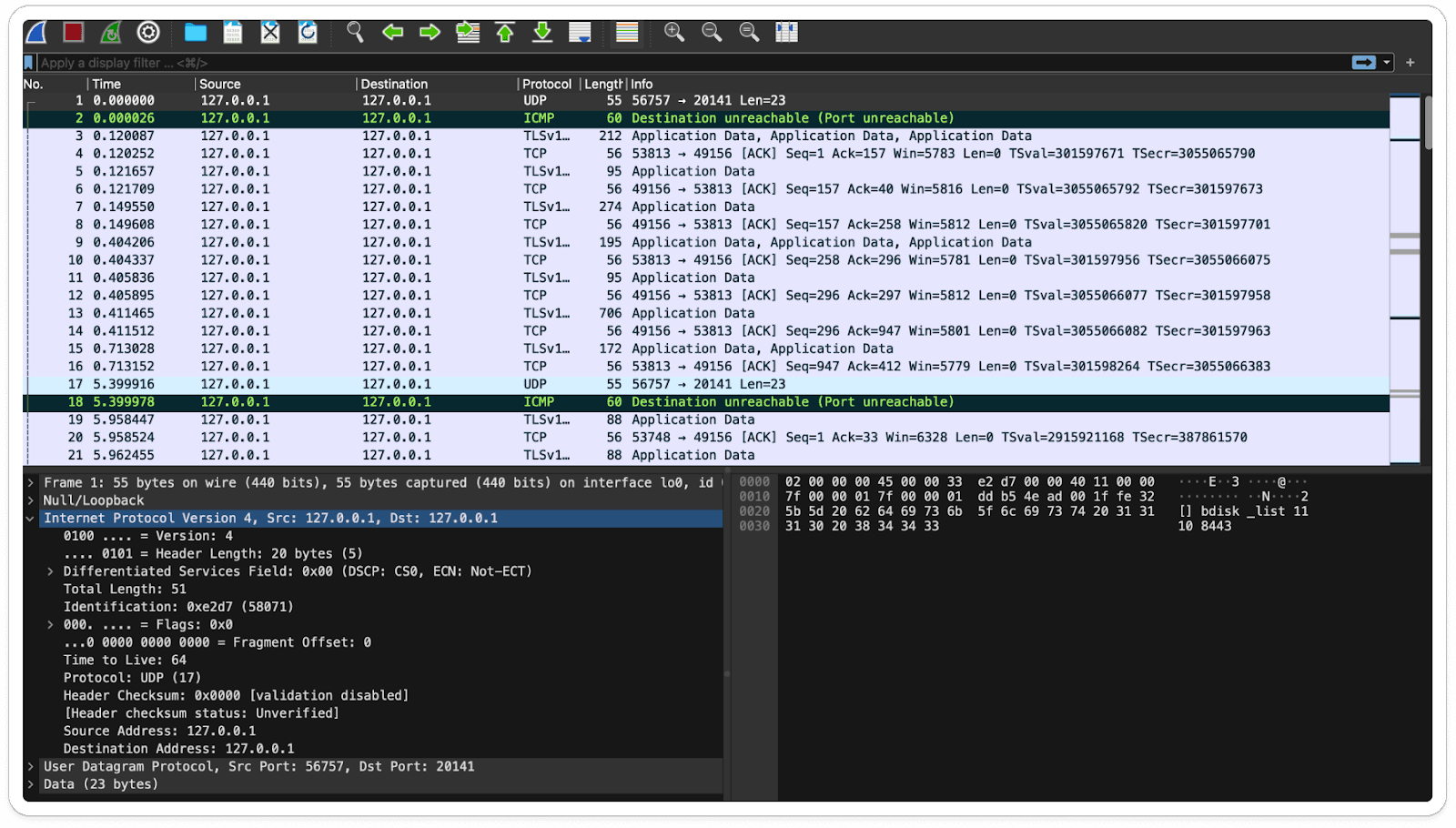
Based on the captured traffic, we can observe the type of protocol and its associated information.
Here info is "Destination unreachable (Port Unreachable)" which states that the ICMP (Internet Control Message Protocol) message signifying that a packet couldn't reach its destination due to the unavailability or inaccessibility of the destination port on the target host. This typically happens when trying to connect to a port that isn't open or isn't accepting incoming connections on the target device.
Similarly, at the bottom of the captured frame, we can view the raw data. During the analysis of an unfamiliar file, we may encounter suspicious traffic. This becomes evident with regular hands-on experience.
Happy Learning !!!


