In our Xeno-RAT Part 1, we focused on analyzing how the malware initially spread using LNK files. However, due to increased detection by antivirus (AV) vendors blocking this method, the malware authors have adapted their tactics. They now distribute Xeno-RAT through Microsoft Excel (XLS) spreadsheets, likely exploiting vulnerabilities or using macro-based techniques to deliver and execute the malicious payload. This shift underscores the malware's evolving strategy to bypass security measures and highlights the ongoing challenge of defending against such sophisticated threats in cybersecurity.
File Details:
Infection Chain:

Analysis of Xeno-RAT:
Following the infection chain, the malware author sends phishing email attachments to targeted victim machines. The email prompts users to open an XLS file, which appears blurred, forcing them to enable Macros to view its content. Once Macros are enabled, VBA macros execute and download the payload file to the %Appdata% folder, hiding malicious activity.
The Appdata is a directory on Windows systems where user-specific application data, settings, and caches are stored, crucial for application functionality and user customization. As mentioned earlier, when analyzing non-PE MS Office files, it's necessary to extract the archive as it often contains multiple bundled files.
Extraction of XLS file:
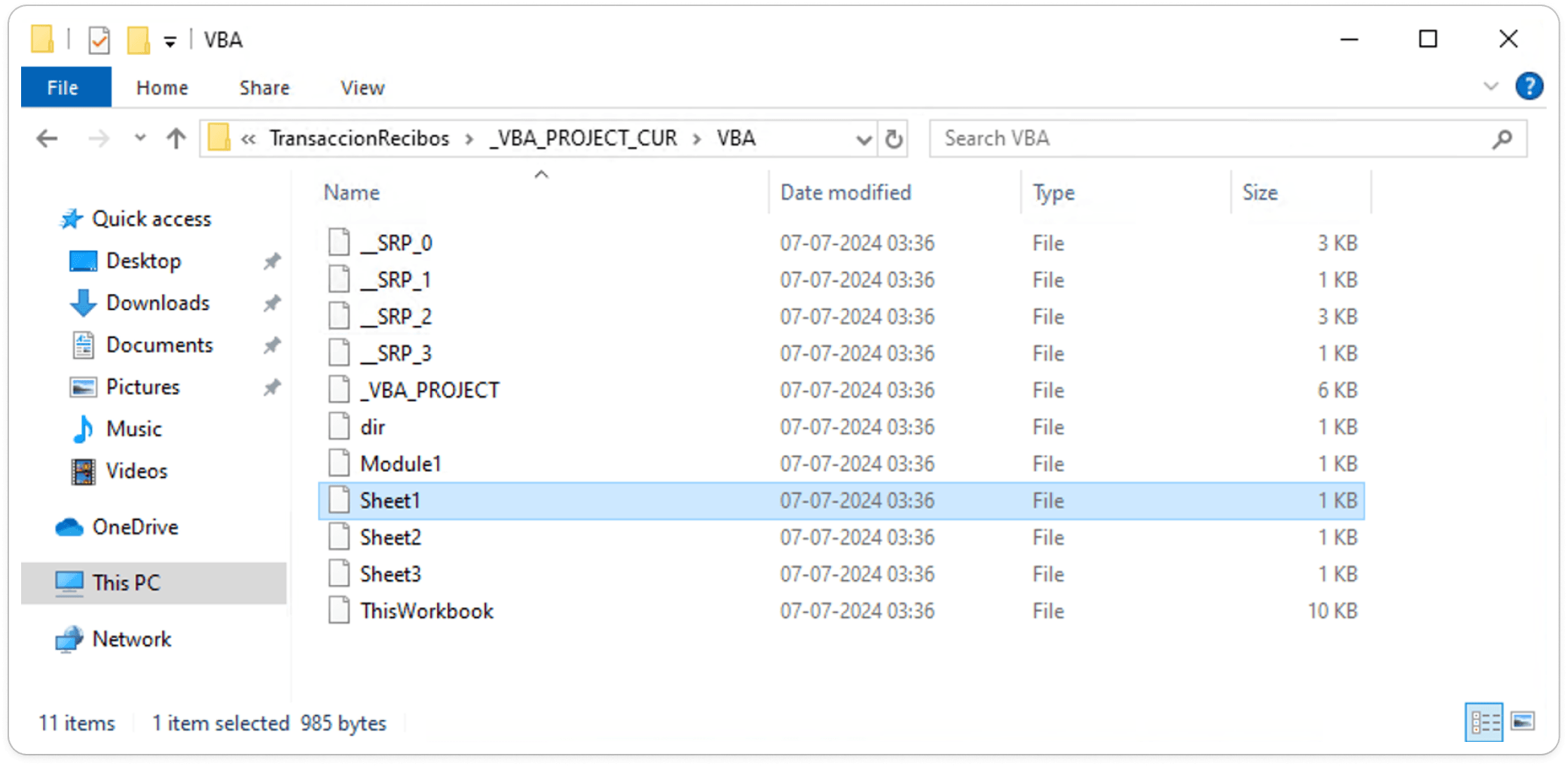
Here's the extracted XLS file, containing bundled files such as VBA_Project, Sheets, and the Workbook.
This Workbook:
In Microsoft Excel, a Workbook is the main document that holds multiple worksheets or spreadsheets, central to organizing and managing data within the application.
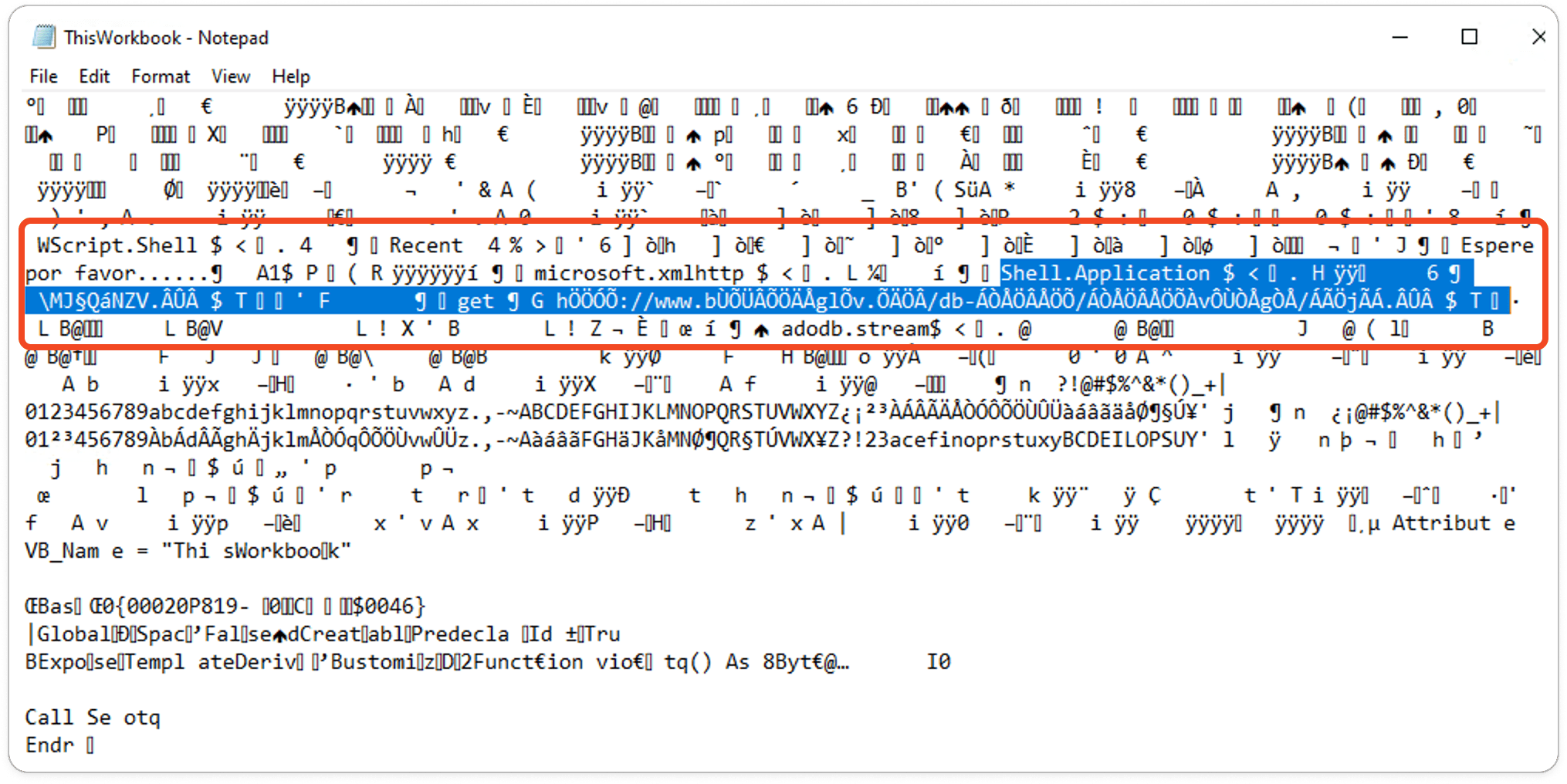
Here in this workbook, you'll find an embedded Windows PowerShell executable. When executed, it triggers the Shell Application, which is used to fetch an obfuscated URL. This URL typically leads to a malicious website or downloads additional payloads onto the system. This technique is commonly used in phishing campaigns to conceal malicious activities and initiate further exploitation of the compromised system.
_VBA_project:
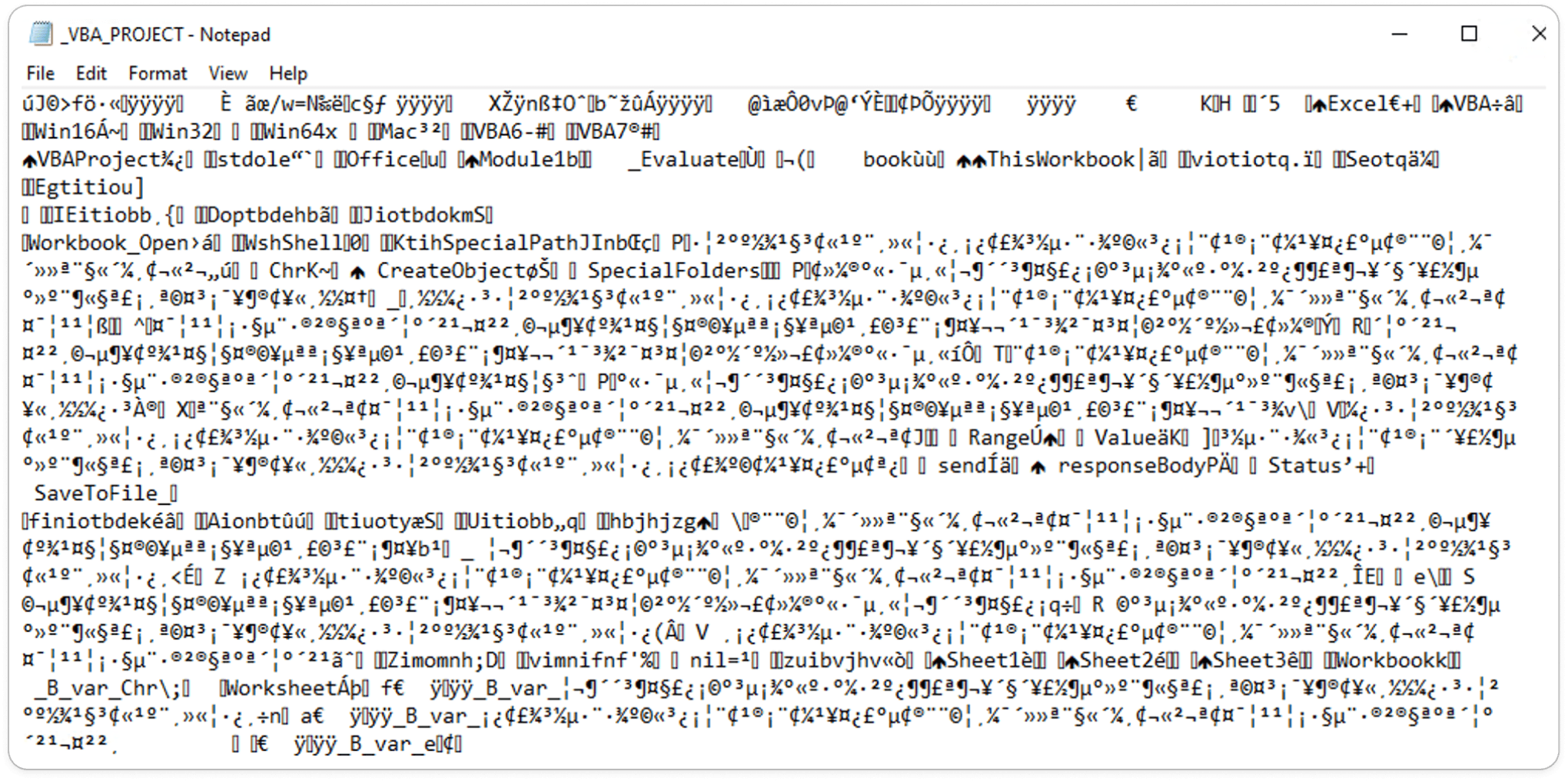
VBA_Project is the section within a Microsoft Office file where Visual Basic for Applications (VBA) macros, modules, and code are stored, defining the document's automation and functionality. Here, it appears encrypted, displaying as obfuscated strings.
Xeno-RAT XLS Template:
This is the actual view of the XLS file, triggering a Security Alert due to disabled Macros. If you trust the source, enable Macros to proceed with observing packet transfers for further analysis.
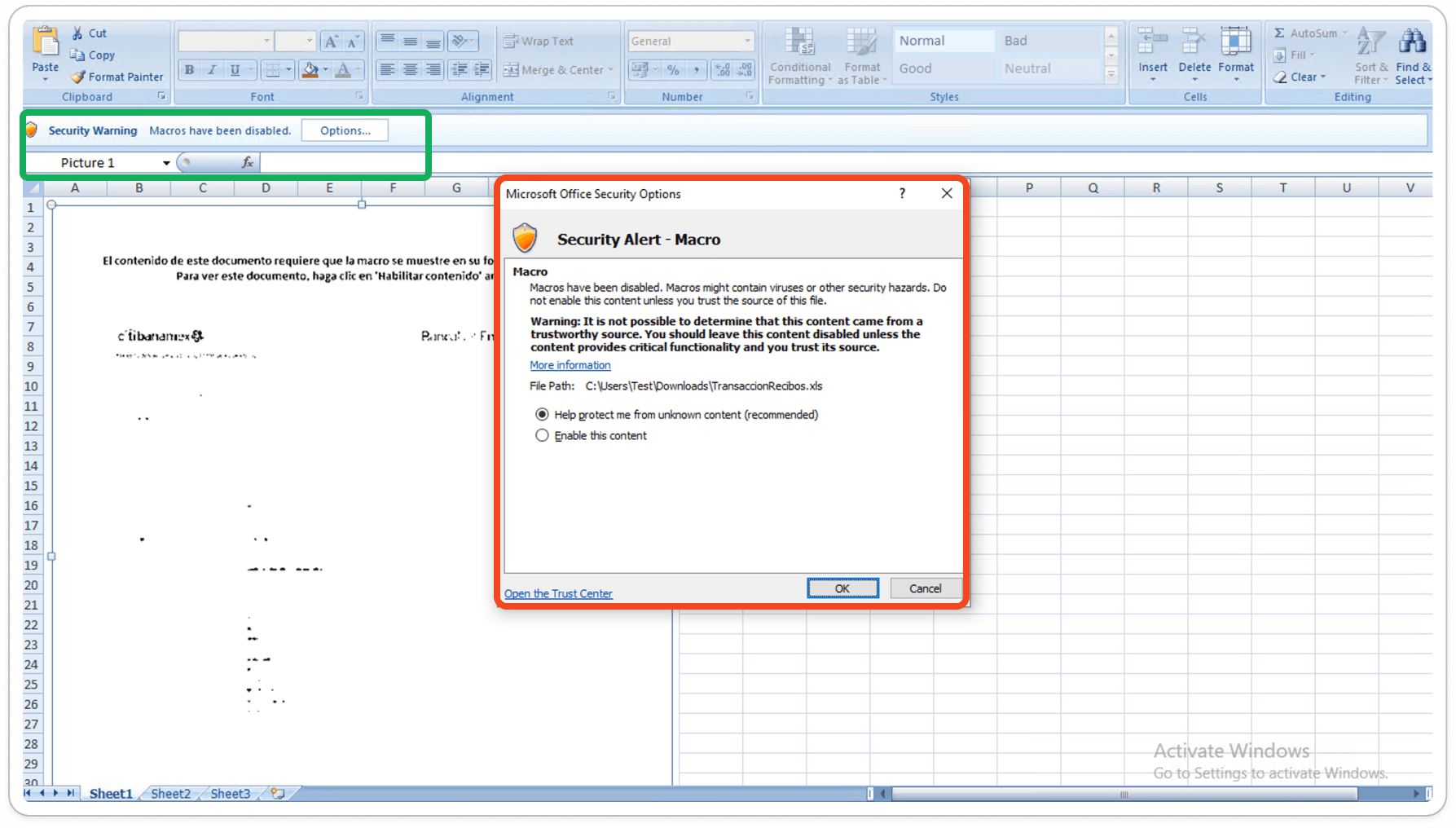
Macro-Enabled XLS Sheets:
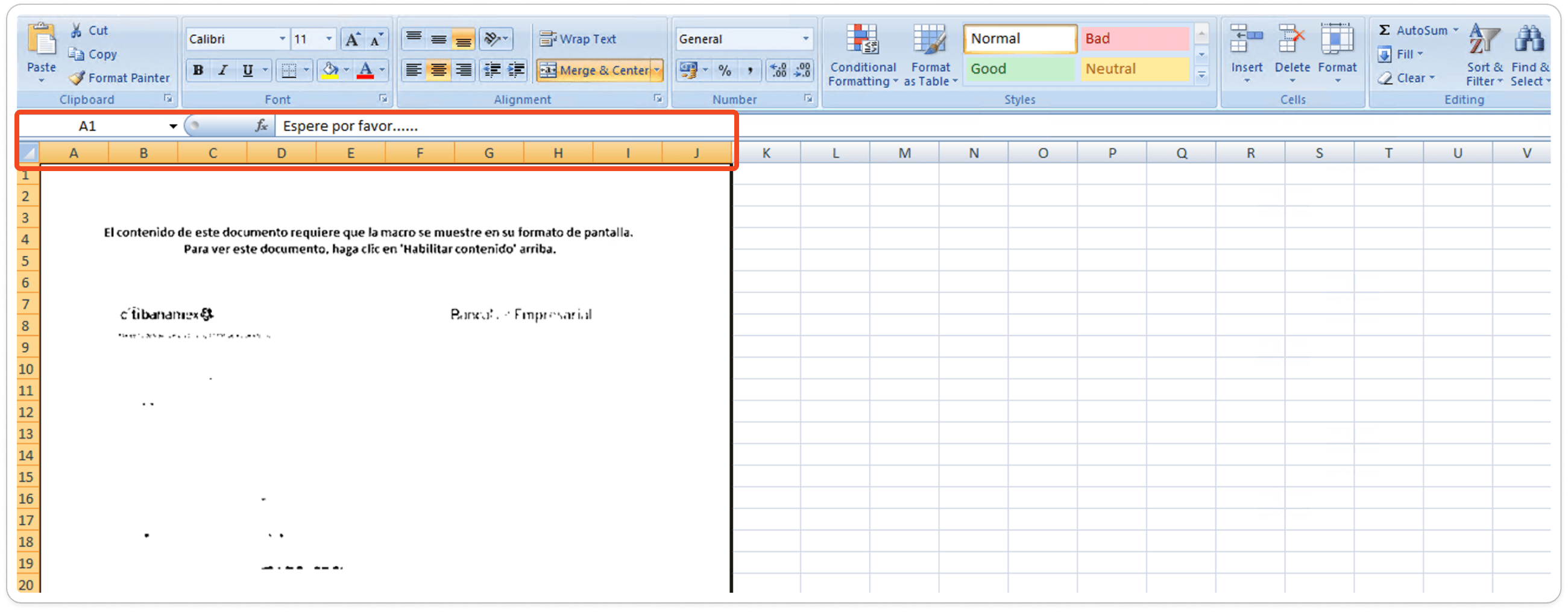
After analysis, I found that while selecting all the sheets, it's showing one Spanish word "Espere por favor.." which states that "Please Wait".
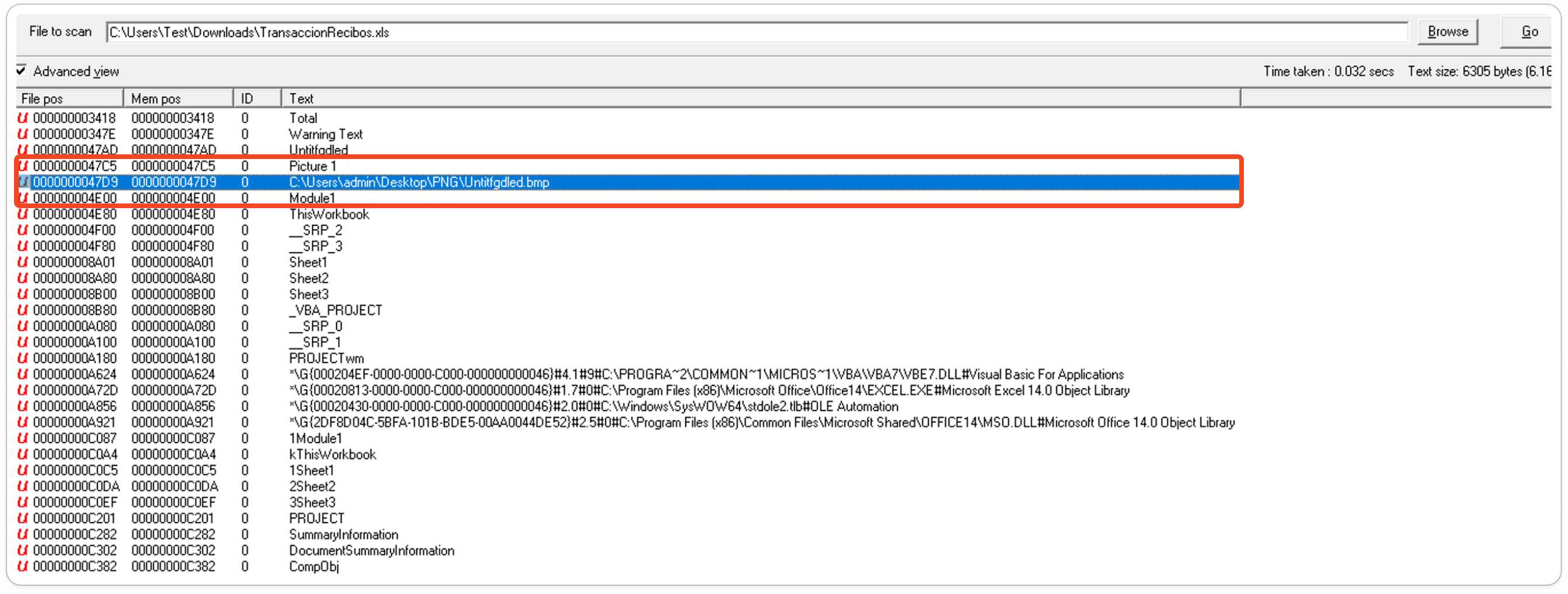
Based on the obfuscated strings, the macro defines an Auto-Open function that executes code when the workbook is opened. This function first creates objects for "WScript.Shell", retrieves the path to the "Recent" folder, and constructs a file path by appending "\\MJ\u00a7Q\u00e1NZV.\u00c2\u00db\u00c2" to it. It then creates an "adodb.stream" object and another one for "microsoft.xmlhttp".
Here, it saves the response body to the previously constructed file path if the request is successful. Finally, the macro uses "Shell.Application" to open this file. The characters with hexadecimal representation like `\u00b7` are obfuscated and need further analysis.
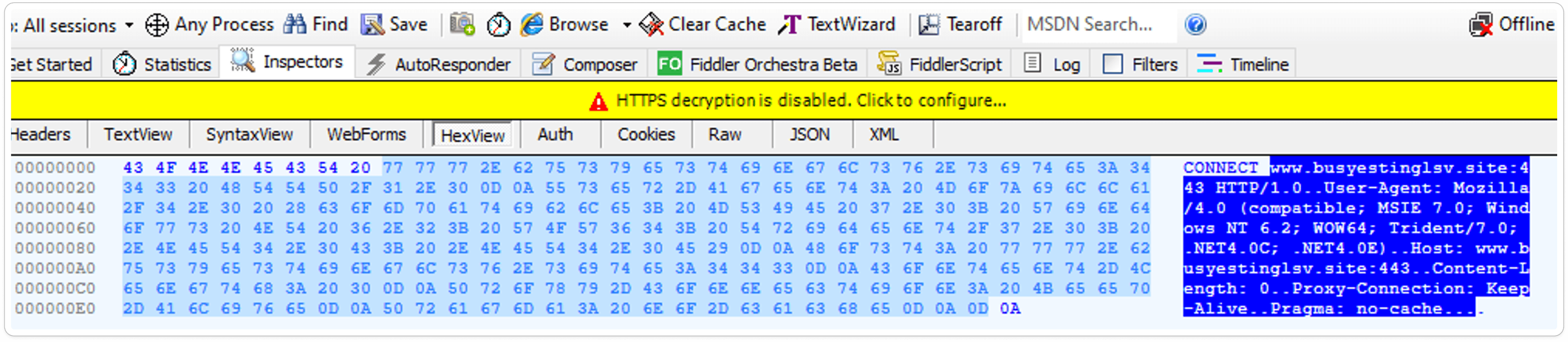
Captured HTTP Packet:
AV Vendors Verdicts for the obtained URL:
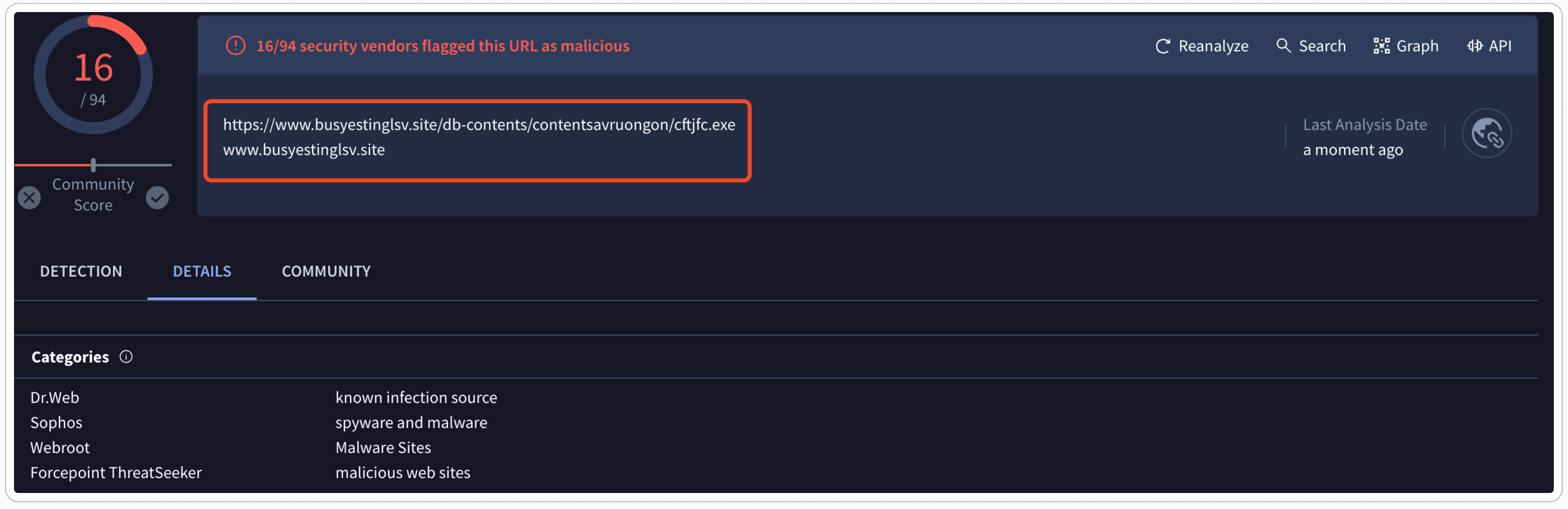
Analyzing sandbox results enables us to know whether the URL is associated with malware, phishing attempts, or other malicious activities. Here the obtained URL is marked as 100% malware.
MITRE ATT@CK MATRIX:
Happy Hunting !!